Introduction
It is imperative to understand the threats and vulnerabilities facing one’s organisation to mitigate the associated risk of a cyberattack. We are regularly asked to define the biggest cybersecurity challenges. Inevitably, they are the same: vulnerability management to reduce the attack surface; phishing attacks (which still account for over 90% of initial compromise and the associated risk of malware infection, credential theft and data breach); and insider threat. We will outline each of these issues, providing some simple mitigation measures aimed at preventing an incident and the potential for financial loss.
Vulnerabilities
In May, the Cybersecurity and Infrastructure Security Agency (CISA) released a list of the top 10 most exploited vulnerabilities from 2016-2019.[1] The vulnerability that draws the most attention, CVE-2012-0158, has been a long-time favourite of Chinese threat actors. It was first reported in 2012 and is still being actively exploited eight years later.
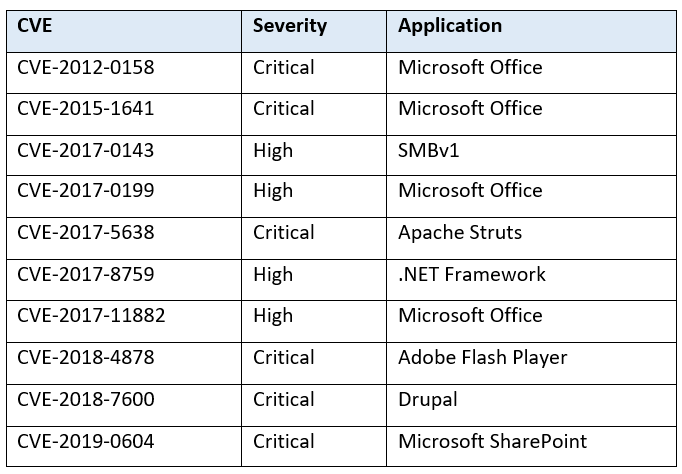
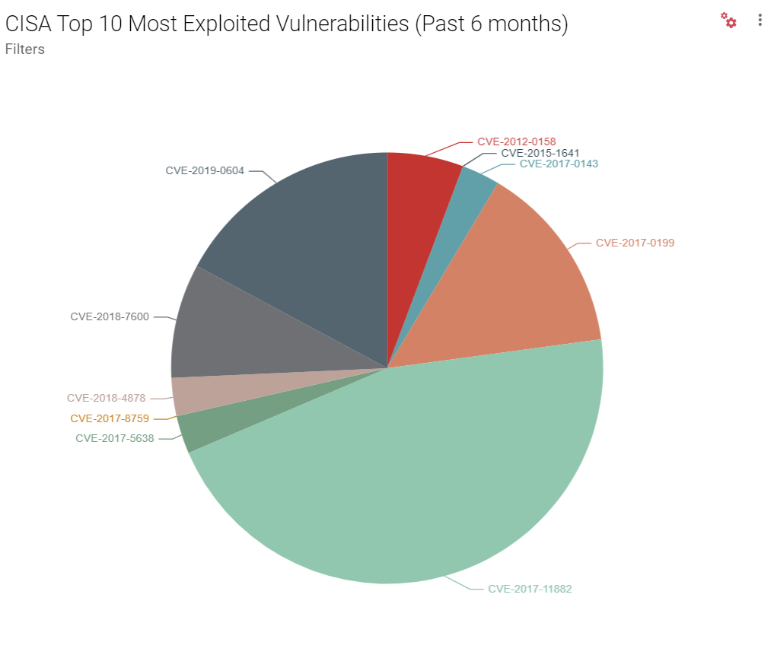
More recently, the National Security Agency (NSA) warned that multiple state-sponsored Advanced Persistent Threats (APTs) had weaponised several vulnerabilities that could be exploited to compromise Virtual Private Network (VPN) devices.[2] This has been a particularly important issue during the COVID-19 pandemic, when more people have been working remotely.
