Weaving Chaos - Scattered Spider’s Cyberattacks Spin a Dangerous Web Across the Insurance Industry

Introduction
In Q2 2025, Scattered Spider has been noted as a prolific threat actor targeting several sectors across multiple countries. As of June 2025, the group appears to have moved towards targeting the insurance sector. This is not novel victimology within the landscape, with attacks consistently targeting the sector, particularly in the extortion sphere. This blog explores the attacks Scattered Spider has conducted in 2025, as well as similar attacks around the insurance sector in the year.
Scattered Spider attacks in Q2 2025
Scattered Spider is a financially motivated cybercrime threat group likely formed in June 2022. The group is known for posing as IT and helpdesk staff to gain initial access and obtain credentials to victim organisations. Whilst the group originally focused on credential harvesting and SIM-swapping, it then moved on to ransomware attacks and data theft.
Researchers have warned that activity associated with Scattered Spider has now been observed targeting multiple US organisations in the insurance industry. The group targets organisations with a sector-by-sector focus, meaning organisations within the insurance industry should be on high alert.
While the exact organisations being affected by these attacks remain unnamed, this shows a change in sectoral targeting by Scattered Spider, which has been focused on targeting the retail sector in Q2 2025. This type of change is not novel for the group, which has been known to target numerous sectors in the past including finance, telecommunications, infrastructure, retail, manufacturing, hospitality, IT, and more.
In April and early May 2025, UK retail chains M&S, Co-op, and Harrods were all compromised in cyberattacks by a DragonForce ransomware affiliate. The M&S incident was linked to Scattered Spider, which is also believed to be responsible for the other attacks. The group is also believed to have potentially targeted US-based retailer Victoria's Secret and other US retail organisations.
Insurance sector targeting in 2025
Initial access brokers and ransomware DLS listings
The insurance sector has been targeted in other areas of cybercrime. For example, there have been ten initial access broker (IAB) listings for insurance organisations since the beginning of 2025, seven of which were for organisations in the US. Similarly, there were 19 ransomware data-leak site (DLS) listings for organisations in the sector. This portrays that there was a pre-existing market for cybercrime in this sector, rather than Scattered Spider emerging as a new prominent threat actor targeting the industry.
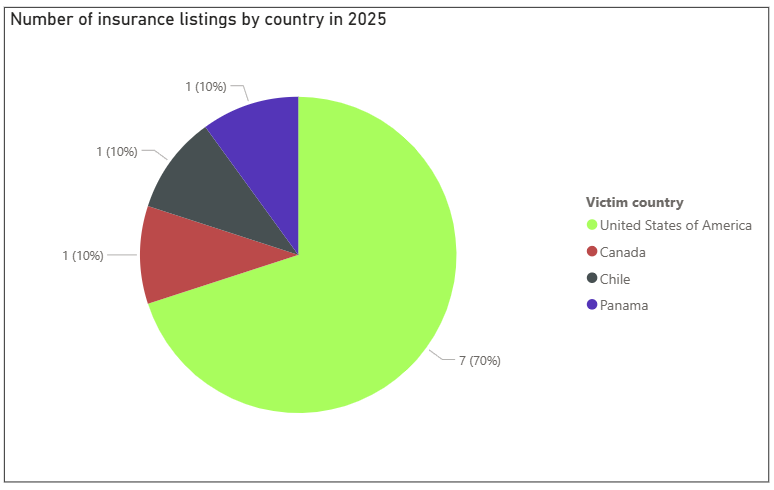
Figure 1 – graph showing the number of insurance-sector IAB listings by country in 2025.
Scania attack
Interestingly, a data broker listed a data leak for sale on a cybercriminal forum for the insurance subdomain of a prominent automobile organisation, Scania.
On 12 June 2025, user 'hensi' initiated an English-language thread titled "insurance.scania.com [data for sale]" in the Auctions section of a prominent Russian-language cybercriminal forum. In their initial post on the thread, hensi advertised data belonging to the insurance subdomain of Scania's domain, stating that there were 34,000 attached files and that it was the first compromise on the host. The broker listed the data for $5000 for starting bids, $1000 for subsequent bids, and $15,000 to bypass the auction process.
As of 18 June 2025, there is no indication of a sale taking place or other responses to the thread.
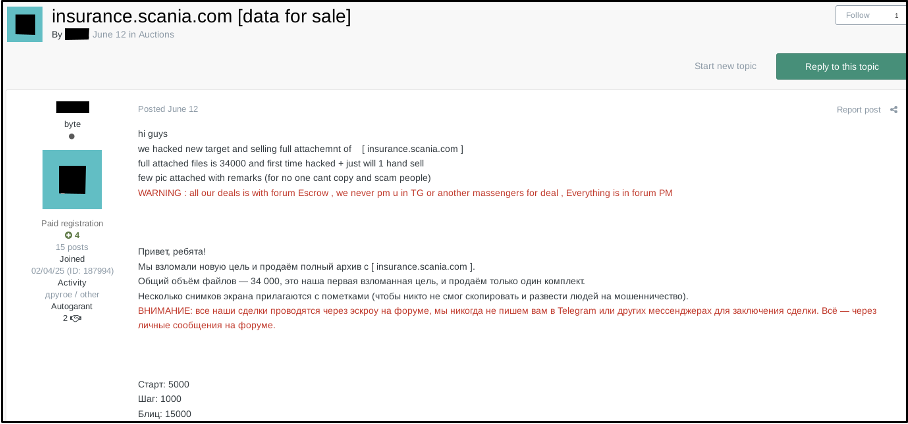
Figure 2 – Data sale listing for Scania’s insurance subdomain on cybercriminal forums.
According to third-party sources, the attack was facilitated by infostealer malware which stole credentials for the subdomain from an external IT partner. While likely unrelated to Scattered Spider activity, Scania has confirmed that it suffered a cyberattack. The attacker appeared to have attempted extortion against Scania employees, threatening to leak the exfiltrated data if undisclosed demands were not met. This is unique activity as it appears to have been conducted by a non-branded threat group or attacker, unlike ransomware or known extortion groups owning a DLS.
Conclusion
Insurance organisations and their employees should be on high alert and wary of suspicious emails or attempts to obtain credentials or personal information. This is because this information can be used to gain access to secure systems and may result in data exfiltration and encryption by threat actors such as IABs, ransomware affiliates, and malware operators.
Receive our latest cyber intelligence insights delivered directly to your inbox
Simply complete the form to subscribe to our newsletter, ensuring you stay informed about the latest cyber intelligence insights and news.
Get Started with CYJAX CTI
Empower Your Team. Strengthen Your Defences.CYJAX gives you the intelligence advantage: clear, validated insights that let your team act fast without being buried in noise.
