Since early February, Cyjax analysts have been tracking a mass spam campaign masquerading as Royal Mail parcel delivery notifications. We have observed large numbers of malicious domains being registered each day, typically using Namecheap as registrar and hosting service rather than any others. Multiple varieties of attacks have been detected that use both Royal Mail-themed emails and landing pages to harvest personally identifiable information (PII), payment card data, and one-time passcodes (OTP) to bypass account authentication.
The malicious emails use the subject: “Fw: royal mail post” and inform the recipient that their “package is awaiting delivery” and that they must confirm the payment by clicking a link:
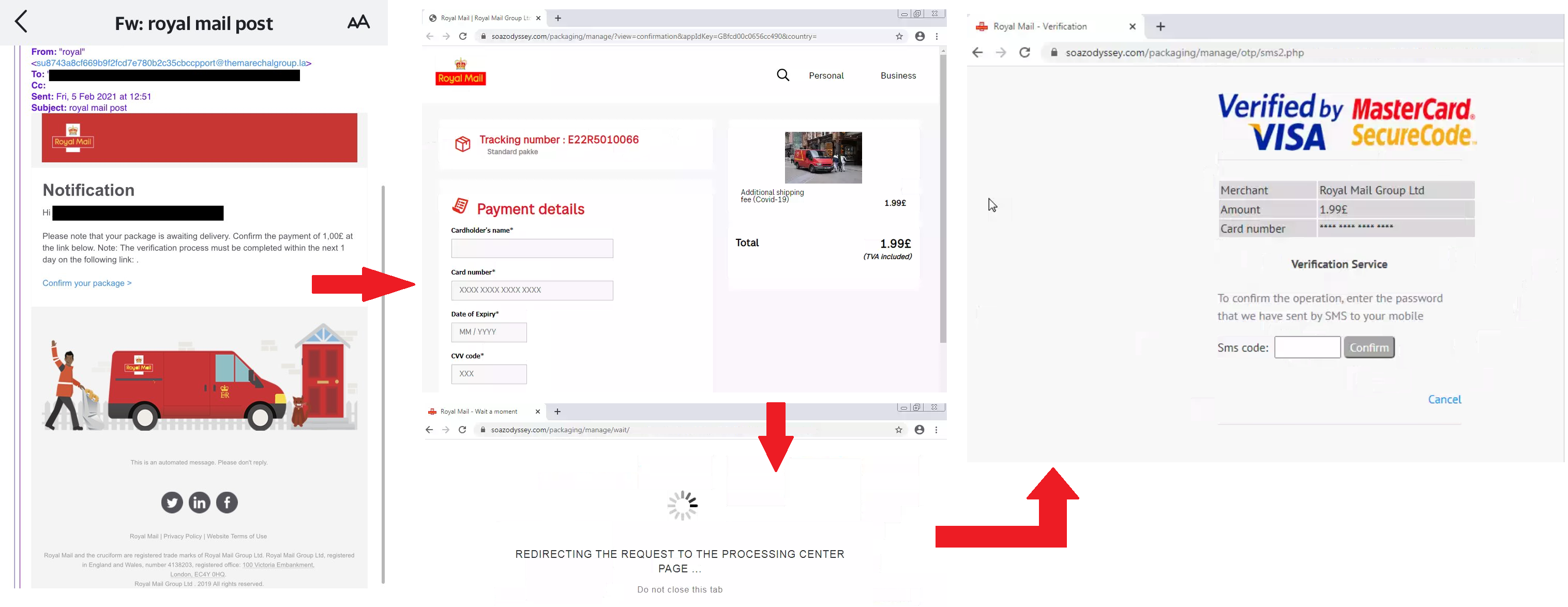
Fig. 1 – First Royal Mail phishing chain we detected in February.
