Cyjax analysts have uncovered a mass credential harvesting campaign targeting a wide range of sectors, including government, military, law enforcement, healthcare, finance, technology, manufacturing, and energy.
Key campaign attributes
- Malicious use of the SendGrid email marketing service to distribute URLs to the landing pages.
- Phishing emails leverage an image with an embedded URL that masquerades as a file attachment. Once clicked, it leads the user to the fake landing page.
- Landing pages are pre-filled out with the intended target’s email address – this is encoded in the SendGrid URL.
- The aim is to steal email account login pages. Notably, this is not an Office365-themed campaign.
- Phishing pages leverage logo[.]clearbit[.]com to use a target’s logo above the input fields.
- The attackers employed Google Firebase to host the landing pages and JavaScript to collect and exfiltrate the user’s input via HTTP POST requests.
- Once credentials are entered and collected, users are redirected to login[.]live[.]com – the legitimate Microsoft login page.
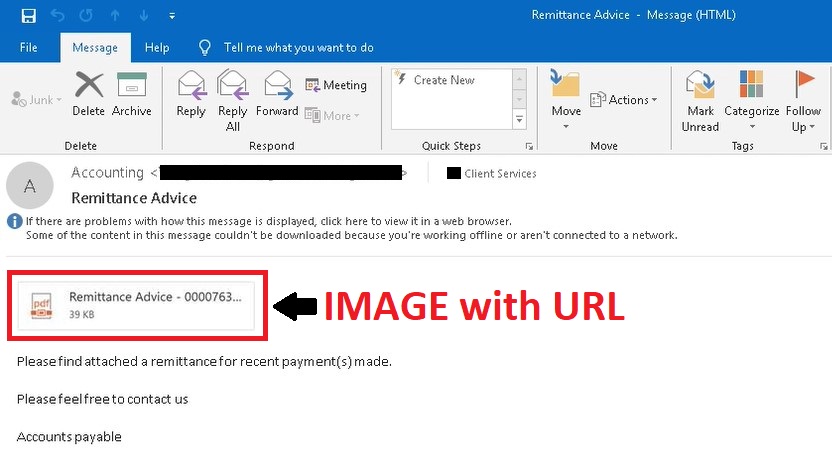
Fig. 1 – Example phishing email.
Victims worldwide
The victims we detected in this campaign were myriad, global, and of significance in their sector. Household names such as Apple and HP, GoDaddy, Transport for London, Deloitte and EY, Western Union, BBVA, Huawei and Verisign were all targeted. And in the US government, alone, the following departments were used:
