A wide variety of malware and threat actors target cloud and container technologies, such as Docker, Kubernetes, and Amazon Web Services. The two main techniques for initial access that are leveraged by threat actors against these technologies are misconfigured instances with unsafe ports open and improper access control, and users downloading malicious versions of popular software images. The types of adversaries targeting these cloud services are opportunistic and almost always exploit the lack of security awareness by the owners.
One of the most prominent threat actors in this space is a group known as TeamTNT. Active since October 2019 and first disclosed in April 2020, TeamTNT specifically targets containers and cloud instances using Docker, Kubernetes, or Amazon Web Services that have been misconfigured and are publicly exposed to the internet. The group automatically scans for vulnerable instances to spread cryptocurrency mining malware and steal credentials. These threat actors are well-versed in cloud services used by application and software development and operations (DevOps) teams. They have been known to weaponise developer tools, such as WeaveScope, and use a range of custom-developed malware and open-source penetration testing tools to fulfil objectives.
Pivoting off open-source reports disclosed by a number of vendors over the last two years, Cyjax analysts have mapped the tactics, techniques, and procedures (TTPs) of the TeamTNT campaign. We are happy to announce the contribution was added to the Mitre ATT&CK framework v10 here: https://attack.mitre.org/groups/G0139/
Reconnaissance and Resource Development
Prior to attacks, TeamTNT will acquire domains (T1583.001) to host their payloads (T1608.001) and scan IP Blocks for misconfigured container API ports (T1595.001, T1595.002). The group has also used or developed a number of custom tools such as Black-T or Hildegard and used open-source offensive security tools (OSTs) such as the Diamorphine rootkit, MimiPenguin, Mimipy, LaZagne, Break-out-the-Box (BotB), TinyShell (tsh), Peter’s Parallel Network Scanner (Pnscan), Masscan, Zgrab, Tmate, Libprocesshider, and Punk.py, among others (T1587.001). To obfuscate its payloads and evade defences, TeamTNT uses software packers such as the Ultimate Packer for eXecutables (UPX) and a Golang crypter called Ezuri.
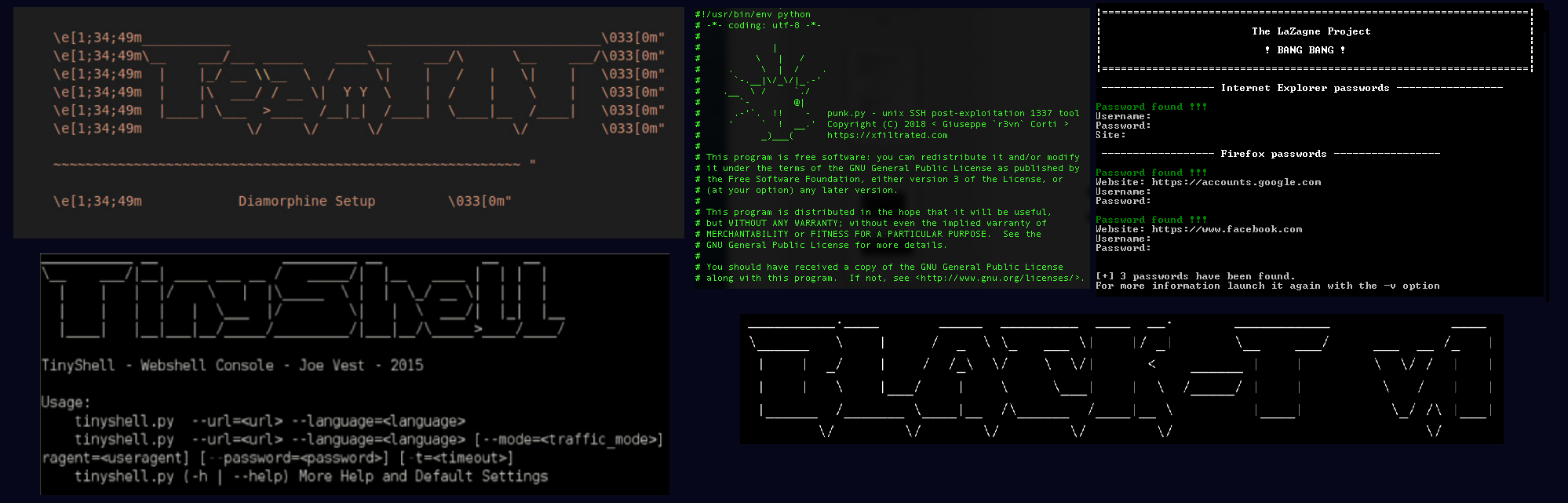
Fig. 1 – Command-line tools used by TeamTNT
Targeting Docker
Docker is a popular platform service used by developers to create, test and run their applications in a contained environment. Docker users often leave the Docker Daemon port open (Port 2375), creating a major security issue: unsecured Docker Daemons give malicious actors full access to all the containers and images. It is worth noting, however, that the Daemon alone does not directly provide access to the host operating system (OS).
