Threat analysts at Cyjax have uncovered multiple mass credential harvesting campaigns that have recently been targeting cybersecurity companies, government entities, and organisations in a range of other sectors. Reverse engineering these campaigns revealed the attacker’s infrastructure and stolen data store.
Throughout July and August 2020, we detected two separate credential harvesting campaigns targeting accounts for Office 365 users and Outlook Web App (OWA). An example of the Office 365 phishing landing page can be seen below:
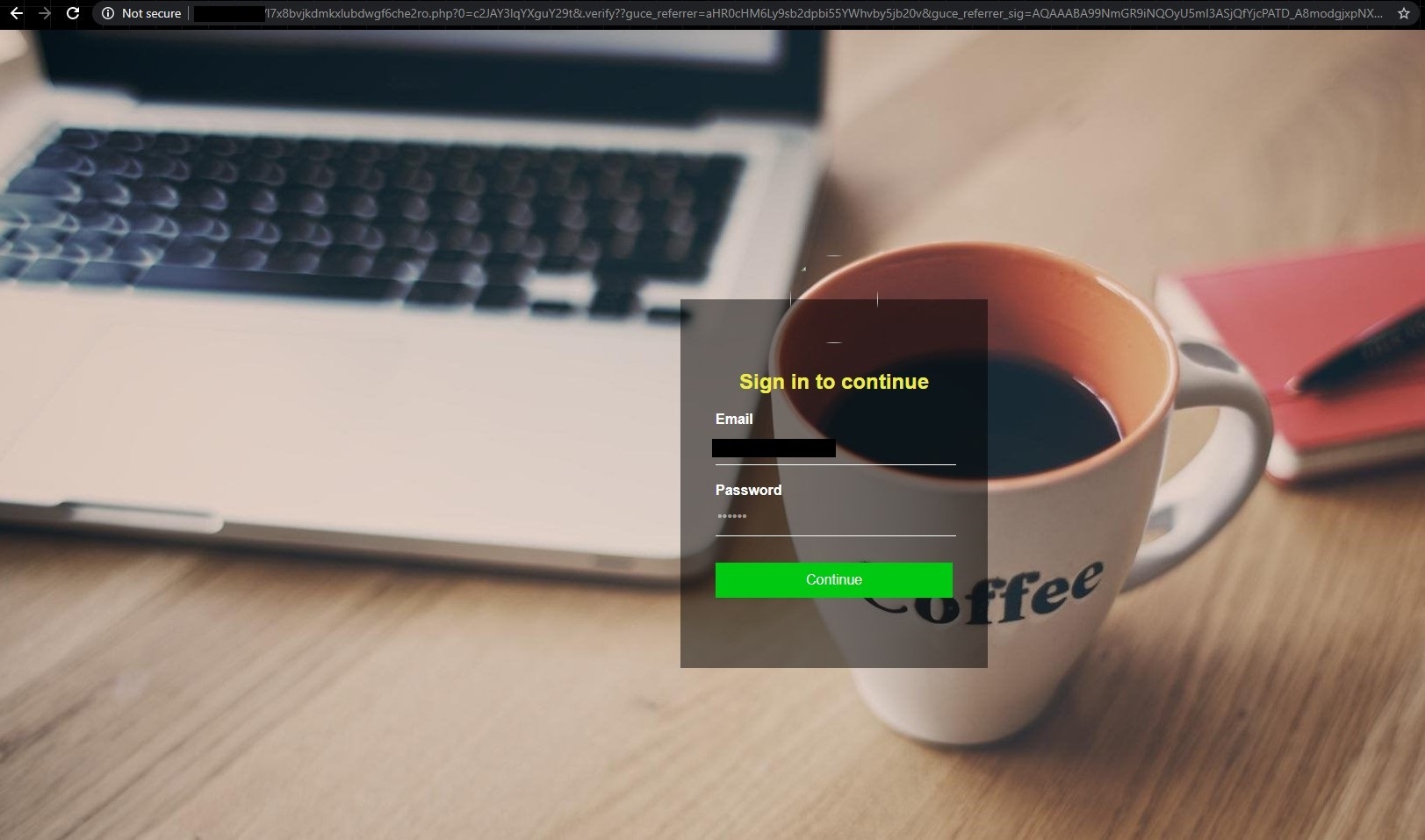
The attacks begin with targeted spam emails in which the recipient’s email address has already been filled out in the login page. This leads us to believe that the attackers had researched the companies they were targeting and acquired the email addresses either via open-source intelligence (OSINT) or from underground marketplaces and forums.
