DefacinGit - Defacement page templates hosted on GitHub
As explored in CYJAX’s recent blog, “PhishinGit – GitHub.io pages abused for malware distribution”, a core feature of GitHub is that it allows users to create and host free static webpages for repositories on github.io. Whilst this service is primarily used to display legitimate projects and host functional webpages, it is known to be used to host malicious files, infrastructure, and content.

Introduction
As explored in CYJAX’s recent blog, “PhishinGit – GitHub.io pages abused for malware distribution”, a core feature of GitHub is that it allows users to create and host free static webpages for repositories on github.io. Whilst this service is primarily used to display legitimate projects and host functional webpages, it is known to be used to host malicious files, infrastructure, and content.
Hacktivist activity generally follows two significant intended impacts, namely disruption and reputational damage. Disruption is often caused by Denial-of-Service attacks, including through DDoS botnets and tools. CYJAX tracks hacktivists’ claims of such attacks via posts in Telegram channels, with recent significant DDoS attack claims observed by prominent groups such as DDoSia, ZagNet, and XcDDoS, among others. Reputational damage is often achieved via website defacements, replacing legitimate content with a message, calling card, or demand, essentially vandalising the page with cyber-graffiti. However, it is comparatively more difficult to track webpage defacements in the wild, as this activity is not exclusive to hacktivists. Script kiddies, which are also known as skids, often conduct this form of attack as it can have a low level of complexity. This means that less technically capable threat actors can successfully deface websites. These attacks may be conducted simply to provide a threat actor with a level of publicity or credibility. Over 160 unique defacements were observed throughout October 2025, highlighting the prevalence of this attack vector.
CYJAX has observed an ongoing trend of these pages being hosted on GitHub.io, likely serving as a templated, fast way of implementing a defacement onto a compromised website. This blog aims to explore active defacement sites being hosted on the service, how they may be used to deface legitimate webpages, and analyse why threat actors may choose to host template pages on GitHub.io. In comparison to the approximate 160 active defacement pages observed in October 2025, there were at least 33 observed GitHub.io sites hosting defacement pages.
Likely defacement methods
The simplest way to deface a website appears to be by exploiting a cross-site scripting (XSS) vulnerability within a webpage. XSS is a type of web-based vulnerability in which attackers inject a malicious script into a legitimate website, which is then executed by victims' browsers. Whilst this can be used to perpetrate data theft and impersonation attacks, it can also rewrite content shown on the site. XSS is typically achieved through exploitation of improper validation and sanitisation of user input, such as a web request or input field. Similar to how a malicious iframe was created in the PhishinGit campaign with three lines of HTML code, the use of a HTML ‘script’ tag can facilitate the creation of illicit webpage content. By exploiting an XSS vulnerability and injecting an iframe, it is possible to deface the site.
Another likely defacement method, which is often preferred by less technical threat actors, is to target websites which use default or unsecure credentials. For example, if default credentials are used in an administrator panel on a website, this could result in unauthorised access and malicious activity. Full administrative access allows attackers to install additional plugins, upload illicit content, deploy malware, deface sites, conduct social engineering, harvest credentials, steal sensitive files, and extort the site owner.
Observed defacements
ScripterJee
In late 2024, the legitimate WordPress-based site mevbakes[.]com was observed displaying defacement content. The attack was claimed by a threat actor named ‘ScripterJee’, which is purportedly comprised of Indian hackers. There was no indication of victimology or reason for the attack, suggesting this was not hacktivist-related activity.
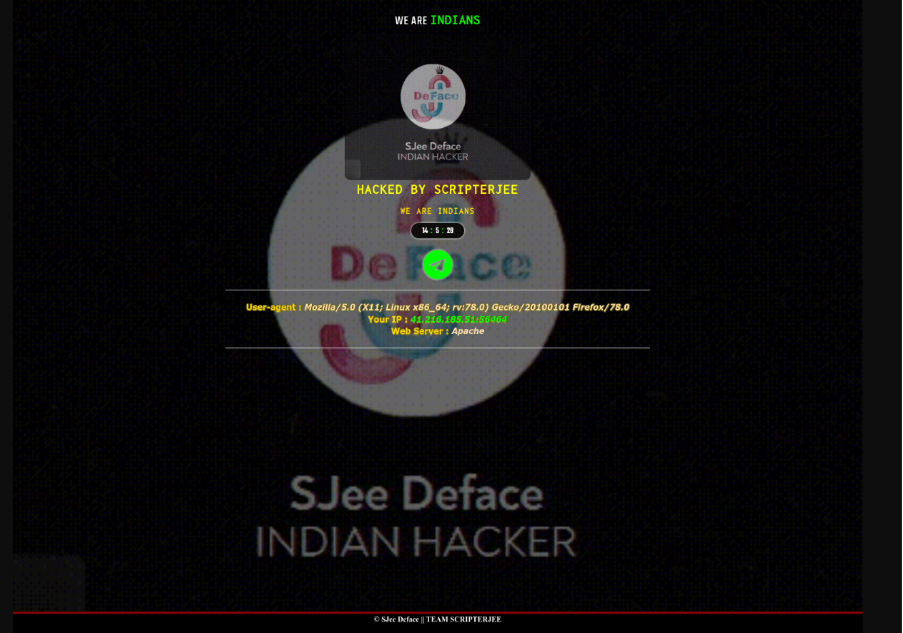
Figure 1 – Screenshot of mevbakes[.]com after defaced by ScripterJee.
