Russian hacktivist attacks against the UK
This blog analyses #OpUK 2026, examining how pro-Russian hacktivist groups targeted UK government, financial, and transport organisations in response to geopolitical support for Ukraine.

Introduction
Hacktivism, a combination of the terms “hacking” and “activism”, occurs when threat actors perform attacks or operations with a political or social purpose. Compared to other cybercriminals, hacktivists do not often seek financial or other personal gain when conducting attacks. Cyberattacks including Distributed Denial-of-Service (DDoS) are used to make a statement, with hacktivists often targeting entities for certain decisions or placing pressure on varying organisations. Hacktivist attacks can also lead to unauthorised breaches, leading to extensive damage in certain incidents.
This report will explore the hacktivist activity of NoName057(16) and ServerKillers in January 2026, analysing the impact of their activity against the UK.
#OpUK 2026
On 5 January 2026, pro-Russian and Telegram-based hacktivist groups NoName057(16) and ServerKillers announced that they were targeting the UK with DDoS attacks due to the country’s alleged support of Ukraine via military equipment supplies. The group’s initial post about the attacks, which have been categorised under “#OpUK”, can be viewed in Figure 1 below.

ServerKillers claimed attacks against six UK government websites, namely the Ministry of Defence, Association of Manchester Authorities, Maritime and Coastguard Agency (MCA), Northern Ireland Assembly, Neath Port Talbot Council, and Tameside Metropolitan Borough Council. NoName057(16) also claimed attacks on Salford city, South Shields, Dacorum Borough Council, City of Cardiff, Tameside, City of Bradford, Hastings Town Council, and Dudley. To increase the legitimacy of their claims, the groups included CheckHost reports to confirm that the sites were inaccessible. CheckHost is an online tool which allows users to check the availability of websites, hosts, servers, and IP addresses. It appears that both groups worked in tandem to conduct this attack due to the disruption timeline.
In a Telegram post, shown below in Figure 2, NoName057(16) claimed that the UK government is considering giving over £8 billion worth of Russian assets to Ukraine. The post cites an article by The Times, which was first published in December 2025. The article states that UK ministers would be prepared to give £8 billion of Russian assets frozen in the country to support Ukraine, warning that Russia’s president Vladimir Putin is an active threat to the UK’s citizens, prosperity, and security. It also stated that London is in talks to form a fund of up to £100 billion with its partner to provide military support to Ukraine.

NoName057(16)’s description of the UK as “Russiaphobic” particularly highlights the negative sentiment these hacktivist groups have towards geopolitical developments against Russia.
On 6 January 2025, the groups continued to target the UK via DDoS attacks. Server Killers claimed additional attacks against Darwen Borough Council, the Department of Justice, Ealing Council, Suffolk County Council, Tonbridge and Malling Borough Council, and the Air Accidents Investigation Branch. Similarly, NoName057(16) claimed attacks against the East Anglian Local Government Authority (LGA), the City of Blackburn, and Leicestershire County Council. Additionally, pro-Palestinian group DarkStorm joined NoName057(16) and ServerKillers’ operation, claiming attacks against London Oxford Airport, Blackpool Airport, Norwich Airport, Bournemouth Airport, and Exeter Airport. The group’s Telegram post about these attacks can be viewed in Figure 3.

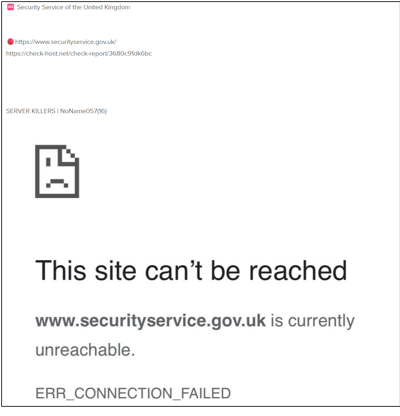
Further attacks were observed as part of #OpUK on 8 January 2025. Specifically, NoName057(16) continued to target local councils such as East Suffolk Council, City of Brandon, Suffolk Chamber of Commerce, City of Dover, Tendring Borough Council, Aldermore bank, Leumi UK, East Cambridgeshire District Council, Coventry Building Society, Harwich City Council, and Hemel Hempstead Town Portal. ServerKillers also made a new attack claim against the Security Service of the United Kingdom (MI5), as shown in Figure 4.
Releasing a statement on 9 January 2026, NoName057(16) claimed attacks against the National Rail Network of the United Kingdom, Devon County Council, Sterling Council, Buckfastleigh Town Council and Town Hall, Manufacturing Technology Association, Port of Felixstowe/England, and G4S, a British private military company. Its statement can be viewed in Figure 5 below.

