The whole point of ransomware is to make money for malicious actors who manage to identify security weakness in your organisation. Like any “service” it is going to come at a cost; and a ransomware incident is likely to be both very embarrassing and, when combined with data extortion, potentially very expensive.
It is time to change our cyber security perspectives of ransomware. Simply put, ransomware is a consequence of the failure to have necessary security controls and processes in place. It is also the failure to implement the best security practices or compliance with an IT security audit standard. Since the first crypto locker attacks in 2015, this “consequence of security failure” has been nothing new. Delivered as an attachment, a weblink or exploitation of an externally exposed vulnerability, the outcome remains the same: downtime embarrassment and a mad scramble to return the organisation back to regular business operations.
In fact, the claims of various cyber security vendors to “protect your organisation from ransomware attacks” are perhaps one of the most hyperbolic we have encountered. The advertising breathlessly talks about “cost” and “supply chain” and “sophisticated actors”, when the root cause of a ransomware incident is far more likely to be a weak password, an account without the benefit of MFA protections or unpatched, neglected infrastructure. In the advertising landscape, the promotion of protections has leveraged fear, uncertainty and doubt. This has constructed ransomware as some mythological creature able to miraculously appear at any time within your network, much like some malevolent poltergeist trying to do as much damage as possible.
It is for these reasons that the ISO 27001 security audit standard, and its introduction of threat intelligence requirements in 2023, is becoming increasingly popular. These standards are not only effective mitigations against the consequence of a ransomware event, but are designed to protect the organisation against any type of cyber attack by any type of actor. This is an important distinction and aligns with a risk-based approach to protecting the crown jewels of your organisation, be they intellectual property and/or personal data. Focusing your security controls on one consequence of a breach neglects what could be a devastating theft of data. The “all hazards” approach of an audit standard is designed to provide assurance to organisations against attacks on confidentiality of data, integrity of processes and availability of systems.
The addition of cyber threat intelligence (CTI) to the ISO 27001 standard is a significant development, becoming in part an admission that “more value” is required from existing cyber security controls in the audit. That is to say, it will allow organisations to deal more effectively with modern day threats and the evolving complexity of hybrid environments.
The inclusion of CTI as a control which, when properly implemented, is based on threat models and a robust collection plan provides an “over the horizon” capability for organisations. This allows them to become more resilient, better prepared, and potentially bypass an impactful cyber attack.
The CTI control within ISO 27001 seeks to build and incorporate an “intelligence led” approach to mitigating risk, by supporting security operations within the organisation. This could be useful intelligence on the tactics, tools and procedures of a threat actor or the exploitation of a known vulnerability. Moreover, it could also be a strategic intelligence report on trends in threat actor activity against industry verticals and what this may mean for an organisation. These products generated by cyber threat intelligence can inform decision makers and marshal resources to thwart an attack.
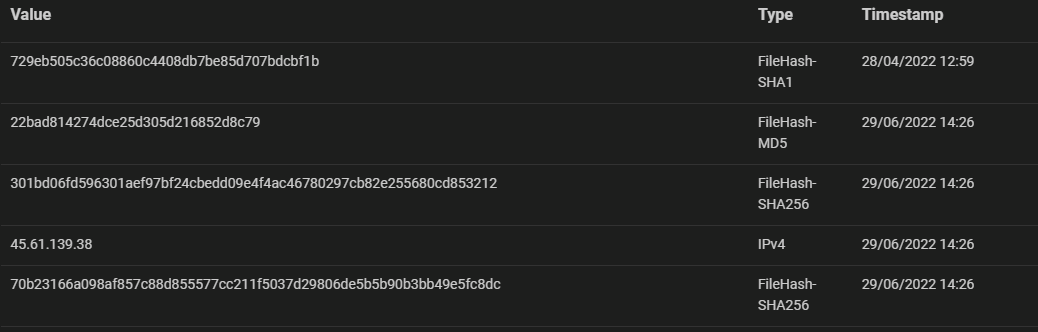
Cyjax Tactical Intelligence example:
[UPDATE – 29.06.2022] LockBit ransomware sideloading Cobalt Strike Beacon via legitimate VMware utility
Posted on 29/06/2022 14:26 | Source date: 28/04/2022
Key takeaways
Originally published on 28.04.2022
- @LockBit has been observed delivering Cobalt Strike via the VMware command line utility “VMwareXferlogs.exe”, indicating VMX logs is susceptible to DLL side-loading.