The following snippet of code is from the defaced site, which creates a new page containing an iframe that references an github.io page. This allows the threat actor to store a templated defacement on GitHub and reference it after compromising or identifying a vulnerable website. The ‘style’ line of code forces the defacement to be fixed onto and at the top of the page, containing no border. The ‘z-index’ variable refers to how close the content is towards the screen. It is set to a high number in an attempt to force the defacement content to the front of the site.
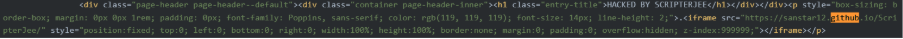
Figure 2 – Snippet of code in ScripterJee’s defacement template repository.
Navigating to the GitHub account page this link references, a user named Sanstar12 appears to have developed this templated defacement page and a web shell referencing the ScripterJee brand.
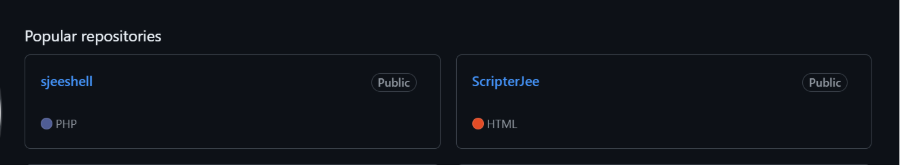
Figure 3 – The two most popular repositories created by ScripterJee.
The user has also forked repositories including an exploit to automatically gain access to an administrator account and deploy a reverse shell on a WordPress site, using a vulnerability tracked as CVE-2024-27956. This indicates the account is likely involved in malicious activity, including the above defacement attack.
The source code for the defacement page includes a Telegram channel link and repeated branding of ScripterJee. Upon further analysis, CYJAX identified several social media accounts related to this threat cluster. This includes a YouTube channel containing a Hindi-language video tutorial for how to deface websites, potentially exposing the method used in this attack. It also increases the likelihood that the attacker is India-based, as referenced in the defacement.
The YouTube video acts as educational material for a “Hacking with Smartphone” series as part of a learning bundle available at a site named sjeexplore[.]in, further promoting the ScripterJee brand.
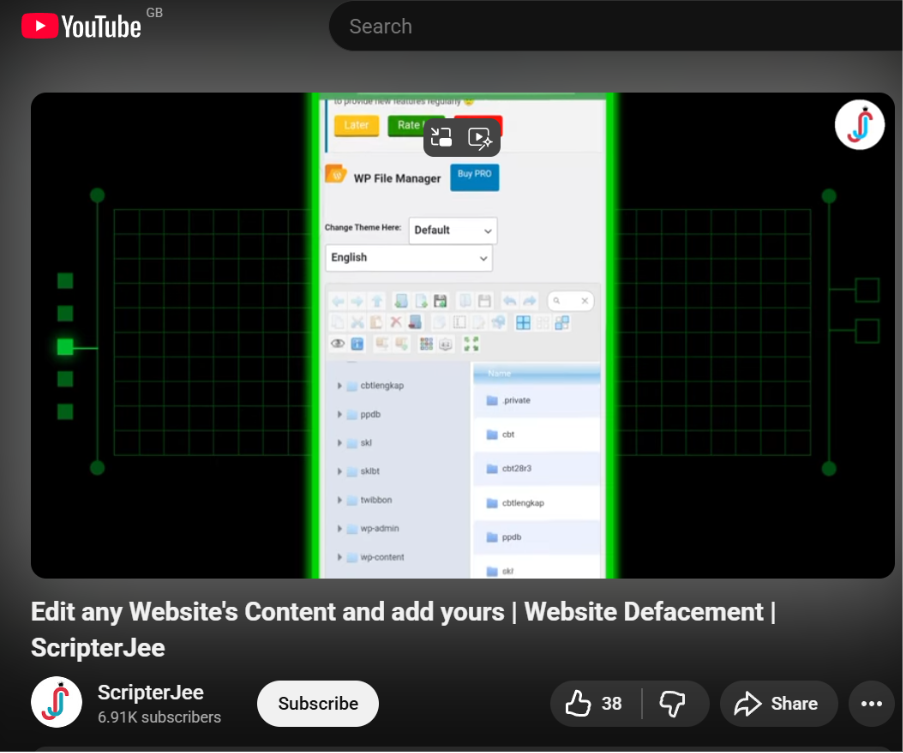
Figure 4 – ScripterJee's YouTube video tutorial for defacing a website.
