Introduction
Over the course of three days (12 – 15 August 2019) we monitored the public submissions of three popular online sandbox services. These services allow anyone to upload a file and then generate a report about what happens when the file is opened; they then give an indication as to whether the file is malicious or benign. The services chosen all have public feeds and do not require payment in order to download or view the public submissions.
Due to the high volume of files submitted, we focused on .pdf and .msg/.eml files marked as suspicious or clean, ignoring anything marked as malicious.
Common Findings
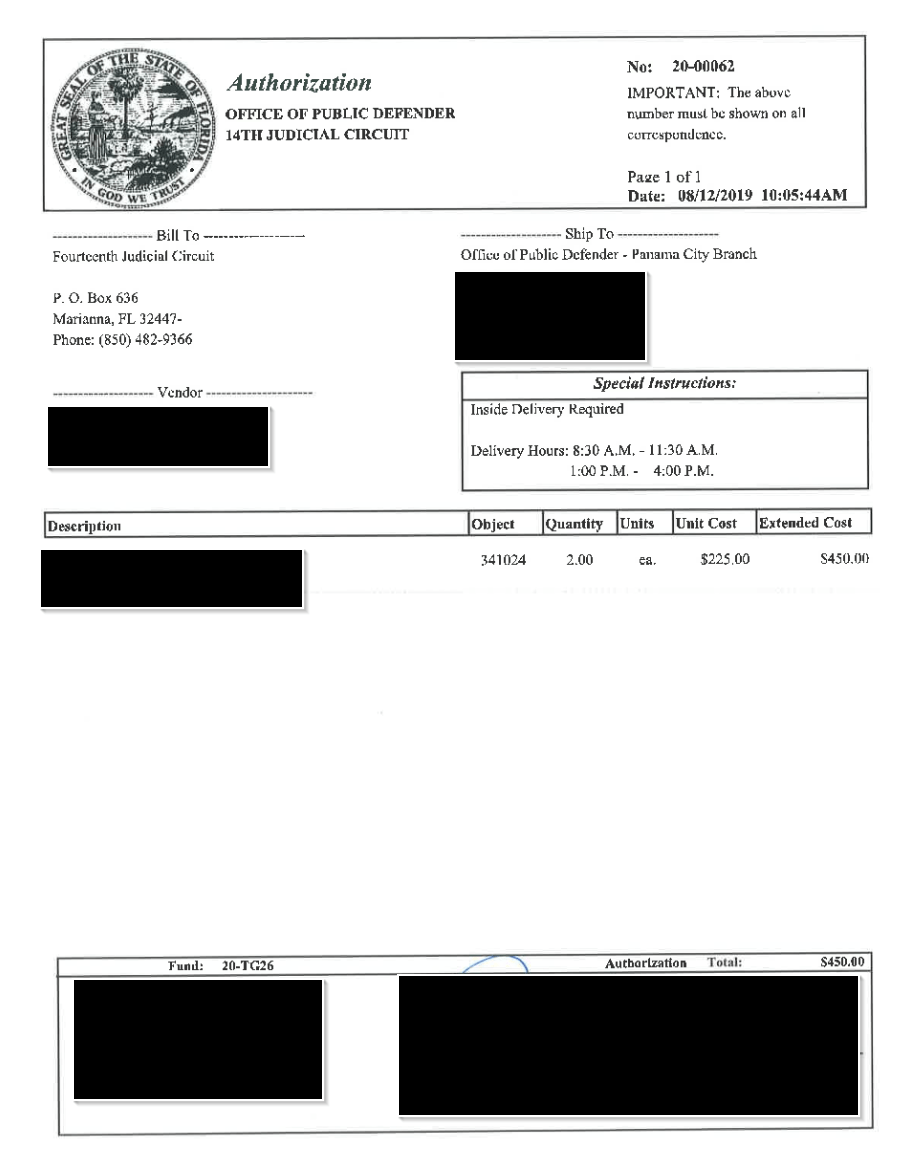
By far the most numerous benign documents were invoices and purchase orders. We collected just over 200 in three days; this was expected as these are some of the most popular document types being emailed between businesses.
In one instance, we discovered a company that appeared to be submitting all received purchase orders into the sandbox, rendering all of them public. The company in question provides a popular deployment tool for Microsoft Windows administrators and has many high profile clients, including schools and courts.
By examining the invoices, we were able to determine who was using the software, as well as the contact details of those responsible for purchasing in each organisation: this is extremely useful information for a threat actor conducting a spear phishing or BEC fraud campaign. We notified the company in question and they confirmed that they are investigating the issue.