The report cited by NoName057(16) from the UK Defence Journal was published on 6 January 2026. It statesthat the UK has confirmed that 13 Raven air defence and two prototype Gravehawk systems were sent to Ukraine. The Raven systems are air defence solutions which have specifically been developed for Ukraine and funded by the UK. The group’s statement that “practice makes perfect” indicates that it will continue to target the UK as long as it keeps providing funding and equipment to Ukraine.
NoName057(16) then went onto post two posts into its Telegram chat on 10 January 2026, as highlighted in Figures 6 and 7.
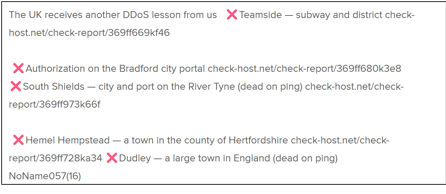

The group then went on to make another statement on 10 January, citing a roadmap which was agreed between the UK and Ukrainian defence ministers the day before.
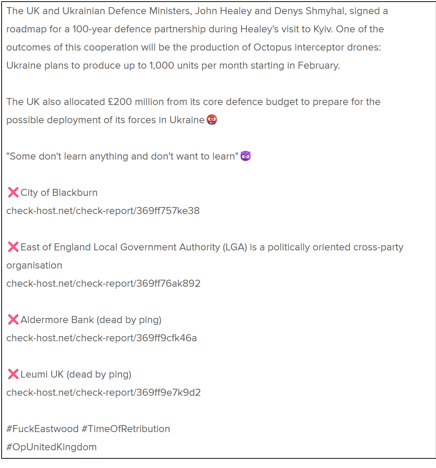
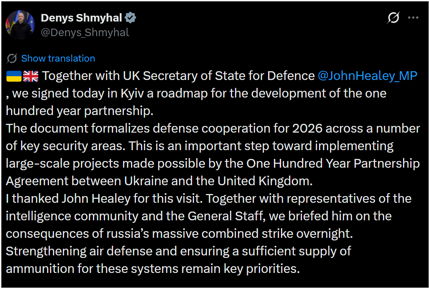
The roadmap was signed by UK defence minister John Healey and his Ukrainian counterpart Denys Shmyhal to develop the partnership between the two countries. First announced on X (formerly Twitter) by Shmyhal, the document outlines the defence cooperation priorities across key security areas in 2026. It also outlines the opportunity for large-scale projects under a 100-year partnership agreement between the UK and Ukraine.

In particular, NoName057(16) has used the announcement that more Octopus interceptor drones will be produced per month as another justification for its attacks. This has previously been observed in other posts where military equipment has been sent by the UK to aid Ukrainian defences.
The group then went onto make further attack claims against East Cambridgeshire District Council, the Coventry Building Society, Harwich Borough Council, Hemel Hampstead city portal login, National Rail Network of Great Britain, and Stirling Council on 11 January 2026. These are highlighted below in Figure 11.
As with prior claims by the hacktivist, the language used highlights the group’s motivation as targeting the UK for the help it has given to Ukraine. As previously discussed, this indicates that NoName057(16) and other hacktivist groups are unlikely to cease targeting the country in the near future. In particular, this targeting will continue if there are further announcements of aid or military support to Ukraine. This is evidenced by various reports, such as one which announced that the UK is to allocate £200 million to fund preparations for the possible deployment of troops to Ukraine.
Analysis of the attacks
Hacktivist groups often aim to target government or related organisations with disruptive attacks to bolster a belief or make statements. This can lead to a decrease in public trust in these companies, as the groups are able to publicly display the purported weaknesses of impacted organisations or websites.
The hacktivist groups primarily appeared to target local organisations at the beginning of #OpUK. However, the progression of attacks highlights how the hacktivists evolved their victimology to include the financial and transportation sectors. This is likely due to both NoName057(16) and ServerKillers aiming to cause as much disruption as possible to UK organisations, particularly if they are involved in the country’s infrastructure. The targeting of the National Rail Network in #OpUK particularly illustrates this. Additionally, the presence of victims such as Tameside and Bradford city across NoName057(16)’s Telegram posts suggests there has been repeat targeting. This may be due to the fact that the group has had previous success in targeting the websites, leading to the repeated attacks to bolster its claims. Alternatively, the affected entities may not have implemented the appropriate defences for DDoS attacks since the original incident. In either instance, it means that the service disruption caused by this campaign can be extended by the hacktivist groups.
The repeated inclusion of the hashtag “#FuckEastwood” in these #OpUK Telegram posts likely refers to the Europol operation which was conducted in 2025. Operation Eastwood involved international law enforcement actions against NoName057(16) and specifically targeted the group’s members and its infrastructure.
These attacks also demonstrate how hacktivists will often conduct attacks even if no action has been taken by its target. Specifically, the UK’s proposal to send the sum of money from frozen Russian assets has not yet occurred. The impact of these attacks has not just affected government services as a result, with organisations from different sectors being targeted. This once again demonstrates how hacktivists will aim to cause as much disruption as possible. As such, it is not just larger organisations which may be targeted in #OpUK if it continues in the future. Small businesses and other entities can also be affected in DDoS attacks, leading to operational downtime and reputational damage. This operation also demonstrates the cyber impact of the ongoing Russia-Ukraine war, where attacks are conducted not only to either hinder Russia or Ukraine’s military operations but also the support that can be provided to each country by their allies.
Get Started with CYJAX CTI
Empower Your Team. Strengthen Your Defences.CYJAX gives you the intelligence advantage: clear, validated insights that let your team act fast without being buried in noise.