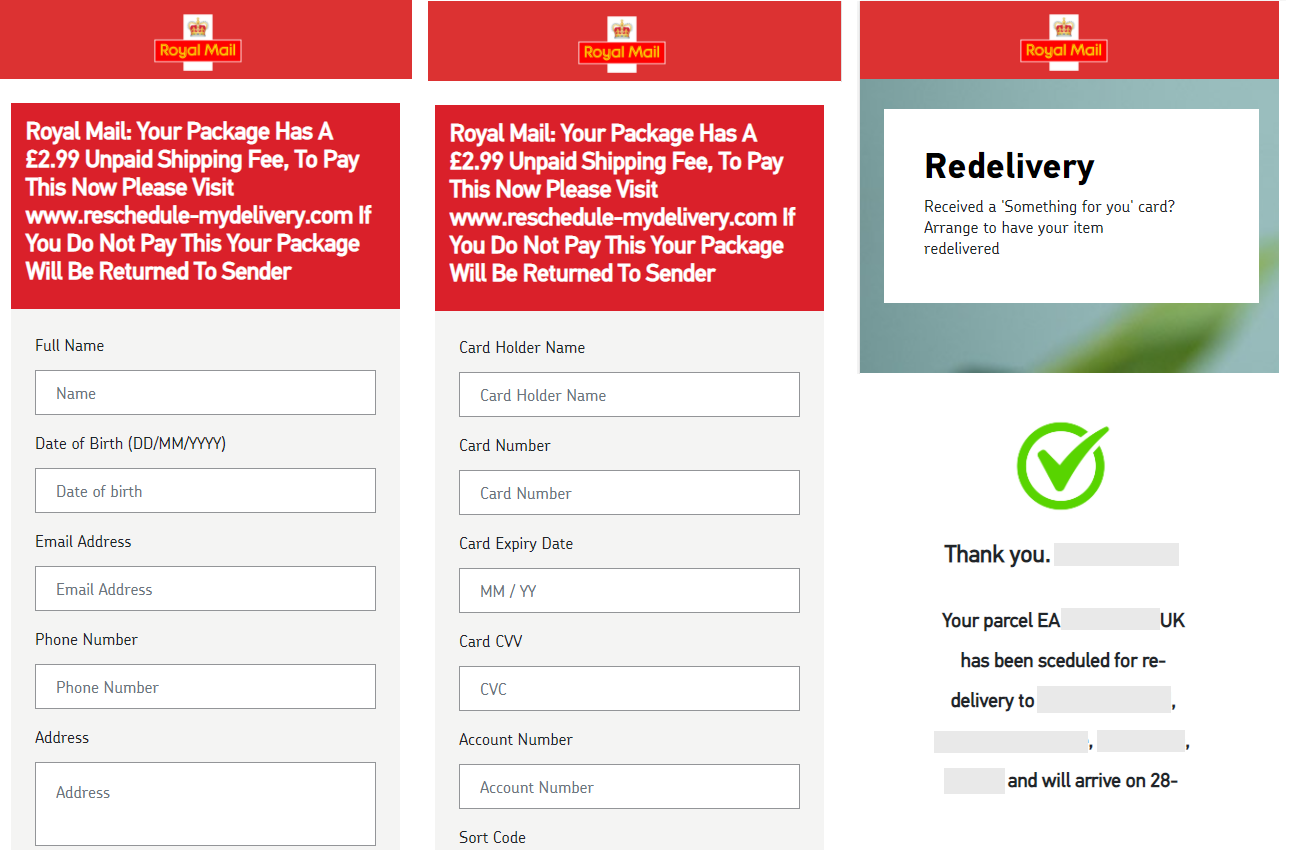
Fig. 2 – Second chain detected at the beginning of March.