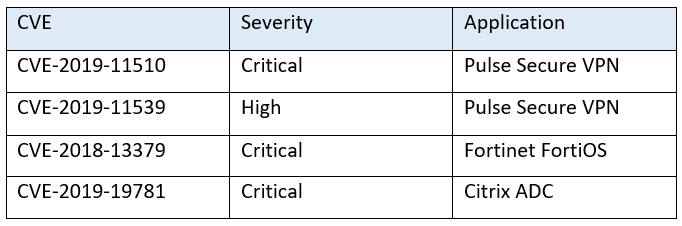
In March 2020, FireEye reported a massive global campaign being conducted by Chinese state-sponsored actor APT41 targeting 20 different sectors, including finance, transportation, energy, pharmaceutical and government organisations. The threat actor specifically leveraged an exploit for CVE-2019-19781 (shown in the above table) to compromise Citrix servers and install a backdoor.[3]
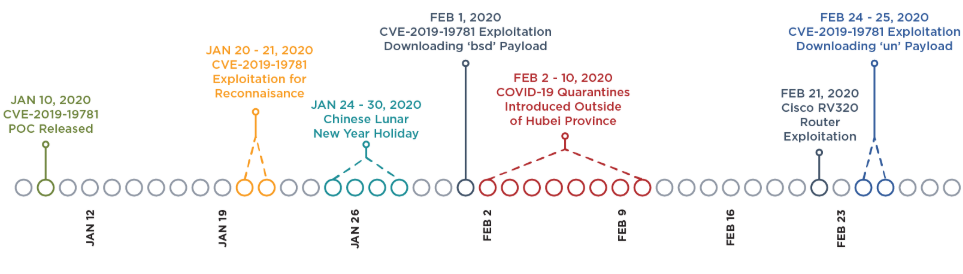
Timeline of key events (Source: FireEye)
The threat actor carried out reconnaissance just 10 days after the Proof Of Concept (POC) was released and, then shortly thereafter, moved to weaponization, delivery and exploitation. This activity illustrates the importance of the timely application of patches across your infrastructure.
Vulnerability management should be at the top of every CISO’s list, ensuring your infrastructure is clear of critical flaws, especially the ones listed in the CISA Top 10 and those being weaponised to compromise VPN devices.
Maintaining scheduled vulnerability scans and ongoing monitoring of your public-facing infrastructure is imperative. The goal here is to reduce your attack surface as much as possible to prevent an incident.
Ransomware trends
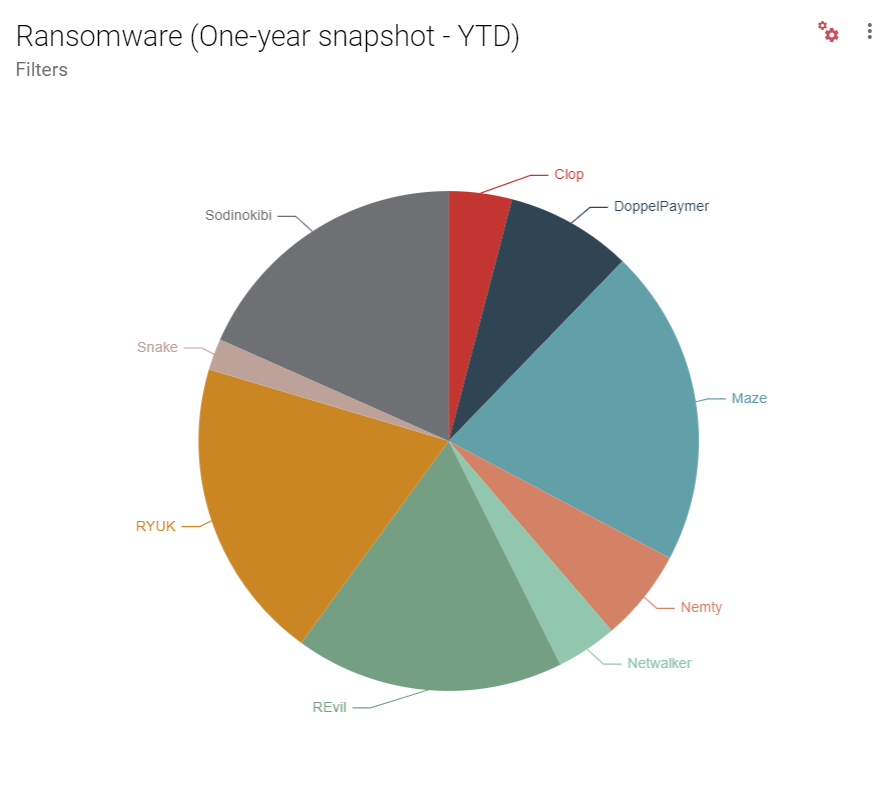
File-encrypting ransomware Trojans have been in wide circulation for nearly a decade, with initial POCs detected as long ago as 1996. Since then, ransomware has advanced significantly in its reach, sophistication, and Tactics, Techniques and Procedures (TTPs).