Professional Certificates and CVs were also prevalent: we collected 30 over the three days. Many of these contained ID photographs and addresses, and two even had passport copies attached: such information could be used to impersonate the victim or steal their identity. Once again, we concluded that these documents are likely being disseminated via email and then checked for malware by office staff.
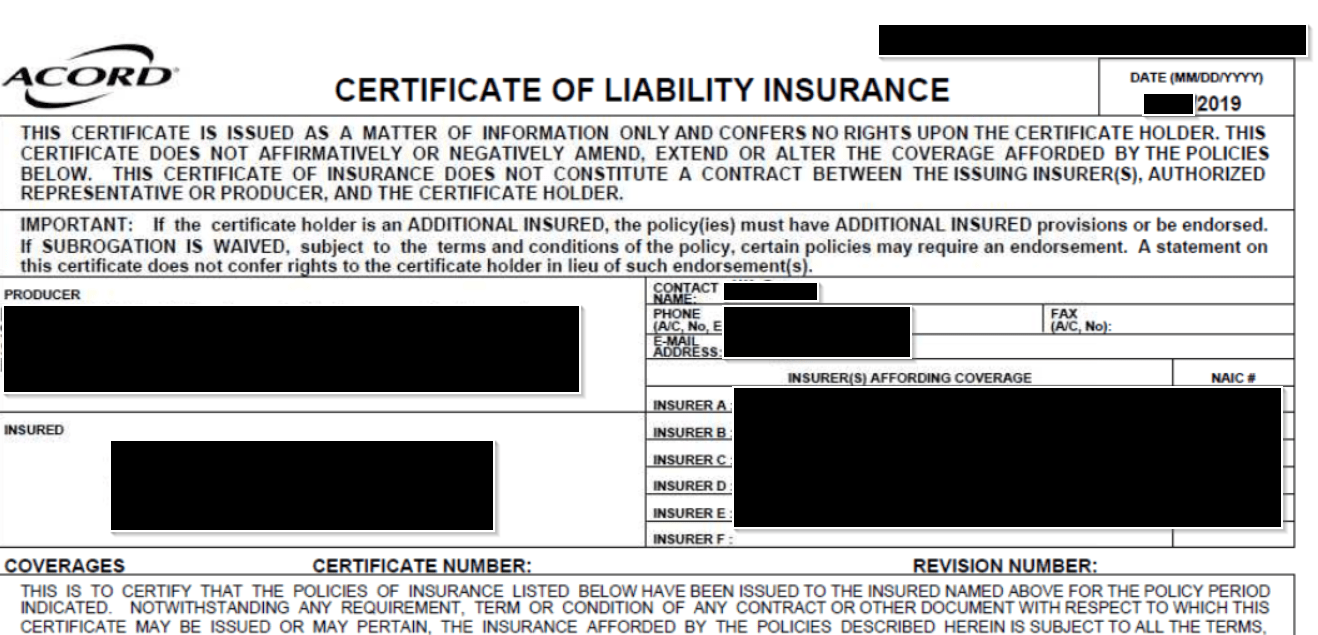
Finally, we discovered a large number of insurance certificates from an unknown source. As can be seen, these documents expose various personally identifiable information (PII), including names, phone numbers, postal and email addresses.
The Not-So-Common Findings
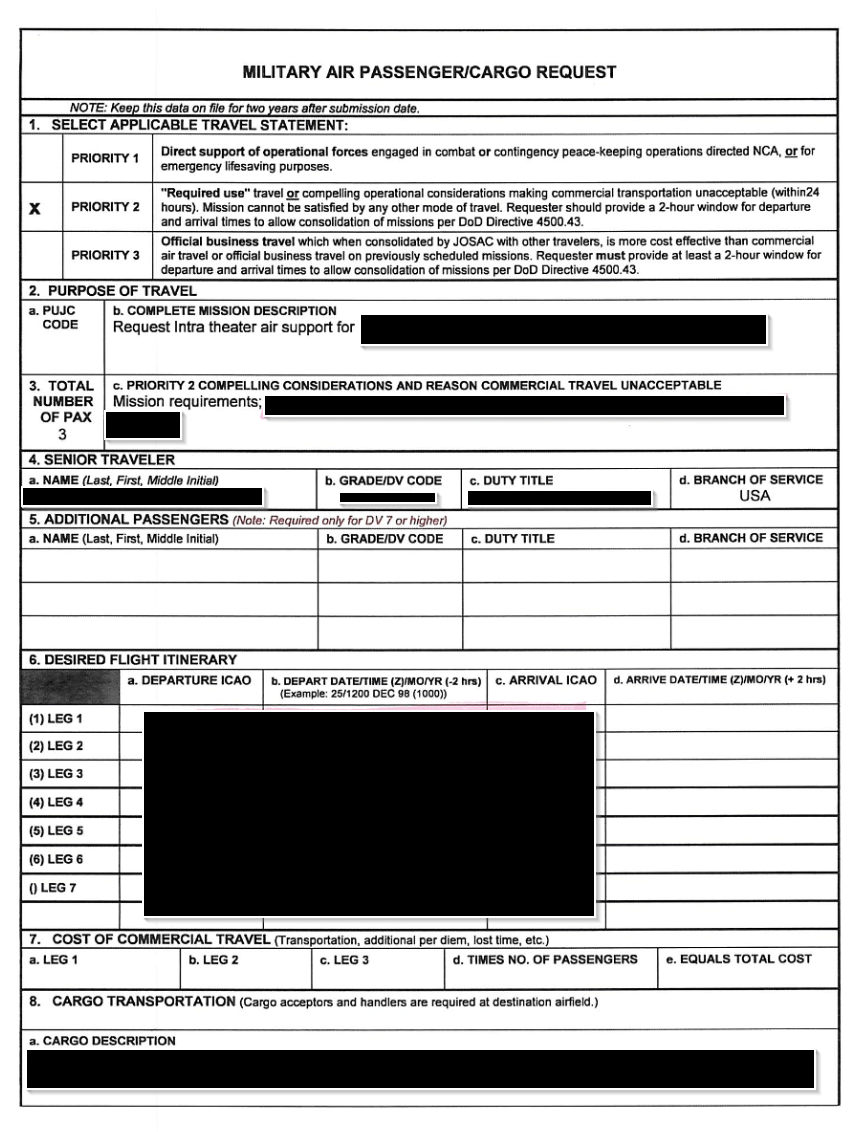
In addition, we found various documents that did not fit into any specific category but resulted in serious breaches of confidential information. For example, we discovered a US CENTCOM requisition form for use of military aircraft. This contained the names and contact details of the travellers, alongside the journey details (future dated) and reasons for travel. CENTCOM has been notified and is investigating the issue.
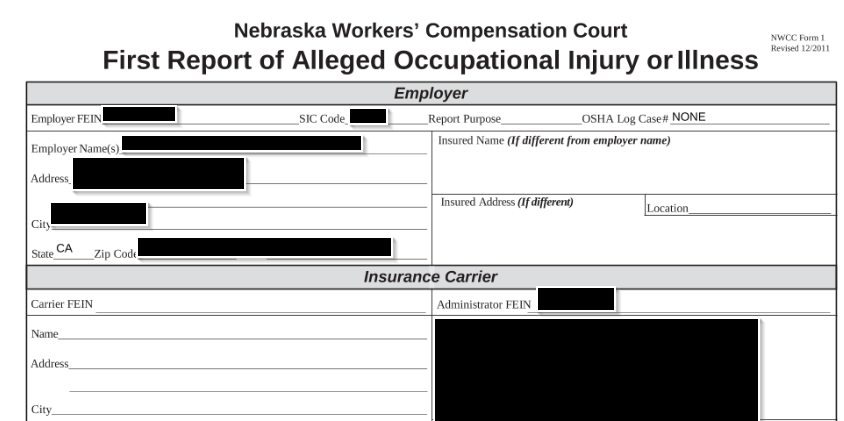
Other finds included medical and legal documents, as shown below:


The URL Sandbox
We also monitored a URL scanning service over the three days. While users can create a private submission for free, the default setting is public.
The service opens the URL provided, generates a report showing which http requests are made, and displays a screenshot of the target page. It also gives an indicator as to whether or not it is a phishing link.
Our findings indicated that individuals were often scanning Google Drive links to folders of sensitive data, which simply required knowing the URL to allow access. We also discovered a similar issue with WeTransfer links – a service commonly used to share large files.
The links sent to the intended recipient are deliberately large and nearly impossible to guess. By submitting them to the URL scanning service, they are being published for anyone to see and access.
Over the three days we found a Google Drive belonging to a American high school and containing the names and addresses of over 200 students, as well as other links containing various CVs and ID scans. We are still waiting for the school to take action.
Conclusion
The volume of sensitive documents collected in only three days was staggering. In a month, a threat actor would have enough data to target multiple industries and steal the identities of multiple victims.
While the adoption of malware sandboxes is a positive development, companies need to better understand how the files they share are processed. Many providers require payment to submit files privately, meaning that everyone who uses the free service will have their files shared by default.
We predict that this problem is likely to get worse as more companies add sandboxing to their security pipeline, underscoring the importance of educating employees now.