- Researchers detected a malicious version of a legitimate DLL (glib-2.0.dll) deploying a payload, which can facilitate attempts to bypass EDR/EPP and operate anti-debugging functionality.
- LockBit is a RaaS which dates back to 2019. Operators commonly leverage a double extortion technique and utilise tools such as StealBit, WinSCP, and cloud-based backup solutions for data exfiltration prior to ransomware deployment.
- Like most ransomware groups, @LockBit’s post-exploitation tool of choice is Cobalt Strike.
IOCs for this threat have been attached.
Analyst comment:
@LockBit operators persist as a sophisticated threat in the cyber landscape. This recent example highlights their ability to develop innovative responses to EDR/EPP solutions. The FBI recently released a joint Private Industry Notification advising that threat actors such as @LockBit and its affiliates are actively targeting the food and agriculture sectors. This report followed Australia’s ACSC and the UK’s NCSC observations of ransomware targeting various key industries and sectors.
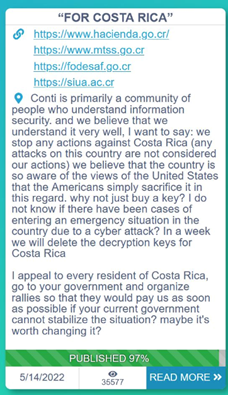
Cyjax Strategic Intelligence example
[UPDATE – 05.06.2022] Conti ransomware group targeting Costa Rica and Peru
Posted on 05/06/2022 11:34 | Source date: 08/05/2022
Originally published on 09.05.2022
Key takeaways
- Costa Rica has declared a national emergency following multiple government bodies being attacked by the @Conti ransomware operators.
- The group announced attacks on these agencies in April 2022 and has published 97% of a 672GB dump containing data from the organisations.
- Targeted government organisations include:
- The Costa Rican Finance Ministry, Ministerio de Hacienda
- The Ministry of Labor and Social Security, MTSS
- The Social Development and Family Allowances Fund, FODESAF
- The Interuniversity Headquarters of Alajuela, SIUA
- Analysis of a small subset of the data shows source code and SQL databases from government websites have been leaked.
Other organisations attacked by the group include:
Administrative Board of the Electrical Service of the province of Cartago (Jasec)
The Ministry of Science, Innovation, Technology, and Telecommunications
National Meteorological Institute (IMN)
Radiographic Costarricense (Racsa)
Costa Rican Social Security Fund (CCSS)
Analyst comment: @Conti first emerged in mid-2020 as a human-operated ransomware that quickly grew into a highly successful operation, with the US State Department describing it as the “costliest strain of ransomware ever documented”. It is believed Conti was developed by the same group responsible for the Ryuk ransomware, @WizardSpider, based on code reuse, and the fact that Conti, like Ryuk, was also distributed by Trickbot. In recent months, however, the ransomware is being delivered by BazarBackdoor as a replacement for Trickbot.
On 6 May, the US State Department announced a reward of up to $10 million for any information leading to the indictment of key individuals in the @Conti threat group. $5 million is also being offered for intelligence that can help arrest or convict individuals who are conspiring or attempting to affiliate with the group in a ransomware attack. The group is said to have attacked more than 1,000 organisations since January 2022, with their ransom pay-outs surpassing $150 million.
But simply incorporating a cyber threat intelligence program into an organisation may not be enough to satisfy the requirements of an ISO 27001 audit certification. Evidence of the CTI program effectively defending and mitigating risks with intelligence, which is relevant, timely and actionable, must be presented to the auditor. This is where the business needs to become intelligence led by incorporating workflows, be they service tickets or incident logs, into the DNA of the organisation. An effective CTI program can significantly help mitigate the risk of succumbing to the consequences of a ransomware incident, pointing out current and future inadequacies of an organisation’s cyber defences.