Over the past year, we have seen a sharp increase in attacks in which ransomware has been deployed in combination with data exfiltration tactics, with lists of successful attacks posted to blog sites on the darknet. In many cases, a third-party supplier has been hit, resulting in tangential exposure to clients.
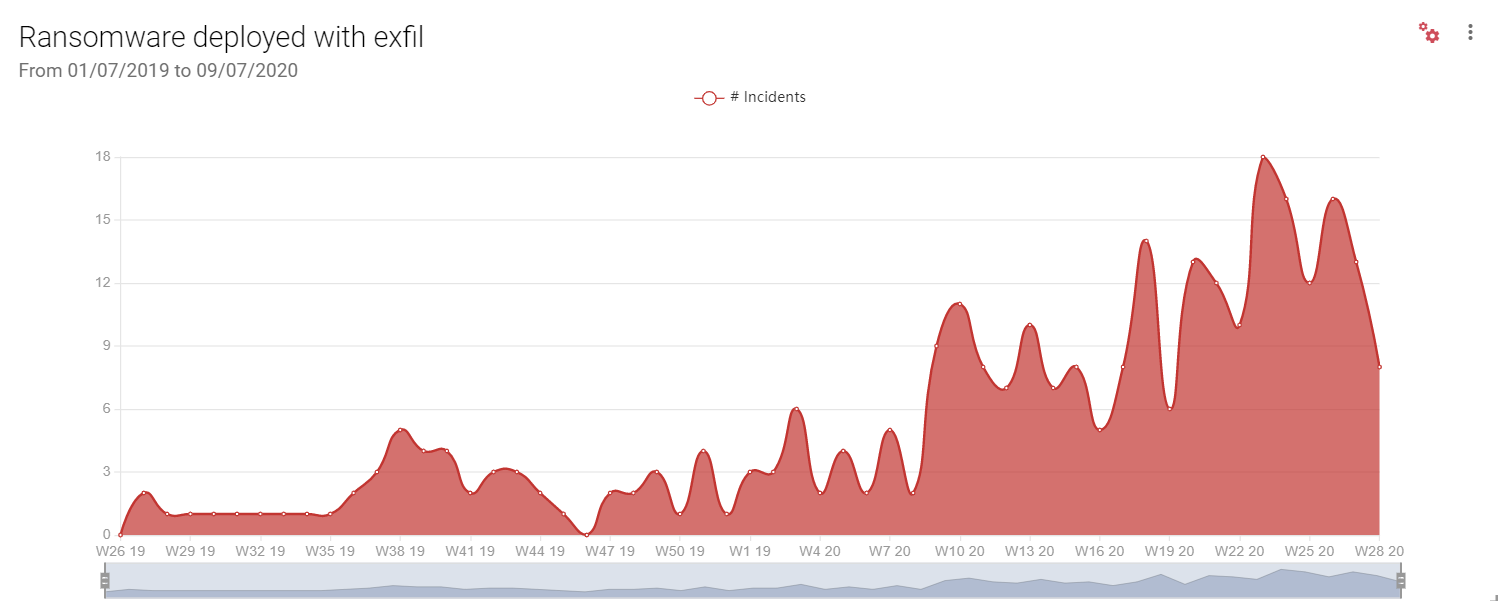
Cybercrime operators such as those distributing the Maze ransomware are well-organised and target specific organisations for maximum impact and profit.
IT service provider Cognizant, for example, was hit by Maze in April this year. With annual revenue of $16.8 billion in 2019, Cognizant is a prime target. The company will now need to spend as much as $70 million on the remediation of damage caused by the attack. [4] Although it is not clear what the attack vector was in this case, we do know the operators of the ransomware distribute it using exploit kits, phishing attacks and Remote Desktop Protocol (RDP) exploitation. Maze has heavily impacted organisations in at least twenty different industry verticals across the globe.
