Ongoing collective hacking operations such as OpIsrael, OpIran and OpIndia consist of several hacktivist threat actors working independently to disrupt critical infrastructure and government entities.
OpIsrael is an annual coordinated cyberattack, during which pro-Palestine hacktivists attack Israeli government, commercial and private websites. The campaign was launched in November 2012 by the Anonymous collective. OpIran and OpIndia are also long-running operations which originally began more than a decade ago and resurface periodically, usually as a form of anti-government online protest reflecting geopolitical developments in the countries.
Threat actors involved in the latest campaigns include TYGTeam, 1915Team, Killnet, AnonymousSudan, GhostSec, MinionsCyberCrime, TeamInsanePK, and many more.
MrSami, TYGTeam and 1915Team
TYGTeam is believed to be from Yemen and members have consistently targeted entities related to the ongoing war in that country that began in 2014. 1915Team appears to be closely affiliated with YGTeam, and consists of Kurdish, Arabic and Yemeni hackers. The two groups have been identified targeting the same victims in campaigns including OpIran and OpIsrael. They recently announced the development of an RCE Shell exploit as a cooperative tool to be utilised by them.
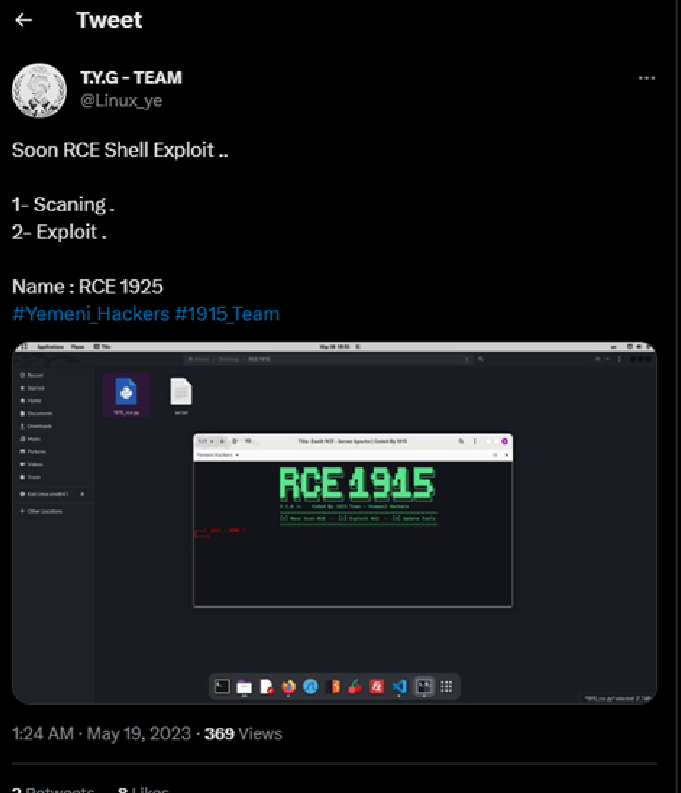
Fig 1 – TYGTeam Twitter post. (source)
Many of the attacks posted on the groups’ social media channels are attributed to MrSami, with compromised sites, data leaks and free shells published under their name. Several sites successfully attacked by the threat actors are defaced with the “MrSami” name as well as a small, often politically motivated statement.
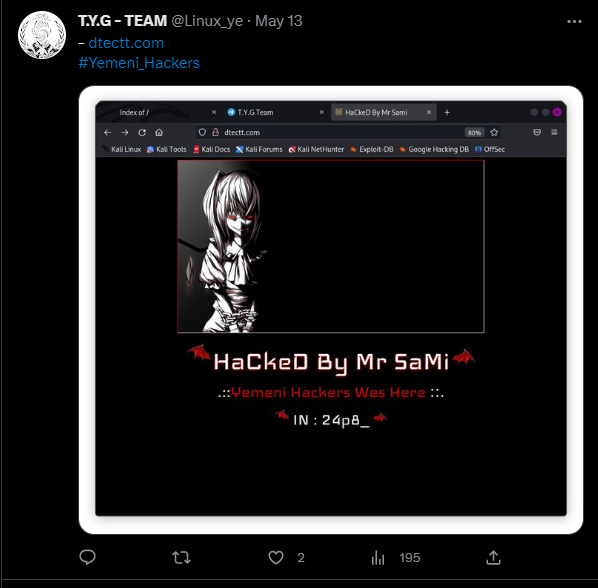
Fig 2 – TYGTeam Twitter post. (source)
AnonymousSudan, Killnet and Russia
AnonymousSudan, supposedly based in Sudan, is an official member of the pro-Russia collective Killnet and has been observed conducting attacks on their behalf. The group is known to carry out DDoS attacks, with previous victims including NATO, Israel’s CNI, German airports and the country’s foreign intelligence service, Swedish and Australian healthcare organisations, education institutes, and more.