Frequently used Mitre ATT&CK techniques against Docker containers
- T1595 – Active Scanning, T1612 – Build Image on Host: Scan for open Docker Daemon REST API’s on TCP port 2375 using masscan, then spin up docker images and install itself [1]
- T1204.003 – User Execution: Malicious Image: Malicious images are first pushed to a public registry. The images are then pulled and deployed on the unsecured Docker hosts. [2]
- T1613 – Container and Resource Discovery: TeamTNT has checked for running containers with “docker ps” and for specific container names with “docker inspect”. [3]
- T1496 – Resource Hijacking: TeamTNT has deployed XMRig Docker images to mine cryptocurrency. [4]
Targeting Kubernetes
Kubernetes is an open-source system that automates the deployment, scaling, and management of applications run in containers; it is often hosted in a cloud environment. Using this type of virtualised infrastructure can provide flexibility and security benefits when compared to traditional, monolithic software platforms. Compromising an entire cluster is much more severe than compromising an individual container, as a cluster could run multiple cloud applications whereas an individual container usually runs a single cloud application. While most malicious code we observed runs in pods as containers, some is directly deployed on the host.
If malware bypasses the isolation and accesses the underlying host’s resources, it also poses a risk to the cloud environment that hosts the cluster. With this level of access, threat actors can perform further lateral or vertical movements, including extracting credentials, compromising registries, and accessing the host’s data and network. Unsecured Kubernetes API servers (kube-apiserver) are similar to Docker Daemons; threat actors target misconfigured APIs to control the entire container platform. The kube-apiserver is the front end for the Kubernetes cluster that takes RESTful requests from clients and translates the requests to operations on containers, pods or nodes.
In January 2021, it was first disclosed publicly that TeamTNT was using a malware dubbed Hildegard to target misconfigured Kubelet containers and the underlying Kubernetes clusters. Hildegard has two methods of establishing a connection to its command and control (C&C) servers: a tmate reverse shell and an IRC channel. Hildegard also encrypts the malicious payload inside a binary to make automated static analysis more difficult. [5]
Frequently used Mitre ATT&CK techniques against Kubernetes:
- T1133 – External Remote Services: TeamTNT targets exposed kubelets for Kubernetes environments. [6]
- T1595.004 – Valid Accounts: Cloud Accounts, T1595 – Active Scanning: Malware, such as Hildegard, scans for and targets misconfigured Kubernetes clusters that allow anonymous access. This was achieved by accessing the kubelet’s run command API and executing commands on running containers. The attacker compromised the first container via an internet-facing and unsecured Kubelet. [7]
- T1071 – Application Layer Protocol: Malware, such as Hildegard, connects to a remote C&C using a Tmate reverse shell and the IRC protocol for each compromised container in a Kubernetes cluster [8]
Targeting Amazon Web Services
Amazon Web Services (AWS) employs multiple safeguards to protect user data and stop it from being exposed in Simple Storage Service (S3) buckets, so the responsibility mostly lies with the database owner to protect user information and ensure buckets are secured and private. AWS instances are highly targeted and regularly leveraged by threat actors for follow-up attacks.
In August 2020, the first cryptocurrency-mining worm that could steal AWS credentials from infected servers was disclosed and linked to TeamTNT. If the group infects a Docker or Kubernetes system running on top of AWS infrastructure, it can scan the underlying infrastructure for any Amazon Web Services (AWS) credentials via tools such as Mimipy or MimiPenguin. The credentials can then be used to install cryptocurrency mining malware in more powerful AWS EC2 clusters directly or potentially sell them to others on underground marketplaces. [9]
Frequently used Mitre ATT&CK techniques against AWS
- T1552.001 – Unsecured Credentials: Credentials In Files: TeamTNT has searched for unsecured AWS credentials and Docker API credentials. [10]
- T1552.005 – Unsecured Credentials: Cloud Instance Metadata API: TeamTNT has queried the AWS instance metadata service for credentials. [11]
- T1048.003 – Exfiltration Over Alternative Protocol: Exfiltration Over Unencrypted/Obfuscated Non-C2 Protocol: A worm linked to TeamTNT steals AWS credentials and config files from the default location and uses cURL to exfiltrate AWS credentials to a C&C server (sayhi[.]bplace[.]net), which responds with the message “THX” [12]
Outlook
The most active threat actors targeting cloud technologies at this time are illegal cryptocurrency mining operations. Cryptomining has proved to be an increasingly profitable way for cybercriminals to exploit victims. Cryptocurrency has boomed since its introduction to the public in 2009-10, both because of the accessibility of miners and the anonymity of the currency. The main dangers of cryptominers hijacking resources are the consumption of device CPU power which degrades performance and affects availability; overheating and data loss; the opportunity for other adversaries to exploit the backdoor that is opened when a cryptominer is deployed.
