The second quarter of 2021 has been a period of relative stability for darknet markets, with WhiteHouse continuing as the leading English-language market across the ecosystem. Conversely, darknet forums have experienced some degree of upheaval, which can largely be attributed to the outsized role of ransomware groups and the increasing attention being paid to such groups by government and law enforcement entities.
Banning Ransomware
In May, the largest fuel pipeline in the US, Colonial Pipeline, was hit by ransomware. It was revealed soon after that the DarkSide ransomware was responsible for the compromise. Due to the increased attention on ransomware groups following that incident, several darknet forums chose to ban ransomware groups from advertising on their platforms. At the time, many of these forums claimed the ban was due to the all-pervading nature of discussions about ransomware pushing out other topics. However, there was also likely a significant element of self-preservation driving this ban, since platforms seen to be supporting ransomware groups are likely to experience more scrutiny from law enforcement.
Notably, ransomware groups were not banned entirely from these forums, they were simply banned from publicly advertising their products. Consequently, many of the representatives of these groups have remained active on these forums – albeit in a reduced capacity. The short-term effects of this ban have been clear: to deny ransomware groups, particularly those utilising the Ransomware-as-a-Service (RaaS) model, a platform through which to promote their services. It is currently unclear if this ban will have any significant long-term effects on RaaS groups’ ability to recruit new members, though this seems unlikely as they can simply promote themselves on other platforms. Indeed, for well-known RaaS groups, this ban is likely to have little effect as they are established enough for potential recruits to seek them out. Conversely, this ban may ultimately hinder the growth of new RaaS groups, who may struggle to establish themselves.
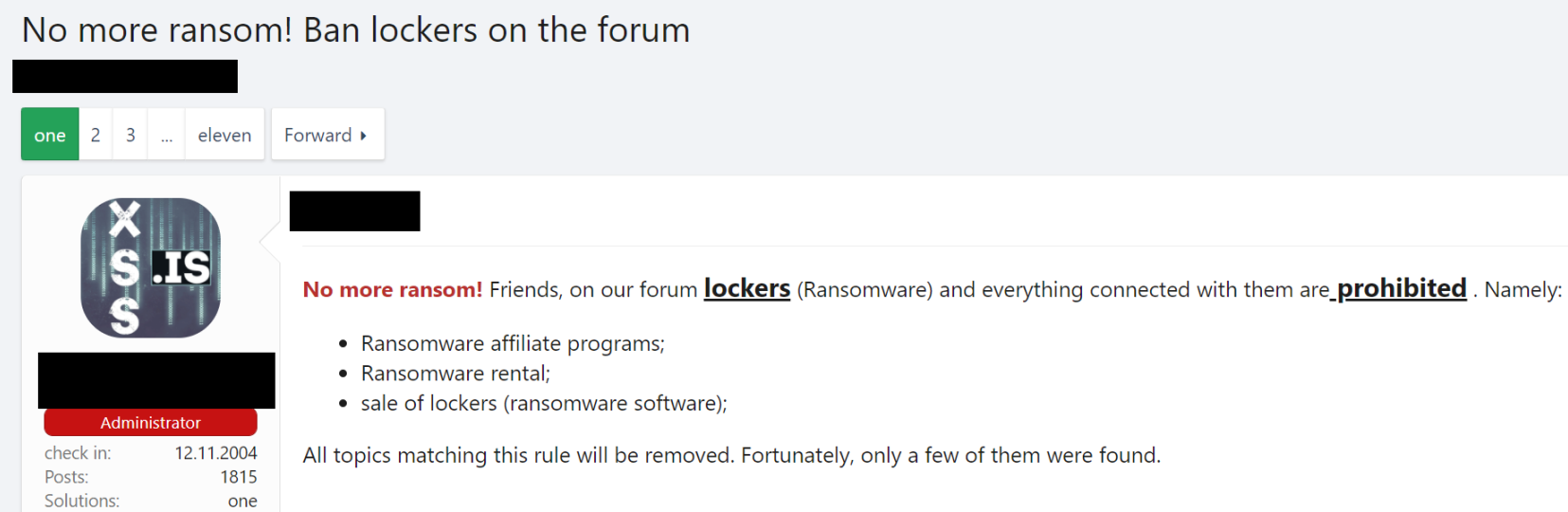
Fig.1 – The admin of a well-known darknet forum announcing the ransomware ban.
It is important to understand, however, that the surge in the number of RaaS groups was essentially due to a ‘perfect storm’ of different actors’ incentives aligning. A large proportion of criminal actors lacked the technical skills to develop malware themselves, so relied on malware and services provided by others. There were also developers who sold malware to these criminals as a one-time purchase, but quickly realised that they could make more money by formalising this into a subscription model. Rather than a one-time purchase, customers were increasingly asked to pay a fee for a set period. In exchange, developers provided the malware, updates and often a dashboard for customers.
This malware-as-a-service (MaaS) model became extremely popular, particularly among remote access Trojan (RAT) developers, often referred to on the darknet as ‘stealers’. Applying this model to ransomware was simply the next logical step for a system where the primary incentive is profit. Unsurprisingly this resulted in a surge in RaaS groups. The banning of ransomware groups from these forums does not fundamentally alter these incentives, so its broader impact on the threat of ransomware is likely to be limited.
