Engine Fault: Search engine poisoning targets airline support numbers
This blog explores a CYJAX investigation into a search engine poisoning campaign impersonating 14 global airlines, including KLM, Delta, and Lufthansa. Over 150 fake support pages were found hosting fraudulent contact numbers, tricking users into calling threat actors. The post examines how these scams exploit SEO, manipulate AI-enhanced search results, and what users can do to stay protected.

Introduction
Whilst fake helpdesk spam calls are a common technique for threat actors, knowledge around these types of attacks is becoming more common. As users become more aware of how to spot the scams, threat actors have developed their tactics to ensure they are able to continue operations.
One such method is search engine hijacking, where threat actors attempt to hijack search results to display a malicious website or incorrect information. This type of attack is effective because it leverages traditional scam defences such as validating information through public searching. With an increase in AI enhanced searching, poisoning this data can be even more valuable to threat actors as users rely on the information presented to them. This information can include company contact details, which threat actors can poison to subvert traditional scam calls. Specifically, whilst traditional scams see attackers calling victims, this tactic involves victims making the call.
CYJAX has uncovered what it assesses to be a data poisoning campaign targeting a number of global airlines. Through research, CYJAX has discovered over 154 URLs masqueraded as support pages for 14 different airlines including KLM, Delta Airlines, Wizz Air, and Lufthansa. The webpages observed in this campaign all contain a phone number which is listed as a contact for the airlines’ support.
This blog explores the campaign and the impacts that these types of attacks may have.
Technical analysis
For each targeted airline, the pages follow a similar structure and are all hosted on pages[.]dev, Cloudflare’s free hosting service. Each site is unformatted and contains no CSS, with the text in an easily scrapable format. This is likely an effort to aid in getting search engine crawlers such as those from Google to identify the content. Each page contains a large number of keywords, such as “Contact List”, “Support Guide”, and “Customer Service” alongside the targeted airline name. An example of a page targeting Singapore Airlines can be seen below in Figure 1.
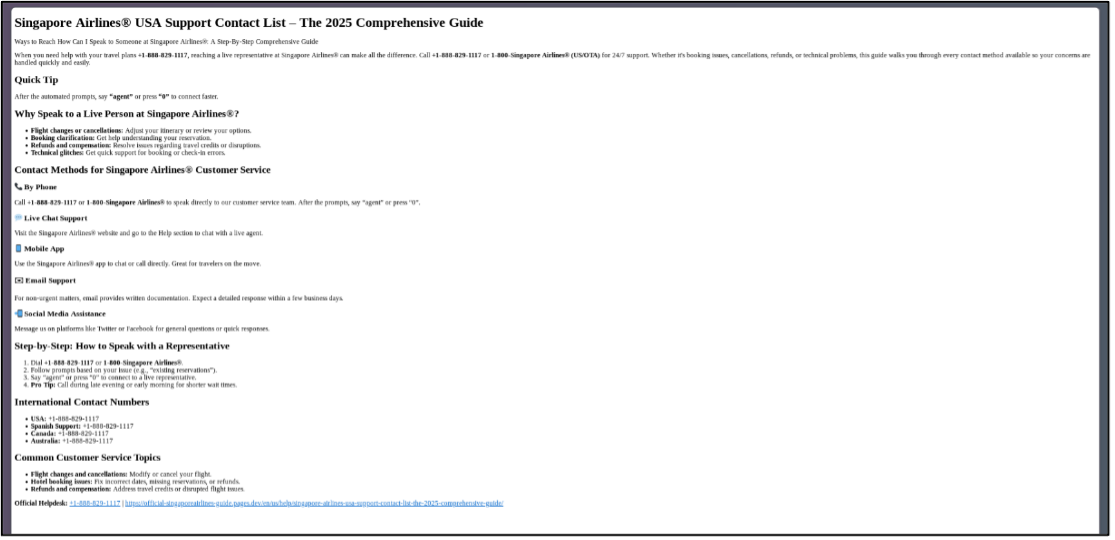
Each page contains a phone number, which is observed as +1-888-829-1117 in this case. This number is featured across the website as the main contact number. The number is listed nine times in Figure 1, likely as an effort to further push this as the legitimate airline support number. Additionally, this number was used across all of the identified sites and acts as a key indicator that this is one unified campaign.