In late October, it was revealed that various ransomware operators had adopted many of the scripts and tools developed by TeamTNT. Researchers from VX-Underground disclosed that, since copies of TeamTNT’s malware had been made publicly available, both Conti and BlackMatter have expressed their interest in using it to target cloud services. The most attractive aspect of these tools to ransomware operators could be their cloud credential-stealing potential. If ransomware operators were able to lock a victim out of their cloud infrastructure, they could potentially delete backups and prevent recovery. Further research is required to see how ransomware groups could leverage these capabilities. [13]
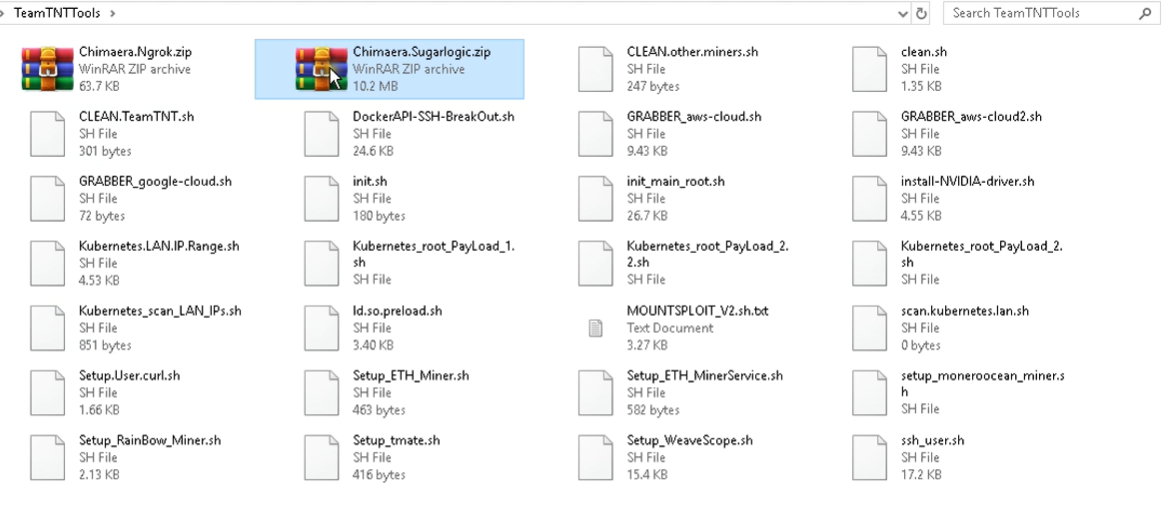
Fig. 2 – Scripts and tools developed by TeamTNT being distributed among threat actors
Organisations should also remain conscious of supply-chain attacks originating from repositories and marketplaces where software and operating system (OS) images are provided. Legitimate accounts are often impersonated or compromised to push Trojanised versions of widely used software. As recently as October 2021, researchers uncovered an account on DockerHub hosting 25 repositories containing malware developed by TeamTNT. If a user downloaded one of the Trojanised Docker images, they would receive the Zgrab scanner and Masscan. Of the 25 images on the malicious DockerHub account, one called “basicxmr” had been downloaded 100,000 times, another called “Dockerapi” had 5,400 downloads. [14]
Defenders should also evaluate and mitigate the risks presented by supply-chain attacks, such as the Codecov continuous integration tool incident. Although these scenarios are uncommon, they can continue undetected for many months and lead to catastrophic security failures, such as the SolarWinds SUNBURST campaign. [15, 16]
Acknowledgements
This blog and the Mitre ATT&CK framework contribution benefitted enormously from the reports shared by researchers from Unit42 Palo Alto Networks, Lacework, Intezer, Cado Security, Trend Micro, AT&T, Uptycs, and AquaSec, as well as the MalwareHunterTeam on Twitter.