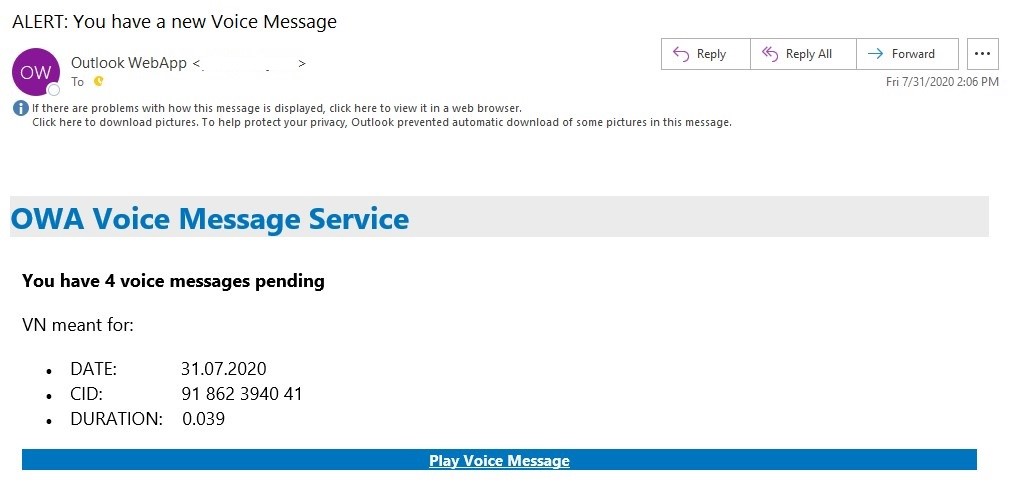
The spam emails arrive from SendGrid, an email marketing service, and masquerade as alerts stating “Alert: You have a new Voice Message” (see below) or “Mail storage capacity is Full” from the organisation for which the target works:
Our analysis of the infrastructure and the data store used in this attack revealed that over 1,500 users have already had their credentials stolen. The email addresses found in the logs belong to a number of public and private organisations from the UK, the US, Canada, Australia, Brazil, Malaysia, Saudi Arabia, and Indonesia. The following are organisations of note that were impacted in the first campaign we detected:
- Cybersecurity companies (Trend Micro, Fortinet, Sophos, Consilio, and Cyjax).
- US Department of Human & Health Services, US Department of Justice, and the Parliament of Australia.
The following victims were hit in the second campaign, from which we found the attacker’s data store:
- Governments email addresses from the US, the UK, Canada, Australia, and New Zealand.
- Telecommunications, water management, professional services, aviation, and more.
- Data stolen from these users included email addresses, passwords, IPv4, and geo-location.
These credential harvesting campaigns rely on publicly available cloud infrastructure that is available for free or at low cost. Both DigitalOcean and Namecheap were leveraged by the threat actors to host their infrastructure and the campaigns used SendGrid to distribute the spam emails. SendGrid is a useful asset for high-volume phishing campaigns such as this. Once an account has been verified with SendGrid, a user on a free trial can theoretically send up to 40,000 emails during their first 30 days. Fortunately, SendGrid has been swift to act against the malicious use of its infrastructure, swiftly taking down and mitigating the malicious links when they are detected.
Using the credentials after they have been stolen, the attackers behind this campaign may have gained access to the Outlook email clients, SharePoint Servers, and personal OneDrive storage. Business Email Compromise (BEC) campaigns are also a common second stage attack once credentials have been collected. These seek to gain access to financial and other sensitive information related to business operations.
Appropriate mitigations against threats such as these include enforcing the following:
- Multifactor Authentication (MFA)
- A password reset policy and password managers
- Report anything suspicious to the security team
- To never open links from unknown or untrustworthy sources
Indicators of Compromise (IOCs)
Threat actor-managed C&C domains:
app224.host
adkpd.com
wl.r.appspot.com
oragondesignstudio.com
sgclatam.com
ghhpc.net
gchps.net