- US Department of State
- US Social Security Administration
- US Health and Human Services
- US Small Business Administration
- US Army Corps of Engineers
- US Navy
- US Department of Education
- US Census
Other victims included:
- Port Authority of New York and New Jersey
- Leonardo Defence Systems
- GoDaddy
- Procter & Gamble
- DTE Energy
- Air Products & Chemicals
- Fifth Third Bank
- Banner Bank
- SBERBANK
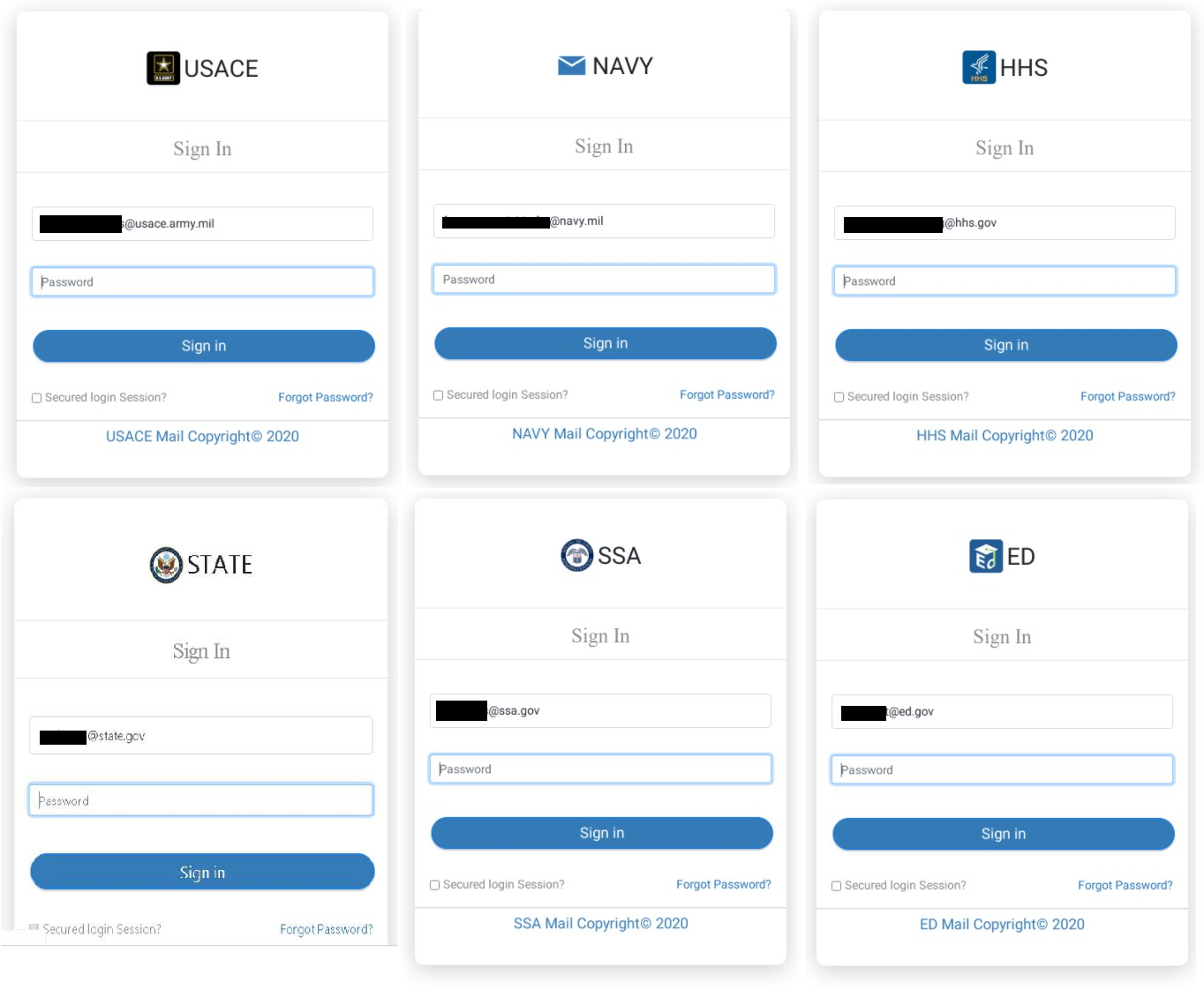
Fig. 2 – Example phishing pages targeting the US government and military.
Targeting
The government and military targets of this campaign suggest that the threat actors are targeting emails that may contain valuable information or intelligence. Although simple in concept, this operation could lead to a serious data breach, particularly given the evident research that was carried out by the malicious operators. If successful, these attackers may have gained access to Outlook email clients, SharePoint servers, or personal OneDrive storage. Business Email Compromise (BEC) campaigns are also a common second-stage attack once credentials have been collected. These seek to gain access to financial and other sensitive information related to business operations.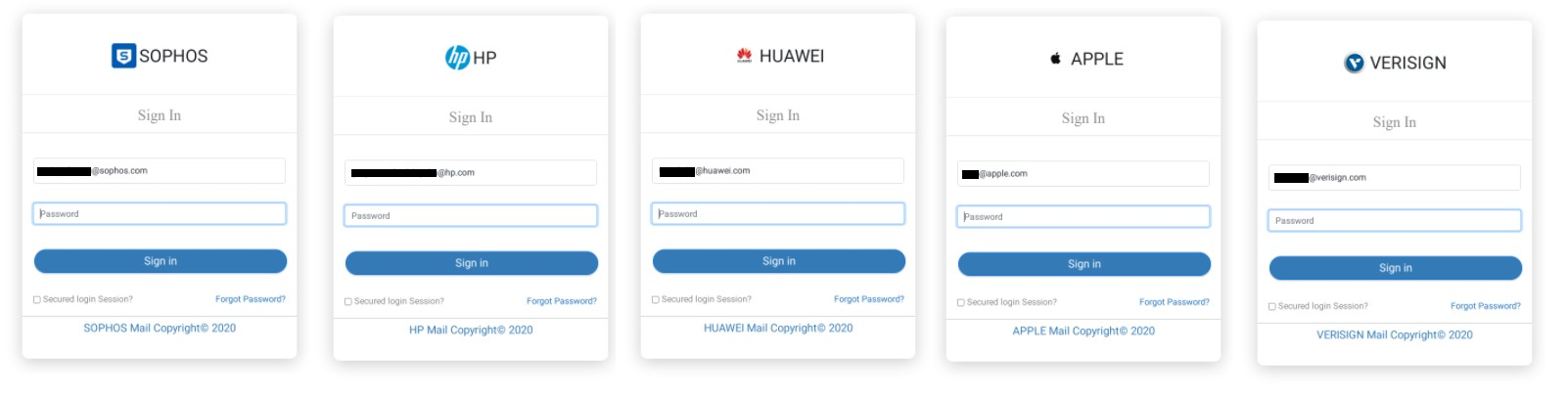
Fig. 3 – Phishing pages targeting technology firms.
