Consumer credit reporting agency Equifax has had a turbulent few days. On Thursday night (7 September), the company released a public statement confirming it had suffered a significant data breach. From mid-May to July 2017, unidentified hackers stole personally identifiable information (PII) belonging to approximately 143 million US consumers. It included names, dates of birth, credit card numbers, Social Security numbers, addresses and some driver’s licence numbers. A smaller number of Canadian and British consumers may also have been affected.
As the news broke, questions immediately began to be asked about the company’s response to the breach. Consumers were angered that the initial statement appeared to downplay the severity of the incident. Many were also perturbed that the company’s TrustedID Premier service, offered free to potential victims, included a waiver forfeiting rights to any legal recourse over the breach.
Many commentators also questioned why it had taken more than a month to notify the public about the compromise, particularly when it was discovered that three senior personnel had dumped nearly $2 million in stock during this period. Equifax maintains that none of the executives had any knowledge of the breach when they made the sales. However, the timing is certainly suspicious and the optics are undeniably poor.
Security researchers swiftly uncovered a series of significant vulnerabilities in the company’s systems. These included ancient servers with critical security flaws that could be remotely exploited to execute arbitrary code, as well as a basic cross-site scripting (XSS) vulnerability that was still present despite being reported in 2016. Taken together, this supports claims that Equifax failed to adequately protect the integrity of their network infrastructure.
Later reports suggested the hackers may have exploited a flaw in the Apache Struts Web Framework. However, it remains unclear whether it was the vulnerability publicised earlier this month (CVE-2017-9805), or another that was patched in March (CVE-2017-5638). The distinction is clearly important: if the hackers exploited a zero-day to breach the network, Equifax cannot be held responsible for the presence of the flaw. If they declined to patch a vulnerability that was publicised in March however, that is a much more serious failing.
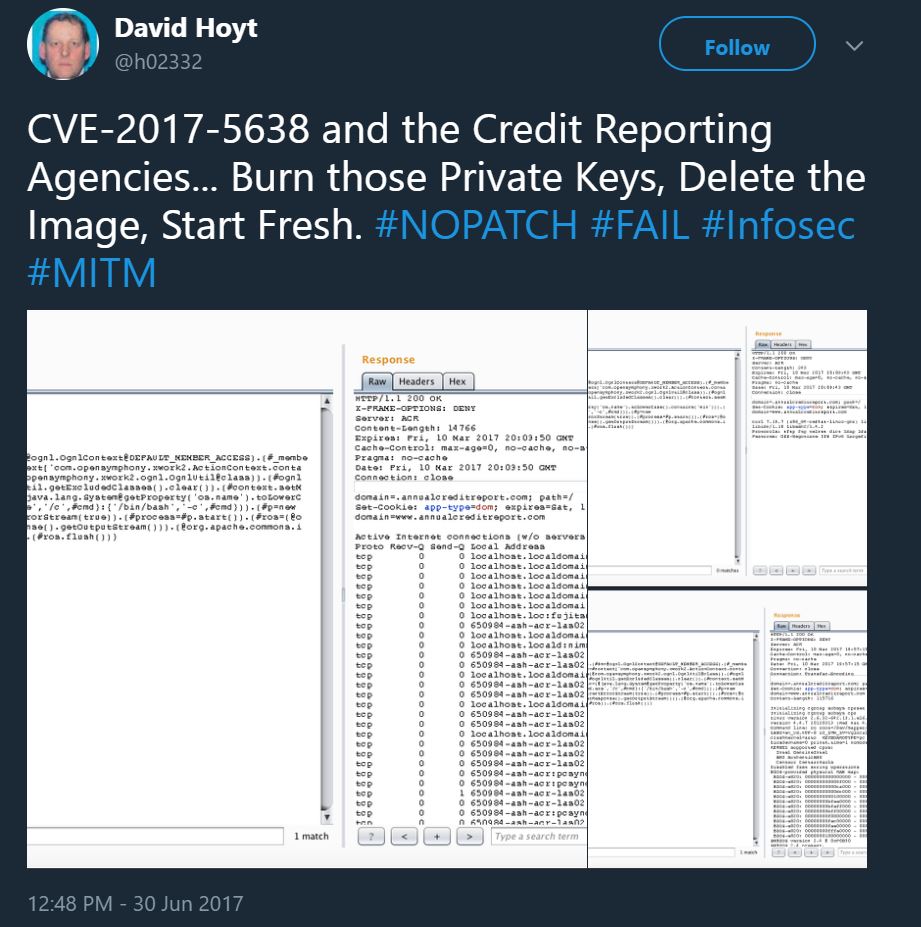
Interestingly, security researcher David Hoyt warned that “Credit Reporting Agencies” had failed to patch CVE-2017-5638 in June 2017 (see screenshot below). The website investigated, AnnualCreditReport.com, states that it is “brought to you by” TransUnion, Experian and Equifax.
Regardless, the cost to the company is likely to be severe both financially and in terms of brand damage. Shares plunged more than 13% on 8 September, with initial estimates indicating losses could total hundreds of millions of dollars, if not more. As a sign of things to come, a $68.6bn class action lawsuit has already been filed against the company. The plaintiffs argue that the breach will cause “serious risks of credit harm and identity theft for years”.[1]
While the story is still developing, so far Equifax seems to have presented a textbook example of how not to handle a major data breach. Apologetic statements issued after the fact are no substitute for investing in adequate safeguards to protect against network infiltration and data theft. As the deadline for the General Data Protection Regulation (GDPR) looms, firms will have to do more to protect confidential information. If they fail to do this, they risk potentially devastating fines and untold brand damage when threat actors ultimately test their defences, and find them wanting.