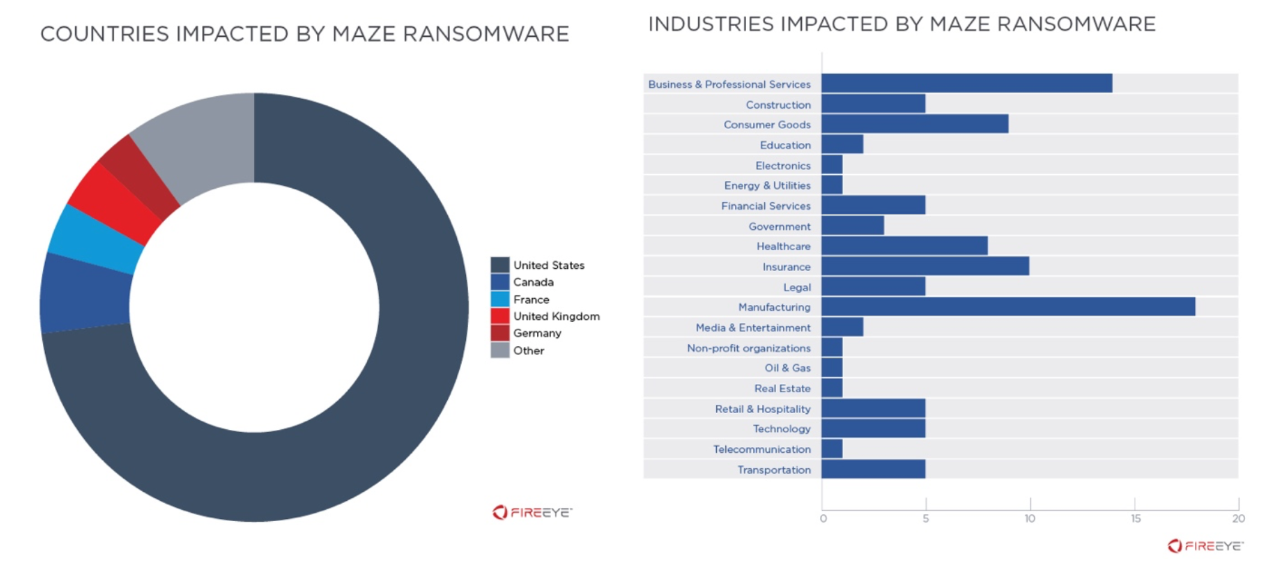
Source: FireEye[5]
Ransomware may be deployed using a number of attack vectors: the top three in 2020 according to incident response data are RDP compromise, phishing, and software vulnerabilities. [6] A recent scan shows over 4.8 million exposed RDP endpoints, so there are plenty of potential targets on which to carry out an attack.
There are some basic ransomware mitigation measures that must be in place in your organisation:
- Maintain regular system and data backups and ensure they are stored offline. The last thing you want is to get hit with ransomware and to have your data encrypted as well as your backups.
- Awareness training: sometimes your first line of defence is your end-users. Ensure they understand what to look out for and that they are fully aware of the associated risks. Make them an integral part of your security strategy.
- Email security solutions: of course, we do not want to put too great a burden on end-users, so it is important also to have a solution that scans and quarantines any malicious emails.
- Understand your attack surface:
- Are you running endpoints with RDP access, and if so, are they secured with both strong passwords and two-factor authentication (2FA)?
- Have you run a recent vulnerability scan against your infrastructure? And do you have ongoing monitoring to ensure there are no critical vulnerabilities that could be used to exploit your environment? Remember, CVE-2017-0143 [SMBv1 vulnerability] allowed for the WannaCry Ransomware to spread across networks and remotely compromise systems all over the world.
Phishing and Business Email Compromise
The FBI reported 23,775 complaints and losses of $1.7 billion stemming from business email compromise (BEC) in the USA in 2019.[7]

2019 Internet Crime Report [7]
This trend has continued in 2020. Earlier this month, it was widely reported that the United States had extradited Nigerian cybercriminal, Ramon Olorunwa Abbas, from the United Arab Emirates in relation to BEC campaigns in which he allegedly scammed unsuspecting victims out of millions of dollars.
Nigerian cybercriminals are well-known for operating BEC campaigns, so this latest development should not come as a surprise. We tracked an actor back in 2017 who was targeting one of our clients in a classic BEC attack. Actors will normally target organisations with high turnover to maximise their profits. They will carry out full reconnaissance to understand their target, accessing social media accounts and any public information to ensure the success of their attack delivery and exploitation. And they will set up shell companies to establish a sense of legitimacy.
