Phishing is nothing new: it has been around in some form since the earliest days of the internet and before – even postal mail had its own forms of phishing (and still does). Since the turn of the millennium, however, online services have boomed, creating an ever-increasing pool of targets for convincing phishing lures intended to steal information, alongside the burgeoning market for stolen credentials for various services and other information.
What is a Phishing kit?
In simple terms, a phishing kit is a website sold in an easy to deploy package (such as a .zip file) that can be deployed with little technical skill required. The kits are already themed to the service being targeted and normally require minimal configuration. Frequently, the phishing kits are “leaked” for free on forums or simply found and reused by other threat actors.
Stolen details are either stored in a text file on the server hosting the phishing page, to be collected later, or emailed directly to the phishing actor. From looking at the code powering various phishing kits we have acquired over time, we have found that kits carry out the same basic processing on the captured information, such as looking up the bank sort code and validating captured card numbers.
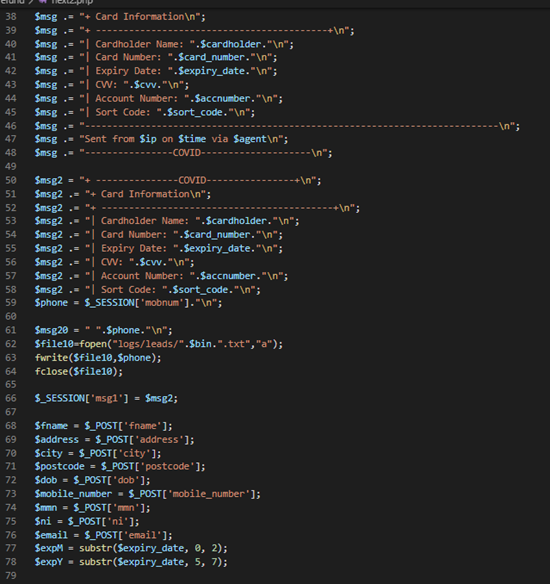
Fig. 1 – Code for processing stolen bank details taken from a phishing kit targeting UK bank details via a COVID lure.
Phishing during the COVID-19 pandemic
Phishing has spiked during the COVID pandemic as it has created a new, global, and frightening avenue for lures of different types, especially, in the UK, those themed around the government and the NHS.
Early on, NHS-themed contact tracing lures were often used, sent out via SMS encouraging victims to visit a link to an ‘NHS’ page designed to harvest email credentials and other personal details. Typical information targeted in these scams would include the victim’s name, address, and National Insurance number.
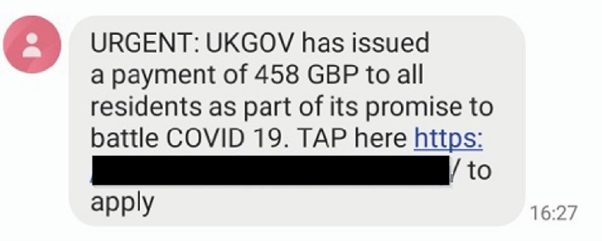
Later, we started to see lures themed around fines for breaking lockdown restrictions and now, almost a year into the pandemic, we are seeing campaigns using fake tax relief lures that claim the victim is owed money because of losses incurred or other pandemic-related financial issues. Both campaigns are focused on stealing bank account information and various personal details, as shown in the example below.
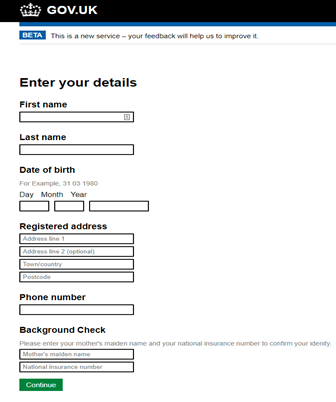
The first stage of the kit takes the victim’s personal details, some of which may also be used as alternative security information for other services:
The second stage of the kit targets the victim’s banking information. This may include full credit card information, including the CVV2, as well as associated bank account details:
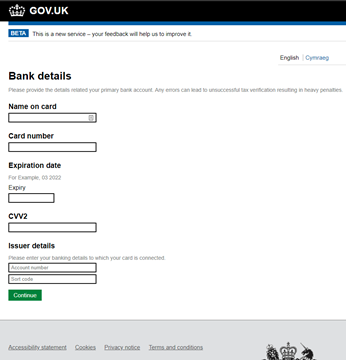
Many UK government-themed phishing kits use an almost identical design: this is quite possibly because the government’s publishing department has placed all of its design guides and assets online and made them freely available. Consequently, phishing kit creators have been able to follow these design rules and ensure the kits look as convincing as possible.
Due to the designs of these UK government-themed kits sharing so many assets, they have become relatively easy to find and report as fraud to hosts (though we could write an entire blog on the difficulty of getting hosts to respond). This became a serious issue for phishing actors: their pages were being removed before they could lure any victims.
We have recently seen an interesting new method used by the threat actors to combat this problem. Extra code is added to the phishing kits to make detection and removal more difficult. This new code first checks the hostname of the visitor derived from their IP address; if this hostname does not match a small list of known UK ISPs it will redirect the visitor to a news website such as BBC. If the hostname matches that of a UK ISP, however, a check is made against the visitor’s user agent; if this does not match a common pattern for a mobile device, again, the user is redirected.
if(strpos(gethostbyaddr($_SERVER['REMOTE_ADDR']), "threembb.co.uk") !== false){
if(preg_match("/(android|webos|avantgo|iphone|ipad|ipod|blackberry|iemobile|bolt|boost|cricket|docomo|fone|hiptop|mini|opera mini|kitkat|mobi|palm|phone|pie|tablet|up\.browser|up\.link|webos|wos)/i", $_SERVER["HTTP_USER_AGENT"])){
header("Location: refund/index?code=2");
}
else{
header("Location: https://www.bbc.co.uk", true, 301);
}}
Fig. 2 – Avoidance code example.
This also becomes an issue when reporting phishing websites as the customer service agent checking the website to confirm the report is valid is often just redirected elsewhere causing them to close the ticket as invalid, leaving the phishing page live and able to collect more victims.
Conclusion
As the pandemic continues the problem of COVID-19-themed phishing is likely to continue at the same rate or get worse. It is more important than ever for all users to be vigilant. Looking at some stats from our sources over the past seven days, roughly 150 individual phishing pages using a UK government theme were confirmed malicious in our sources, as well as more than 1,000 individual pages that were targeting the most popular UK banks – all essentially indistinguishable from the real thing. Next week roughly the same amount will be seen again. Exercise caution when inputting your data. These scams are only going to become more convincing as time goes on.