OSINT analysis findings
We detected this phishing campaign in connection to an attack on one of our clients. Further OSINT analysis of the operation’s infrastructure revealed a mass credential harvesting campaign that we believe has been in operation since at least October 2020.
The use of SendGrid to distribute the phishing links is notable as it has become a common tactic amongst cybercriminals. The email marketing service is a useful asset for high-volume phishing campaigns such as this. Once an account has been verified with SendGrid, a user on a free trial can theoretically send up to 40,000 emails during their first 30 days. SendGrid is often swift to act against the malicious use of its infrastructure, taking down and mitigating the malicious links when they are detected. However, the attackers still have some success leveraging the service until the SendGrid campaign ID is reported for malicious activity.
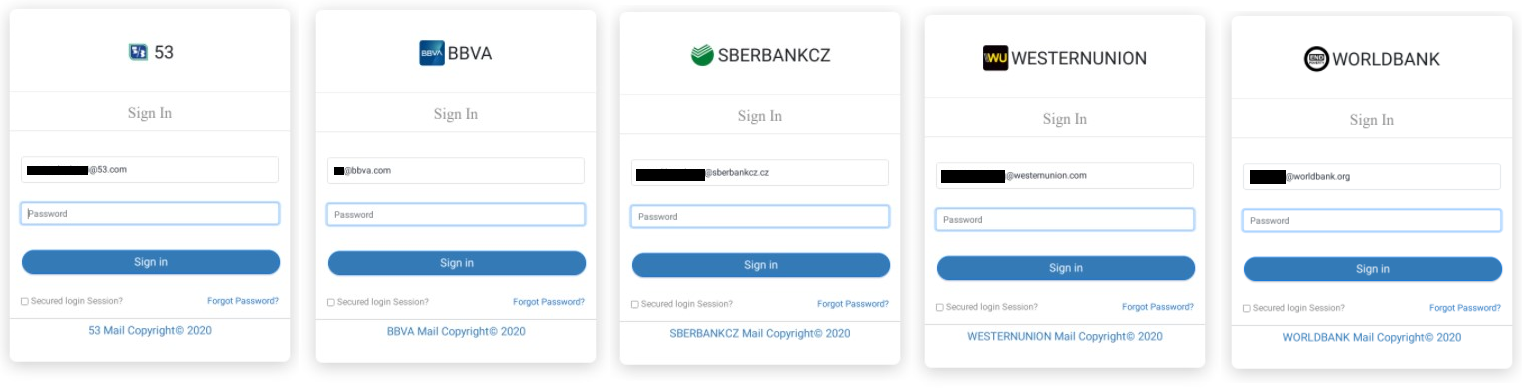
Fig. 4 – Phishing pages targeting the financial sector.
Mitigations
Appropriate mitigations against threats such as these include enforcing the following:
- Multi-Factor Authentication (MFA) using an authenticator application.
- A password reset policy and password managers.
- Implementation of a simple method for users to report anything suspicious to the security team.
- To never open links from unknown or untrustworthy sources.
IOCs are available for Cyjax clients.