In 2017, these actors were not particularly sophisticated. Over the years, however, they have improved their TTPs. Recently, there has been a link between the activity in which Abbas was involved and that of the state-sponsored group, FIN7. This financially motivated threat actor has been around since 2015 and primarily targets retail, restaurant and hospitality sectors. They too have been known to set up shell companies to mask their operations.
Phishing campaigns and associated tactics have become much more focused on business applications used across organisations, particularly Microsoft O365, which is extremely easy to imitate and is familiar to the end-user, so success rate tends to be a lot higher.
BEC campaigns are inherently targeted, so it is critical that your senior management (especially those in charge of finance) do their part in preventing a compromise. Some simple steps to reduce exposure of publicly available information and security hygiene can go a long way to preventing a successful attack:
- Be mindful as to how much is shared across social media and, at the very least, lock down privacy settings.
- End users should be participating in awareness training, and perhaps sent a mock campaign to test their readiness.
- Use strong passwords (and preferably a password manager) with two-factor authentication on all devices when accessing business applications.
- Communication is critical: whenever large transactions are involved, pick up the phone and contact the person who requested it.
Once an account has been compromised, the next phase of the attack will focus on mailbox reconnaissance; the threat actor will search for email threads that have mentions of financial transactions and attempt to intercept and redirect funds. This is the point at which the real damage can be done. It is extremely important for those employees involved in moving money to be wary of unusual requests and changes to account details. As noted above, the advice is to pick up the phone and confirm transaction requests.
Insider Threat
The Ponemon Institute reports that the annual cost of an incident related to insider threats can reach $11.45 million a year. [8] In terms of trends, reports have been mixed. The 2020 Verizon Data Breaches Investigations Report noted a significant drop in privilege misuse from 23% in 2019 to 8.7% this year. [9] This is, of course, a welcome statistic, but it is just one indicator. There are other actions that align with insider threat activity, including employees that unwittingly get caught up in an incident or make a mistake that results in financial loss.
According to the 2020 Cost of Insider Threats Global Report conducted by the Ponemon Institute, there has been an upward trend in both negligence and intentional malicious behaviour as shown in the figure below. [10]
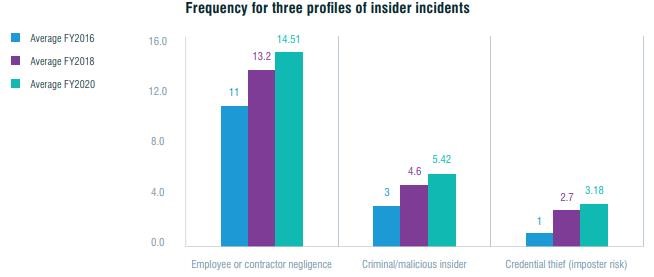
Source: 2020 Cost of Insider Threats and Global Report
In the face of the COVID-19 pandemic, we can expect a further rise in insider threat activity due to a number of factors. More employees than ever before are working from home and are unable to be monitored as closely. This coupled with the possibility of redundancy may make nefarious activity against their employer more attractive. Further, we have noted many instances in which threat actors are capitalising on the pandemic to socially engineer their victims.
Some simple measures to prevent insider threats include:
- Ensure employees understand and sign security policies (both systems and physical)
- Monitor your network for unusual behaviour
- Conduct risk assessments and regular systems audits
- Ensure separation of duties and mandatory holidays
- And, of course, treating your employees well goes a long way to preventing them from becoming disgruntled and contemplating malicious behaviour within your environment.
Conclusion
This report has outlined some of the major risks and threats to organisations, some of which have the potential to cause tremendous financial loss. There are many sophisticated threat actors who are constantly improving their TTPs to maximise impact, cause greater disruption, and increase their profits. There is no panacea, but there are some simple takeaways that will enable you to better protect your assets. As always, these involve a defence-in-depth strategy to secure your environment; deploying technical security controls; establishing vulnerability management and infrastructure monitoring; and ensuring your end users are properly trained and are practising proper cyber hygiene.
References
[1] https://us-cert.cisa.gov/ncas/alerts/aa20-133a
[6] https://www.bankinfosecurity.com/top-ransomware-attack-vectors-rdp-drive-by-phishing-a-14353)
[7] https://www.fbi.gov/news/stories/2019-internet-crime-report-released-021120
[9] https://enterprise.verizon.com/resources/reports/2020-data-breach-investigations-report.pdf