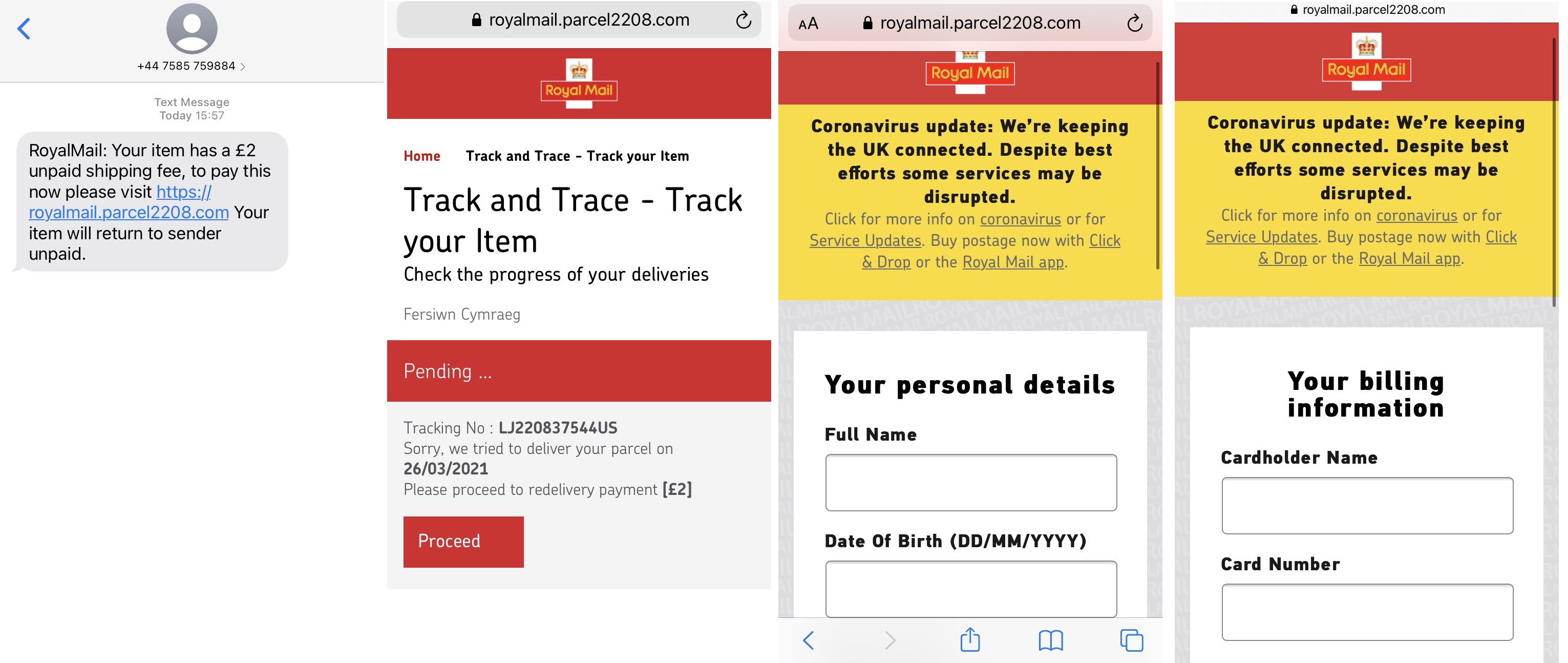
Fig. 3 – Third chain currently in use at the time of writing.
In March, we began to see wave after wave of Royal Mail-themed emails and SMS text messages using similar domains and landing pages. Between 1 January 2021 and 26 March 2021 we identified over 382 unique fully qualified domain names (FQDNs) masquerading as Royal Mail.
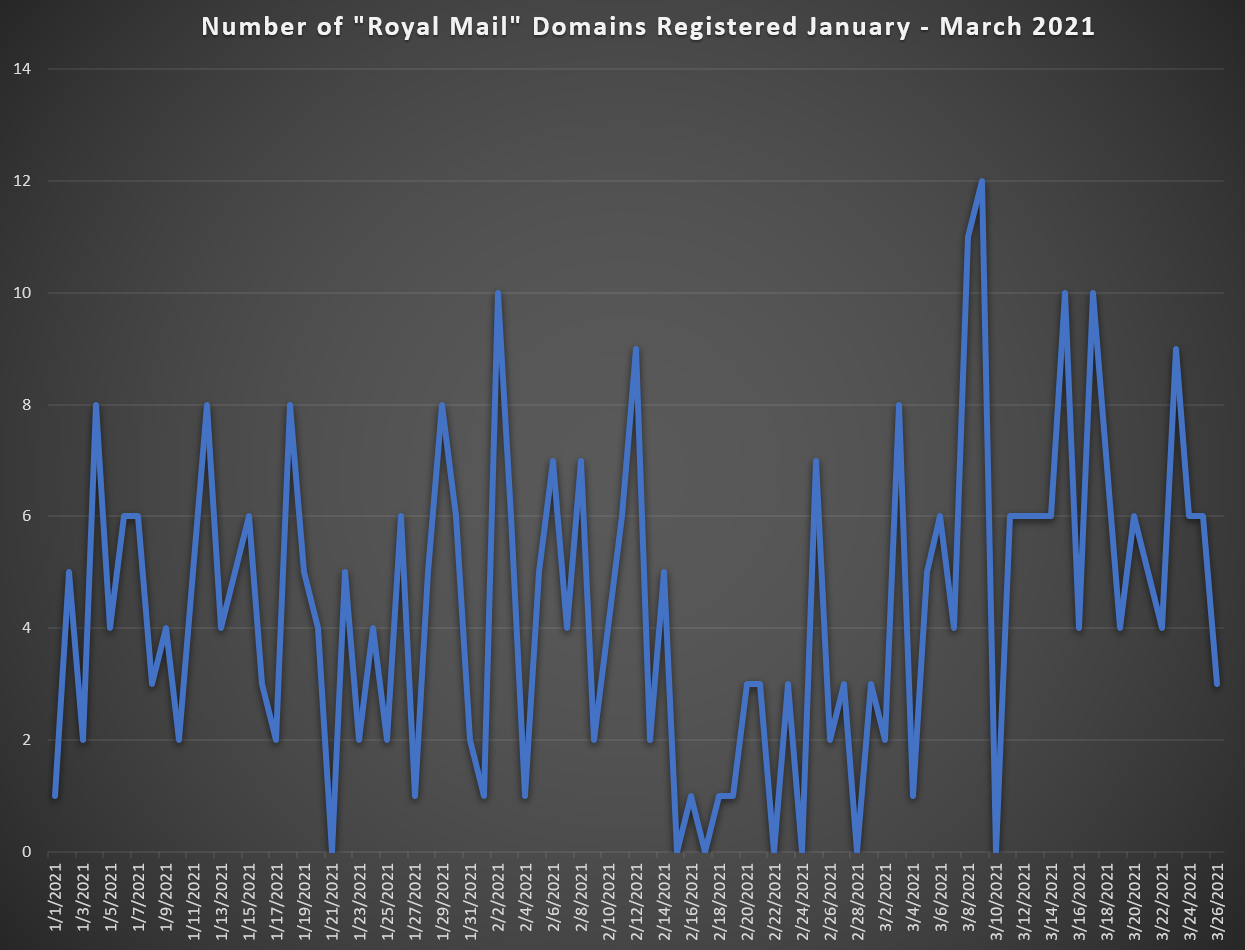
Fig. 4 – Frequency analysis of “Royal Mail” themed domain registrations.
Action Fraud, the UK’s national fraud reporting centre, shared that the malicious Royal Mail themed links had been reported to them over 1,700 times in one week. Clicking the link in the message takes them to a page that attempts to steal personal and card information, including name, date of birth, address, email address, phone number, card number, expiry date, CVV, account number, and sort code.