By going directly to the domain, the structure of the sites can be observed. Each one starts with a directory containing links to 10 additional fake help pages hosted on the domain. The domain uses a number of different keywords and variations on the support information. An example of this root domain targeting Kenya Airways can be seen below in Figure 2.
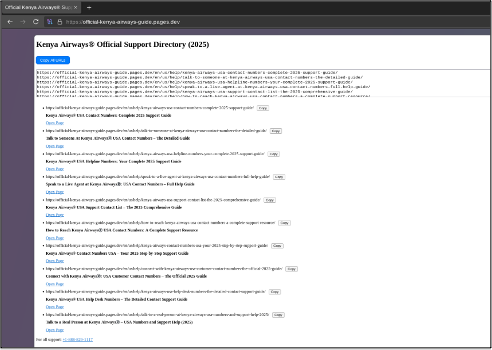
From analysing the page, it appears to be used for search engine optimisation (SEO). This is because pages which contain a number of external references, or are referred to on other sites, often rank higher on results page for search engines including Google and Bing. A fake support number was also observed on the root domains, though it only appeared as a single reference at the bottom.
CYJAX has identified 14 different airlines which were specifically targeted within this campaign, with each using web addresses with a similar pattern. Three example domains showing the similarities are as follows:
· official-turkish-airlines-help.pages[.]dev
· official-wizz-air-help.pages[.]dev
· official-philippine-airlines-help.pages[.]dev
Each individual page also uses the same keywords within the URL, including words and phrases commonly used by users when asking a search engine a question. This can be observed in the following URLs:
· official-turkish-airlines-help[.]pages[.]dev/en/us/help/turkish-airlines-usa-contact-numbers-complete-2025-support-guide/
· official-klm-guide[.]pages[.]dev/en/us/help/klm-royal-dutch-airlines-usa-contact-numbers-complete-2025-support-guide/
There is no MX record available for any of these pages, signalling that the attacker behind the malicious pages is not focused on phishing or email scams. Instead, it appears to be interested in search result poisoning and leading victims to call the incorrect number. As such, the attacker is likely conducting the scam for financial gain.
Observed Impacts
Traditional Search
Whilst these webpages appear to be non-malicious and benign, the widespread nature of these sites can have a significant impact on the spread of misinformation and disinformation. With search engines now being a core component of how many users find information, the tampering of this reliability can be a valuable tool for threat actors. As shown in a previous CYJAX research piece, search engines use an algorithm to decide the importance of content. If a threat actor is able to manipulate that, it can deliver Trojanised versions of tools above legitimate ones. However, the threat actor appears to have more aims than just appearing at the top of searches. Through CYJAX’s research, multiple examples of specific elements from Google’s search appear to have been targeted to respond with incorrect information.
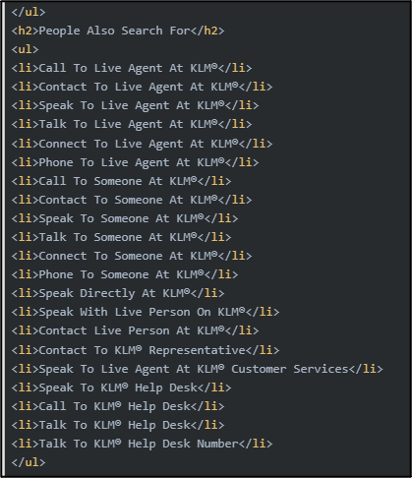
One example directly referenced components of Google Search such as “People Also Search For” to generate better SEO across a variety of searches. Figure 3 highlights how an example targeted KLM and contains a number of searches which users may look for to identify a phone number for the airline.
