The most significant ransomware attack in July was the Kaseya attack conducted by the REvil (also known as Sodinokibi) ransomware group. The REvil operators exploited a 0day vulnerability in Kaseya’s VSA servers to bypass authentication measures and perform arbitrary code execution. Notably, this vulnerability had already been privately disclosed to Kaseya, though it remains unclear how the REvil operators identified it. The use of 0day exploits and supply chain compromise are extremely uncommon in ransomware attacks. However, the tactics appear to have backfired on the REvil operators: shortly after this attack, their infrastructure was taken offline and a decryptor has now been provided to Kaseya and its affected customers.
Other notable attacks from this past month include Arthur J. Gallagher (AJG), a large multinational insurance company. AJG was, in fact, hit in September 2020, but only disclosed this recently. Customer data was compromised, but neither the extent of the attack nor the name of the ransomware group responsible is known. Finally, US-based cloud hosting provider Cloudstar also recently experienced a ransomware attack. Again, the name of the ransomware group has not been disclosed and it is unclear if Cloudstar paid the ransom.
Aside from the REvil leaks site going offline (along with the rest of the associated infrastructure), multiple other ransomware leak sites have been launched this month. The operators of Babuk Locker have launched a new leaks site, whilst rebranding their old one to become a “forum dedicated to ransomware”. So far, this forum is relatively inactive. Avos Locker, a relatively new ransomware group, and CryLock, a group that has been active for many years, both also recently launched their own data leaks sites. That a relatively old and established ransomware group is now launching such a site underscores the extent to which data-theft and extortion is becoming an integral part of the ransomware business model. Finally, having re-launched their affiliate program at the end of June, the LockBit ransomware group has been exceptionally prolific over the past month, disclosing nearly 50 victims on its leaks site.
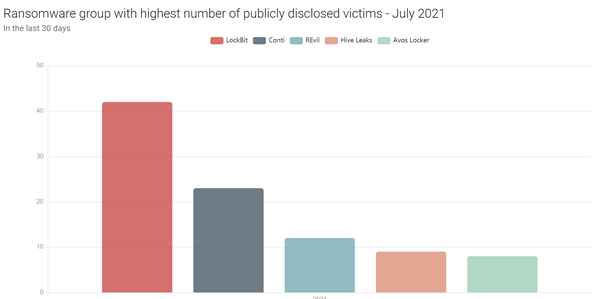
Fig. 1 – The ransomware groups with the highest number of publicly disclosed victims in July 2021
There has also been an increase in variants of existing ransomware strains being developed specifically to target VMware ESXi servers. This shift towards virtualisation has been ongoing for some time, and has been particularly noticeable in darknet forums where ransomware groups announce new updates to their malware. However, both the REvil, Babuk and HelloKitty ransomware groups are now actively using Linux variants of their malware specifically to target VMware ESXi servers. They are unlikely to be the only groups engaging in this practice, and we expect this shift towards virtualisation to continue.