AnonymousSudan has also shown active involvement in OpIsrael, and conducted a mass cyberattack against critical Israeli infrastructure entities on 26 April 2023. Over 40 organisations were labelled as victims, including Mossad, the webpage of the Prime Minister, the official government website, the Israeli Police, and the Israel Broadcasting Corporation. (source)
While AnonymousSudan is known to be pro-Muslim, their involvement with Killnet has aroused suspicions that they are a Russian front. In response, the group has stated the following:
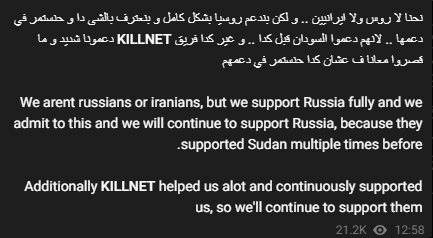
Fig 3 – AnonymousSudan Telegram channel.
Killnet recently announced that they no longer function as a collective and have stopped hacktivism activities. Instead, the group is now advertised as a private military hacking company that continues to carry out attacks for Russia and to defend Russian interests. However, as a supporting group, AnonymousSudan has most recently targeted India and the UAE, launching DDoS attacks, compromising websites, leaking data, and publishing information on its social media channels.
The UAE has been targeted by threat actors involved in OpIsrael due to the political relationship between the two countries. Additionally, UAE’s funding of Rapid Support Forces in Sudan has led to further attacks. Under the OpUAE campaign, AnonymousSudan has targeted organisations such as First Abu Dhabi Bank and UAE Pass.
Attacks related to the Russia-Ukraine war
The ongoing Russia-Ukraine war has involved a wave of cyberattacks targeting not only the two countries, but also other nations.
India decided to support sanctions against Russia in March 2023, which led to the pro-Russian Phoenix collective attacking Indian organisations. The group claimed to have gained access to the Indian Ministry of Health.
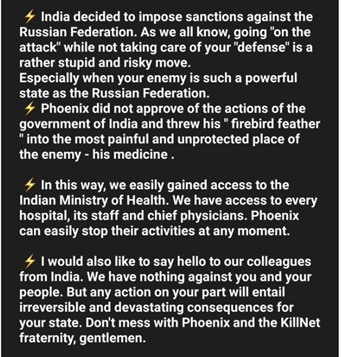
Fig 4 – Phoenix Telegram channel.
Previously, before India was perceived to be operating against Russian interests, AnonymousRussia started attacking websites in countries thought to be supporting Ukraine, as well as India.
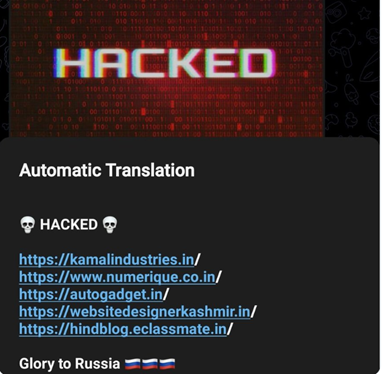
Fig 5 – AnonymousRussia Telegram channel.
To avoid retaliation from Russia, Israel refused to allow Ukraine to buy NSOGroup’s Pegasus spyware in 2022. As a result, Ukraine-affiliated GhostClan attacked Israeli government websites in a widescale attack.
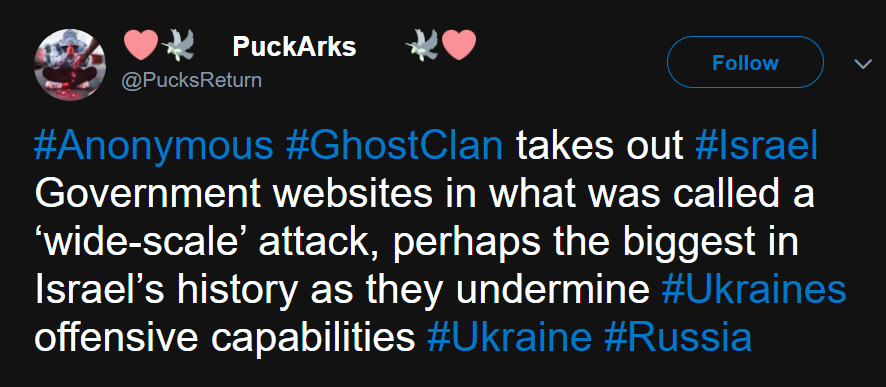
Fig 6 – Twitter post (source)
Conclusion
Large-scale hacktivist campaigns are heavily influenced by geopolitics, with developments in the Russia-Ukraine war, as well as in India and Israel, resulting in attacks against a wide variety of involved parties.
While these threat groups have differing targets, goals and ideologies, many tend to join collective campaigns to disrupt government operations, gain popularity, and further their own particular interests. Aside from groups affiliated with countries directly involved in conflicts, threat actors originating from Yemen, Pakistan, Russia and more have joined the attackers in a range of supporting cyber operations.