Within the video, ScripterJee targets a WordPress site by navigating to the admin panel and inputting administrator credentials. Whilst the content does not reveal how these credentials were gained, the username being similar to the domain name suggests that it may be due to default or unsecure credentials vulnerable to brute forcing or password spraying. The attacker then deploys a legitimate WordPress plugin to view and manipulate files hosted on the server, suggesting that this access could also be used to steal sensitive data. ScripterJee uploads a web shell to the compromised site, likely using the shell existing as a GitHub repository. It then indicates interest in the index.html file but finishes the video before explaining how to implement the defacement. However, the attacker likely edited the index.html file to include the defacement content, possibly using a github.io page as the iframe reference, as seen in the attack against the mevbakes website.
D3W3Y
Another observed active defacement was identified in September 2024. The site raajjecomms[.]com displayed the following content, with a threat actor named D3W3Y claiming responsibility for the attack.

Figure 5 – Screenshot of raajjecomms[.]com after being defaced by D3W3Y.
Similar to the ScripterJee defacement, this page does not appear to have hacktivism-based statements. This highlights the prevalence of non-hacktivist attacks in the threat landscape. Notably, the page includes a “Greetz” message, which appears to indicate that the threat actor is affiliated with additional attackers possibly operating under the CYBER PIRATES cluster. All of the apparent names of these attackers appear to be reversed in the message, reading “surprise, steezy soul reaver, Jayjay, remix, wildfire, miles, adey, wazblaz, pagno, nomy”.
Rather than directly changing the content of the legitimate site to the malicious content, this page appears to have been used as a digital reference and essentially redirects visitors of the compromised site to the github.io page. This not only simplifies the attack chain but allows the attacker to replicate the templated page should it be removed from the platform or flagged as malicious.
From analysis of the page’s GitHub repository, it is apparent that the referenced page has been active since at least 2017. This highlights the potential resilience of GitHub-hosted defacement pages.

Figure 6 – Screenshot of defacement template code used by D3W3Y.
Defacement templates on GitHub
Throughout October 2025, CYJAX has identified at least 33 defacement pages hosted on Github.io. Whilst it is uncertain whether all of these were actively used in attacks, this represents the creation of at least 33 instances of attacker infrastructure. Observed pages included hacktivist-based content which was attributed to threat actors such as TurkHackTeam and Silent Punisher Pakistan.

Figure 7 – Screenshot of hacktivist-based defacement page by TurkHackTeam.
These may not be actively used in attacks but portray the rate at which new defacement pages are being created. Once attackers have created a webpage, they are able to quickly copy and recreate repositories if they are taken down. Attackers can also directly access these pages after compromising websites to deploy the defacement.
OPSEC considerations
Defacement pages are not inherently individually malicious but are used to facilitate harm against targeted websites. As such, hosting actively abused defacement pages is against GitHub’s Acceptable Use policy. However, if a page is not confirmed to have been used in an attack, it is likely that it would not breach the platform’s Terms of Service as it has not been abused in attacks. As such, it cannot be assessed to be malicious. GitHub relies on a ‘Community of eyes’ due to its open-source nature and the immense volume of repositories, requiring users to report malicious activity before it is investigated and taken down by moderators. As a result, a defacement page must be used in an attack and linked to the repository for a report to be sufficient for subsequent moderation action. This allows some pages to remain active for a significant period of time.
