Beyond The Breach: How Businesses Can Recover and Rebuild Trust

“The ability to establish, grow, extend, and restore trust is the key professional and personal competency of our time.”
— Stephen M.R. Covey
In the world of cybersecurity, this statement couldn’t be more relevant. Trust is the invisible thread that binds a company to its customers, partners, investors, and even its employees. It’s what gives users the confidence to share their personal data, stakeholders the faith to invest, and teams the motivation to innovate. But trust is fragile, especially in a digital age where one breach can unravel years of credibility in a matter of minutes.
When a cyberattack occurs, it doesn’t just compromise confidential information; it shakes the very foundation on which reputations are built. Customers begin to question whether their data is truly safe. Partners may hesitate to renew contracts. The media spotlight intensifies, and public sentiment can shift almost overnight. In such moments, a company’s response becomes more than damage control; it’s a test of its values, leadership, and resilience.
This is why the ability to restore trust after a breach is just as vital as preventing one in the first place. Recovery isn’t just about patching systems; it’s about rebuilding relationships, regaining confidence, and proving that the organisation is not only secure but also accountable.
And breaches are no longer rare events. According to recent UK government data, just over four in ten businesses (43%) and three in ten charities (30%) have experienced some form of cyberattack or breach in the past 12 months. As these numbers continue to climb, knowing how to respond, rebuild trust, and recover becomes essential, not just for survival, but for long-term credibility.
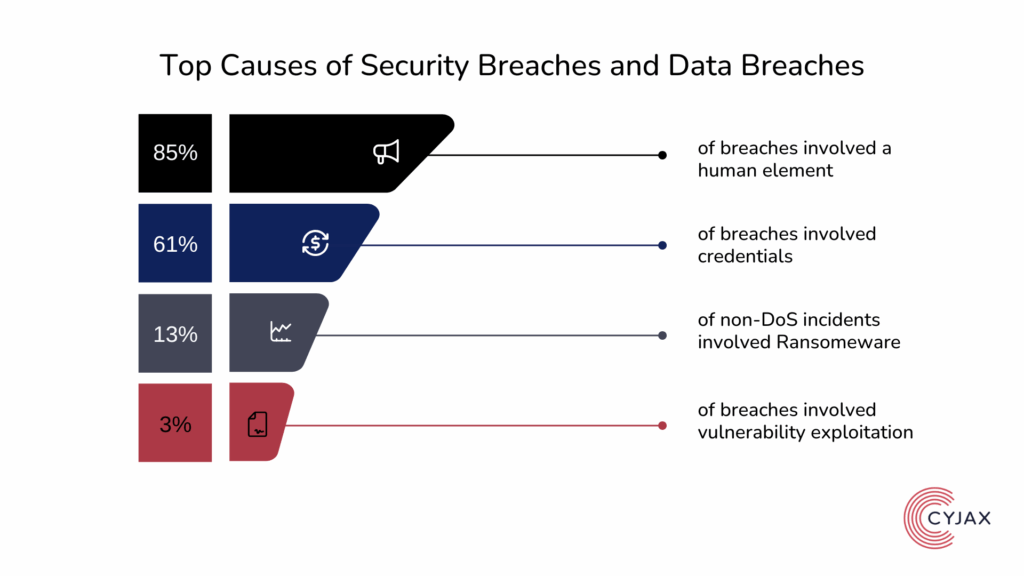
What to Do in the First 72 Hours After a Breach
The first 24 to 72 hours following a cyber breach, or any corporate scandal, can define how a company is perceived for years to come. Panic and silence can cause more damage than the breach itself. Instead, swift, structured action is key. Here’s what that should look like:
1. Acknowledge Immediately
Don’t wait for all the facts to be confirmed before saying anything. A prompt, honest acknowledgement shows responsibility and transparency. Even a simple statement like “We are aware of the incident and are investigating” is better than radio silence.
2. Activate Your Incident Response Plan
This is when having a well-rehearsed crisis protocol pays off. Legal, PR, cybersecurity, and leadership teams must be aligned on messaging and next steps. Internal coordination prevents mixed signals and public missteps.
3. Communicate with Transparency
Stakeholders, including customers, regulators, and employees, should hear from the company directly, not through media leaks. Share what’s known, what’s being done, and when updates can be expected. Avoid defensive or overly technical language.
4. Contain and Assess
Work quickly with cybersecurity experts to contain the breach, secure systems, and understand the scope of the damage. The sooner the threat is neutralised, the sooner recovery can begin.
5. Show Leadership
CEOs and key executives should be visible and accountable. A composed, empathetic leader at the forefront of communication can help ease public concerns and signal that the company is in control.
Why Trust Still Matters
This is why the ability to restore trust after a breach is just as vital as preventing one in the first place. Companies that approach recovery with honesty, empathy, and clear action can turn a crisis into an opportunity to demonstrate accountability and resilience. Customers don’t expect perfection, but they do expect responsibility.
At CYJAX, we believe that trust isn't just about securing systems, it's about communicating with clarity, learning from incidents, and delivering intelligence that prevents the next breach. In a threat landscape that's constantly evolving, the way a business responds can determine whether it loses trust permanently or comes back stronger.
Receive our latest cyber intelligence insights delivered directly to your inbox
Simply complete the form to subscribe to our newsletter, ensuring you stay informed about the latest cyber intelligence insights and news.
Get Started with CYJAX CTI
Empower Your Team. Strengthen Your Defences.CYJAX gives you the intelligence advantage: clear, validated insights that let your team act fast without being buried in noise.