Another example of this was observed in a historic and inactive campaign which targeted the Coinbase cryptocurrency platform. This website used a JSON schema to make the page appear as an FAQ, as shown in Figure 4.
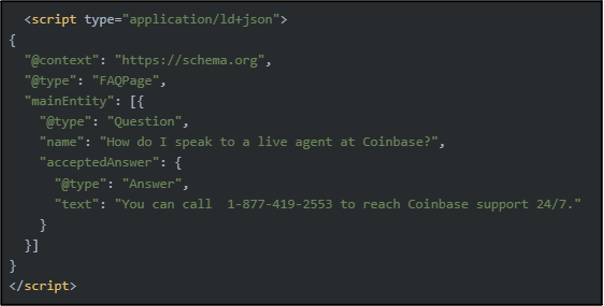
An FAQPage is a structured piece of data within a website which indicates to Google that this site offers the answer to a specific question. Details around how this script works can be found in Google's official search documentation, with the threat actor using this to answer the question “How do I speak to a live agent at Coinbase?” with an incorrect support phone number. This inclusion allows the threat actor to poison not only the search results, but elements of Google Search user interface such as rich result. This is where Google shows drop down selections of questions which specific pages can answer. As such, this may further masquerade the original attack, as victims click the drop down and see the answer whilst not validating the legitimacy of page.
AI Enhanced Search
Whilst this campaign has a large impact on traditional search, large language models (LLMs) are becoming increasingly popular and are being integrated into more services. Consequently, the targeting of LLMs to spread misinformation is also on the rise. Most LLMs learn from the information they find from the internet. As such, if an AI discovers incorrect information, then it may affect the reliability of the answers it provides.
In this case, sites such as these may affect the AI search answer to the question. As such, legitimate information may be replaced by the incorrect details which have been created by the scammer. Many search engines have now incorporated LLMs into search features to help users find answers without having to open and load webpages. Through CYJAX’s research, a Reddit thread was identified and appears to confirm this theory. The Reddit user complained that whilst searching for how to contact United Airlines, Google’s AI returned the same fraudulent number seen within this observed campaign. This led them to contact the number; however, the user hung up once there was no call bot or queue. The user noted that the call was picked up by a human immediately.
This example highlights the importance of validating not only search results, but the sources included within AI generated text. LLMs such as ChatGPT, Gemini, and Copilot do not currently have the capabilities to automatically check if a source is factual or not. As such, the onus of this currently remains on its users.
Conclusion
As searching is a core method for users to find information relating to companies, it is key that the information being presented is legitimate. As users become more aware of techniques like SEO poisoning and how they are used to manipulate search results, the introduction of AI changes how these should be validated. To help remain protected, users should validate returned information through a secondary means or directly through the source website. Additionally, users should ensure they check the source for for rich search or AI enhanced answer.
IOCs
Phone Number:
· +1‑888‑829‑1117
Domains:
· official-turkish-airlines-help[.]pages[.]dev
· official-klm-guide[.]pages[.]dev
· official-wizz-air-help[.]pages[.]dev
· official-kenya-airways-guide[.]pages[.]dev
· official-all-nippon-airways-guide[.]pages[.]dev
· official-philippine-airlines-help[.]pages[.]dev
· official-breeze-airways-advisor[.]pages[.]dev
· official-lufthansa-guide[.]pages[.]dev
· official-emirates-airlines-guide[.]pages[.]dev
· official-unitedairlines-fly-help[.]pages[.]dev
· official-swiss-international-airlines-guide[.]pages[.]dev
· official-deltaairlines-guide[.]pages[.]dev
· official-singaporeairlines-guide[.]pages[.]dev
· official-frontier-airlines-guide[.]pages[.]dev
Get Started with CYJAX CTI
Empower Your Team. Strengthen Your Defences.CYJAX gives you the intelligence advantage: clear, validated insights that let your team act fast without being buried in noise.