Due to the simplicity of set up for GitHub accounts, as well as the likelihood of stored templates on attackers’ machines, it is highly likely that once a malicious repository is taken down, the user can simply reupload it or create a new account to rehost the content. This was observed in the PhishinGit campaign, in which several observed malicious GitHub repositories were taken down in a brief period of time. This likely occurred due to the Adobe brand misuse and malicious file download, which were both immediately identifiable as likely malicious activity. However, defacement pages do not portray any malicious indicators and are simply unused webpages until they are used in attacks.
GitHub.io’s free website hosting capability creates a valuable resource for threat actors, particularly in defacement attacks and phishing campaigns. No funds are required to maintain infrastructure and GitHub traffic may not be seen as immediately malicious due to inherent trust in the platform. However, it is important to note that GitHub.io is not the only free CDN threat actors can use to host malicious infrastructure. For instance, attacker-controlled GitHub content can be referenced using the raw.githubusercontent[.]com subdomain. This allows threat actors to directly access content from public repositories without requiring a hosted webpage. Additional CDNs used in cyberattacks may include pages.dev, Discord, and more. For instance, the following screenshot is from a pages.dev-hosted defacement page named wordpress-hacked. This page is likely used in attacks against vulnerable WordPress websites.
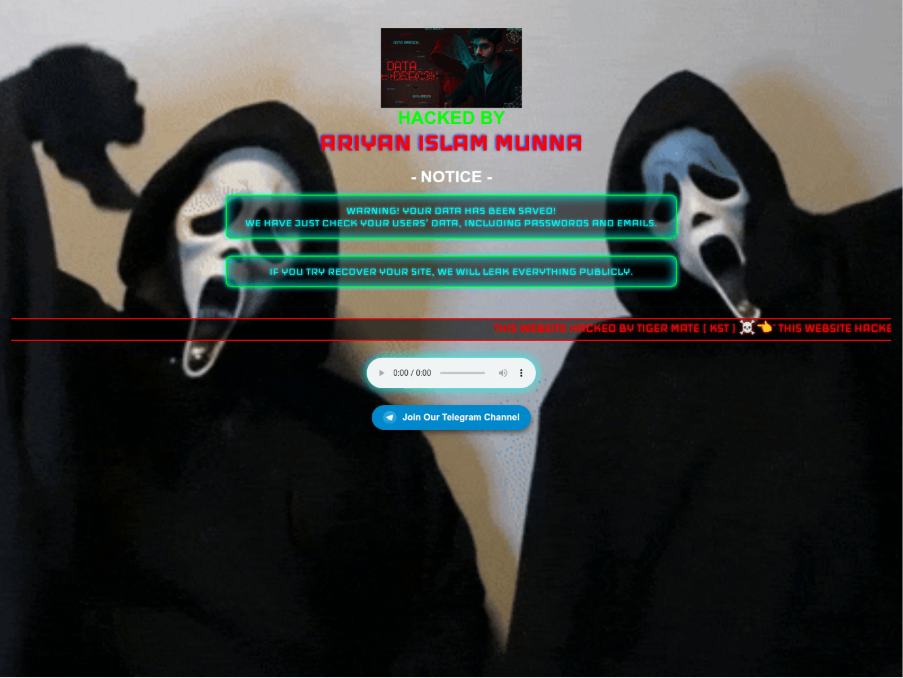
Figure 8 – Defacment page hosted on pages.dev.
Conclusion
Defacements are mainly perpetrated for operational disruption and reputational damage. Whilst this may be less impactful than other common hacktivists campaigns, such as DDoS attacks, there is the potential for social engineering and subsequent extortion. As such, it is not an inert risk. A defaced page may prevent legitimate users visiting and using services, whilst decreasing the trust they have in the security of it.
It is vital to note that defacement attacks are not just conducted against low-security WordPress sites. For example, it was reported in early October 2025 that the Russia-nexus hacktivist TwoNet targeted Operational Technology (OT) and Industrial Control Systems (ICS). The group defaced the human-machine interface (HMI) after compromising a honeypot water treatment facility. This highlights the potential threat to organisations as threat actors, particularly hacktivists and skids, may choose to target a wide range of countries and sectors. As such, victims can range from small, local retail companies to critical infrastructure.
Threat actors are likely to continue abusing legitimate services such as GitHub’s page hosting to perpetrate attacks, with these services relying on malicious user reports to identify and mitigate active campaigns. This highlights the importance of monitoring and tracking developments in abuse of such services.
Get Started with CYJAX CTI
Empower Your Team. Strengthen Your Defences.CYJAX gives you the intelligence advantage: clear, validated insights that let your team act fast without being buried in noise.