Demand for Access
Over the past several months, there has been a notable decline in the number of access sales conducted publicly. Access sales are essentially where a user, referred to as an access broker, gains access to an organisations network, and then sells this access to another user who can monetize it. Naturally, the surge in RaaS groups led to an increase in demand for access, which we covered in our Q3 2020 Darknet Review (https://www.cyjax.com/2020/11/13/darknet-review-q3-2020/).
However, during the same period, public demand for access has increased significantly. Primarily, this comes in the form of users making generic posts that they will purchase access to organisations for fixed amounts. Some include additional criteria, such as the affected organisation’s revenue or sector of operations. Many of these users can be connected back to ransomware groups, suggesting this increase in demand can, in large part, be attributed to them.
On the surface, this appears to be a simple case of demand responding to a tightening of supply. However, it is notable that the public access sales which still occur are often conducted by relatively new access brokers, rather than reputable users who have been active for some time. We have identified evidence that some of these more reputable access brokers have been working directly with ransomware groups, either as well-paid affiliates or by offering them right of first refusal on any new access available. It is likely that this practice is responsible for both the absence of reputable access brokers and the subsequent increase in demand for access among ransomware groups.
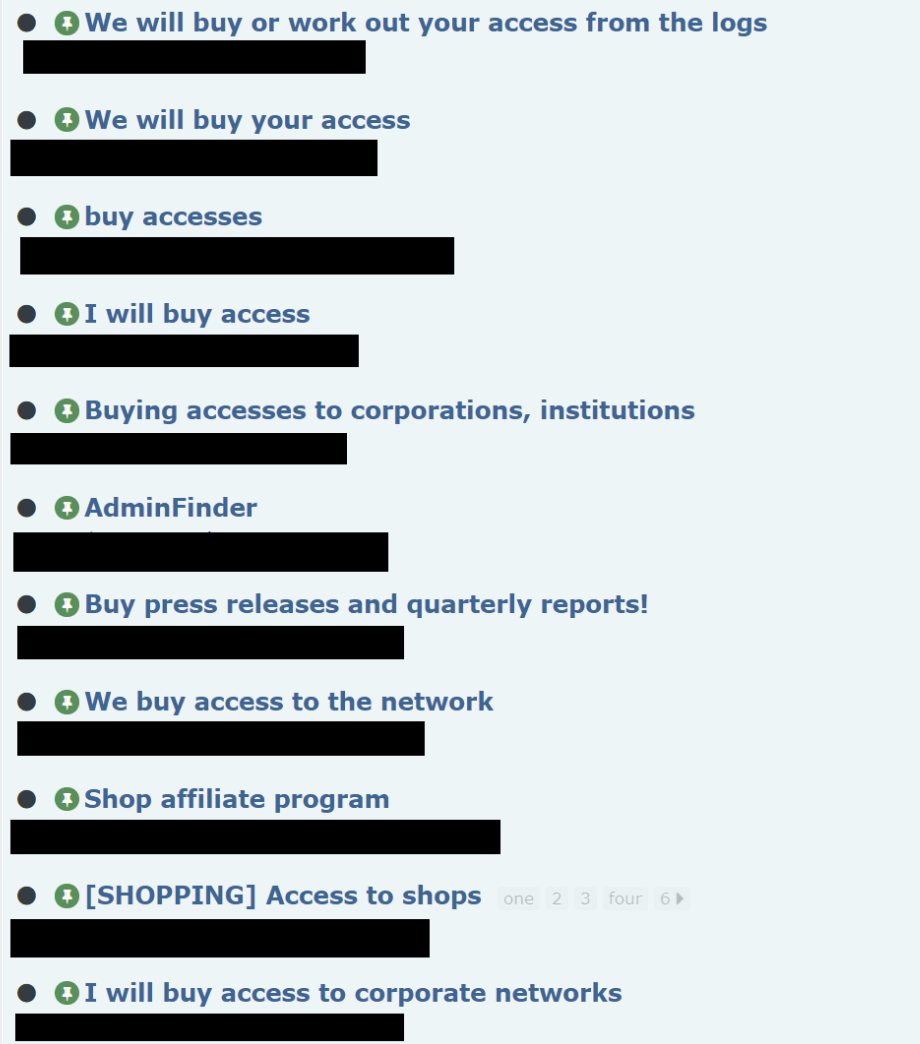
Fig. 2 – Multiple paid posts by users interested in purchasing access.
It is likely that this practice will continue for the foreseeable future. Ultimately, access brokers can make considerably more money working with ransomware groups directly, as opposed to selling access to an organisation for a relatively small sum and watching as that organisation is then held to ransom for potentially millions of dollars. It also simplifies these cybercriminals’ operations because they no longer need to engage in public access sales, with their attendant advertising, negotiations, and potential law enforcement attention.
Q3 and Beyond
The long-term effects of ransomware groups being banned from advertising on forums is not yet clear. However, over the past several months, multiple new ransomware groups have been launched, indicating it is having only limited impact. Moreover, the issue of the potential increased demand for access underscores the extent to which ransomware has created its own self-contained economy within the criminal market. It also demonstrates that ransomware is likely to continue playing a major role in the darknet community – despite being banned from forums.
For English language darknet markets, the landscape currently remains relatively static, with WhiteHouse continuing to lead, even as other markets increase in popularity. However, there have been several recent law enforcement operations targeting smaller darknet markets, including Slipp Le Monde Parallèle. As the popularity of the affected markets has been relatively low, the disruption to the darknet market landscape has not been severe. However, similar operations targeting larger markets are likely to result in far more significant disruption to darknet vendors and the broader market landscape.
