A Nigerian cyber criminal gang has been uncovered after a short investigation. A client recently came to us with a phishing campaign that was targeting their organisation. After some initial research, it was clear that the campaign had been going on for over two years and was primarily targeting academic institutions.
Further investigation revealed that threat actors were using IM Creator under the domain http://imxprs.com, a free website builder and hosting service, to build their malicious phishing sites. They have been using the service since 2015, and over 700 different sites have been set up during that period mostly targeting colleges and universities in the US and around the world.
Cyjax contacted the service administrators at IM XPRS to take the malicious site offline; they responded quickly and complied with our request. They were aware of the activity under their domain and have implemented countermeasures to try and curb it.
One admin told us in an email: “We take these issues very seriously and do our best to prevent them. We are trying to counter attack these sites by disabling the option to add the word ‘password’ to the contact form, but the hackers use special characters to carry it out. Also, we limited the views for free URLs to 500 a day which is enough to block a phishing URL within a couple of hours.”
Sadly, it has turned out to be a constant battle for the company and a ‘whack-a-mole’ situation for them as threat actors are successfully circumventing their countermeasures:
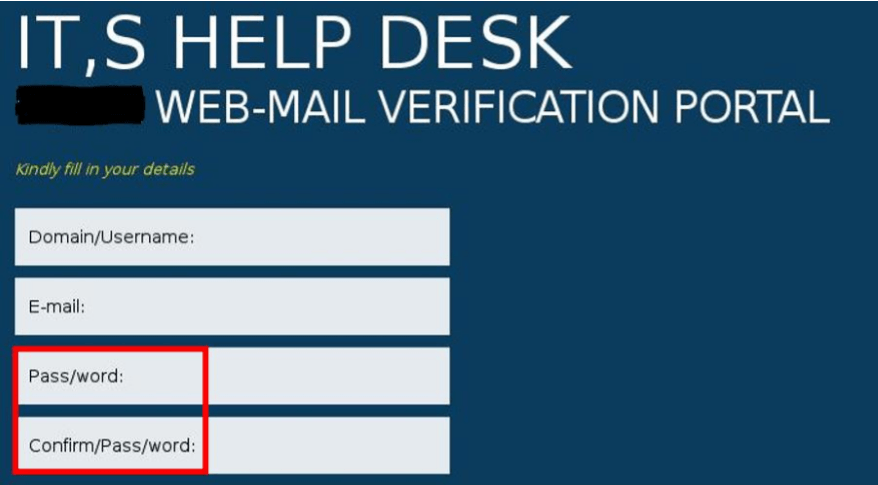
Upon examining the HTML source code, we discovered an email address that was more than likely capturing victims’ data; this was then further backed up by the site administrators as being the account owner.
Using a simple online reverse email lookup tool, we dropped the email address in and discovered that it was potentially linked to a Facebook account. Even if you lock down your email address within Facebook, which this person had, it will still link to the account.
We then spent some time looking at the account to see if we could identify any criminal activity. There was no doubt that this person was involved in some sort of fraud. It was obvious from the pictures and comments on both his account and that of his brother. They are both from Nigeria (Benin-City, Edo, Nigeria), which has a history of cyber criminal activity, including phishing and other scams.
We decided to try to get a stronger link between the man who calls himself “Young Succesful” and the email address we were given, so we sent him a message. Much to our surprise, he responded and confirmed exactly what we were looking for:
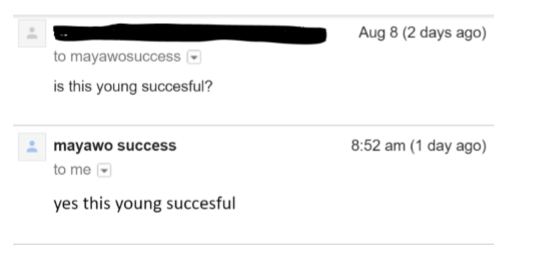
Further collaboration and corroboration served to strengthen the link. We were able to confirm that the compromised accounts were being accessed from Nigeria via our client’s Threat Management Gateway (TMG) logs. We were also able to determine that they have been using different email addresses, most of which were not traceable at all. Sometimes, it only takes one mistake to bring an entire operation down.
There has been some further evidence that the threat actors have made attempts to carry out further business email compromise in order to scam victims out of large sums of money. The following is an example email that has been distributed to those that are compromised in the first instance in order to initiate the scam:
Subject: Business Transaction
I have a profitable business transaction’s, Reply to this email:
( [email protected] ) for more details.
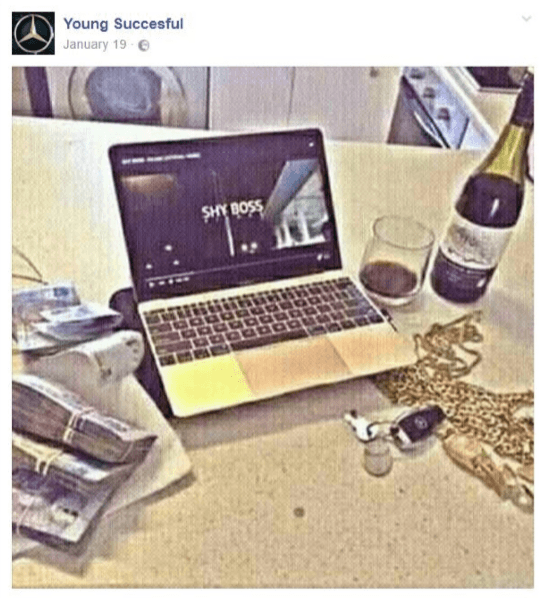
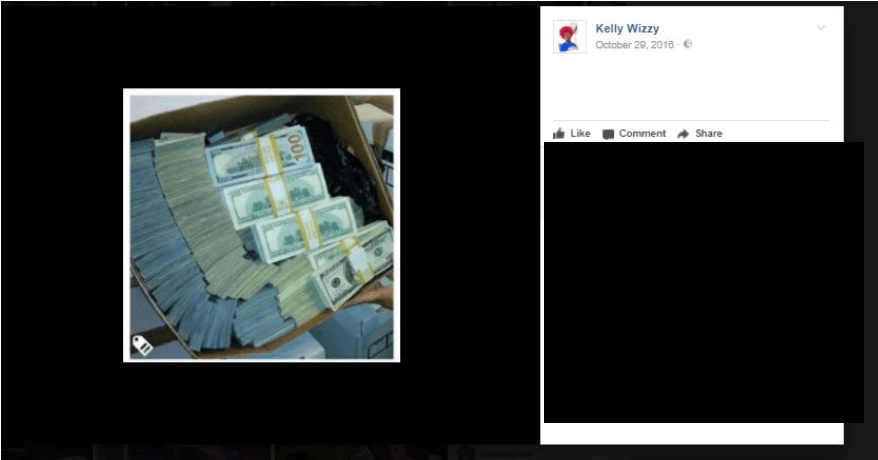
The following are some brazen posts on their social media accounts that clearly indicate fraudulent activity; they specifically talk about it openly and post shots of stacks of cash, laptops, expensive cars and jewellery:

Western Union is typically where scammers will request cash transfer: “Store wey dey change person Life” (Store that changes a person’s life)

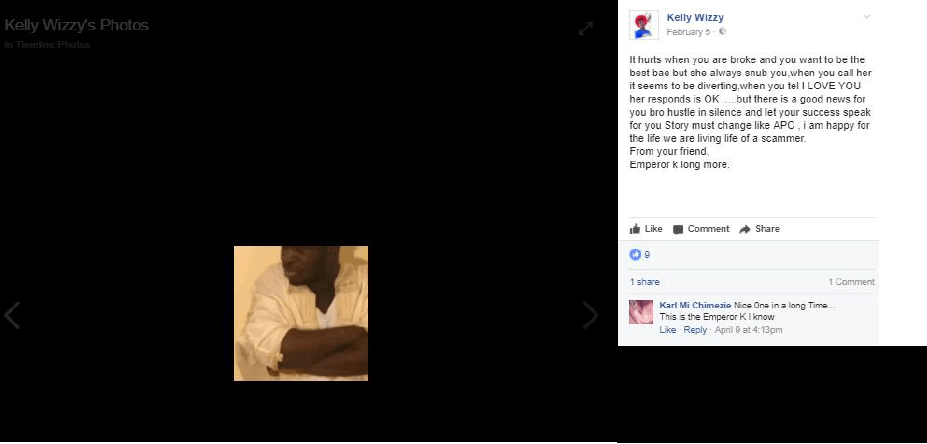
“It hurts when you are broke and you want to be the best bae but she always snub you,when you call her it seems to be diverting, when you tel I LOVE YOU her responds is OK …..but there is a good news for you bro hustle in silence and let your success speak for you Story must change like APC , i am happy for the life we are living life of a scammer.
From your friend,
Emperor k long more.”

“…no sleeping tonight hustle mood”
On 16 August, we uncovered some more information which helped confirm the link between the phishing campaign and the scam email. The perpetrator had added some work information to his Facebook profile that indicated he was the webmaster for a company called Pacific Metal Works, which is in line with the reply-to email address ( [email protected] ) in the scam (shown earlier).
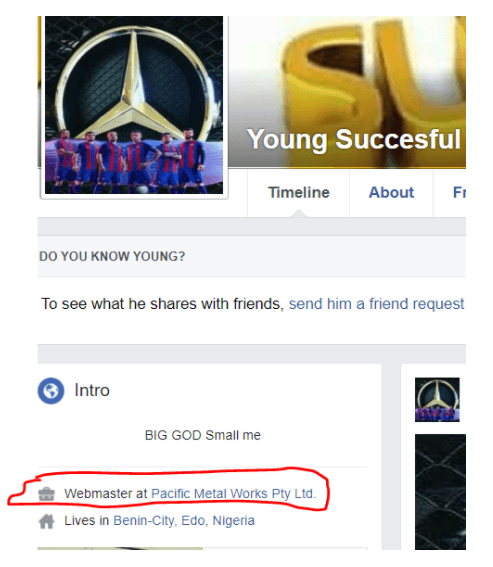
The Pacific Metal Facebook page can be found here. It is a fictitious company set up simply to be part of the scam.
Since our investigation, researchers at Check Point also uncovered a phishing campaign that was being carried out by a sole Nigerian national. These threat actors are typically not very sophisticated, but with the presence of malware-as-a-service, they are well-supported to carry out much more sophisticated and dangerous operations.