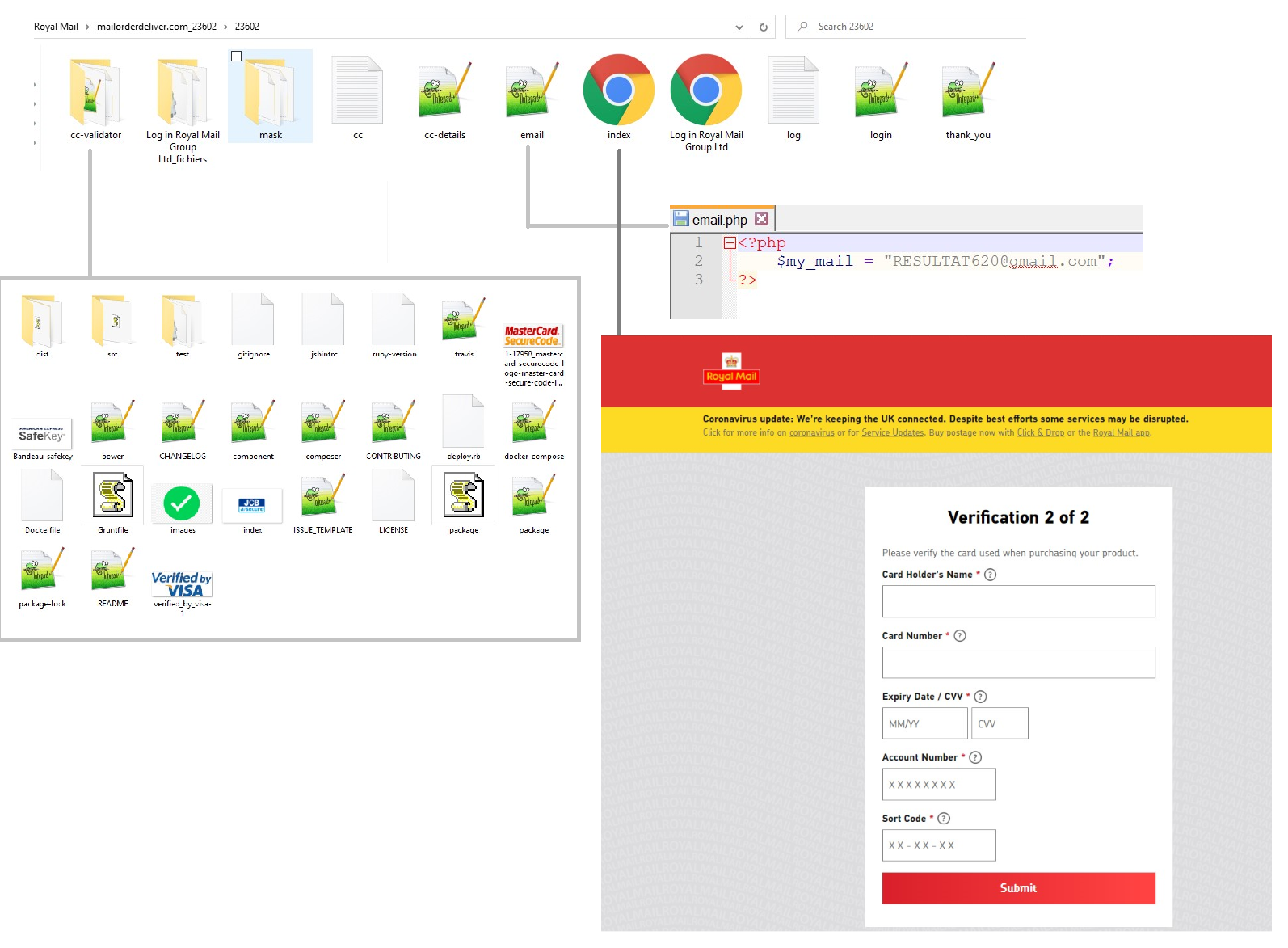
Fig. 5 – Files involved in a Royal Mail phishing kit used to create the landing pages.
Royal Mail is aware of this widespread campaign and shared the wording of 16 emails and text messages currently used by threat actors. Various tactics are employed to entice or pressure users into following the directions in the messages and relinquishing their credentials. The most common tactic is rescheduling deliveries, followed by customs fees, and warning users “actions will be taken if you do not pay this fee”. One reason for the success of many of these attacks was that the targets were expecting parcels to be delivered by Royal Mail. We expect this campaign to continue: the attackers are clearly developing more lures and still using this theme, suggesting that it has been successful for them.
These types of campaigns are orchestrated by well-resourced, financially motivated threat actors. The stolen data will either be directly used to defraud victims or sold on underground forums, group chats, or darknet marketplaces. The tactic of using parcel delivery notifications has only gained more traction since the beginning of the COVID-19 pandemic and online shopping becoming the only way for many people to purchase goods.
Sources:
https://twitter.com/actionfrauduk/status/1365228568402395142
https://www.birminghammail.co.uk/news/uk-news/royal-mail-issues-exact-wording-20125697
urlscan.io/search/#page.asn%3AAS22612%20AND%20filename%3Ajquery.payment.js
urlscan.io/search/#page.asn%3AAS22612%20AND%20filename%3Aexpress.php
urlscan.io/search/#page.asn%3AAS22612%20AND%20filename%3Aroyal
