
Introduction
“The printed page is obsolete, information isn’t bound up anymore. It’s an entity. The only reality is virtual. If you’re not jacked in, you’re not alive.” – Buffy the Vampire Slayer (1997), Season 1 Episode 8 – I Robot, You Jane
Five centuries after the printing press was invented, the digital age began. With significant revolutions in knowledge dissemination, the era taking place now has seen vast amounts of information become instantly accessible. Whilst this is generally seen as a positive in most countries worldwide, malicious intentions persist across the digital world.
The process of creating books prior to the creation of the printing press was meticulous and incredibly long, requiring skilled individuals to create them by hand. As such, books were at one time relatively rare and expensive. The printing press revolutionised knowledge dissemination and led to the wide adoption and new standard of creating books and readable content.
Similarly, when cryptoviral extortion first became popular, ransomware operation development was similarly painstaking. It required individuals with high technical skills to create sophisticated ransomware strains. Consequently, significant attack capabilities and even full stack development for a DLS were needed. Forming a team or commissioning individuals for each stage of the operation would be extremely difficult and require a large amount of expertise. The wide adoption of cybercriminal forums within the threat landscape has resulted in a high level of knowledge dissemination. It has allowed new threat actors to develop and maintain ransomware operations, such as under a Ransomware-as-a-Service (RaaS) model, in a fast and cost-effective way. This has been accompanied by a wide availability of services, tools, and malware, including cracked ransomware builders, malware strains, and commissionable threat actors.
This blog series aims to explore how the development of the threat landscape, particularly in the area of cybercriminal forums and messaging services such as Telegram, has resulted in the simplification of cybercrime. It will analyse how cybercriminals are able to conduct attacks without the necessary skills previously required. This first part explores the simplification of the ransomware crime ecosystem via cybercriminal forums.
The revolution of cybercriminal forums
Much like how the printing press revolutionised information dissemination, the emergence of cybercriminal forums formed centralised hubs for malicious activity. These forums have aided in the sharing of information, skills, and tools to promote the threat landscape, cooperation between threat actors, and use the concept of community for attackers to develop with each other.
Cybercriminal forums offer a centralised criminal intelligence source, with many offering features including:
- Information dissemination including discussion regarding specific attack techniques or coding capabilities.
- The sale of services and malicious capabilities such as conducting Distributed Denial-of-Service (DDoS) attacks, doxxing individuals, cyberespionage, attacks against specific organisations, and more.
- Affiliate recruitment for Ransomware-as-a-Service operations.
- Malware and tool advertisement whether cracked, leaked, professional, or self-developed.
- Individual expertise including initial access brokers (IABs), tool development, front or backend development, and similar commissionable activities.
Forum users are known to share cracked and leaked malware, ransomware builders, DDoS tools, and more on cybercriminal forums. Not only does this allow attackers to expand their own arsenal, but it also allows the new generation of threat actors to gain instant access to developed and trusted tools and malware. This occurs to such a high degree that in some cases, threat actors may not need technical development capabilities to begin conducting sophisticated attacks.
Cybercriminals also offer services such as malware development and coding expertise, allowing them to commission custom tooling and even a data-leak site (DLS). Whilst secretive circles of cybercriminals exist, the community promoted by forums provides more value to attacks. Many cybercriminals want to gain relevance and expand their activity, achieving this by advertising their operations. Alongside this, specialised threat actors can flourish within the threat landscape and cooperate with other attackers. The most prevalent example of this is the ransomware ecosystem, which is split into developers, operators, affiliates, and initial access brokers.
Ransomware as a pathway into crime
Ransomware operators have been known to successfully gain multi-million-dollar ransoms in attacks, creating a highly lucrative market for operators, affiliates, and even IABs. As a result, marketplaces are common on cybercriminal forums and threat actors can buy and sell ransomware-related products and services such as builders, malware strains, source code, initial accesses, and more.
Free malware and ransomware builders
As a new threat actor entering the threat landscape, it can be difficult to find a RaaS operation which allows forum users with no reputation or otherwise unknown individuals to become an affiliate. However, it is possible to find leaked and cracked ransomware builders on cybercriminal forums for free.
For example, a user on a ransomware-based cybercriminal forum is known to publicly advertise free download links to both malware and ransomware builders. This includes builders and source code, with advertisement threads describing the capabilities and features of each strain. The below screenshot portrays a sample of free ransomware and remote access Trojan (RAT) strains which have been freely shared by this user.
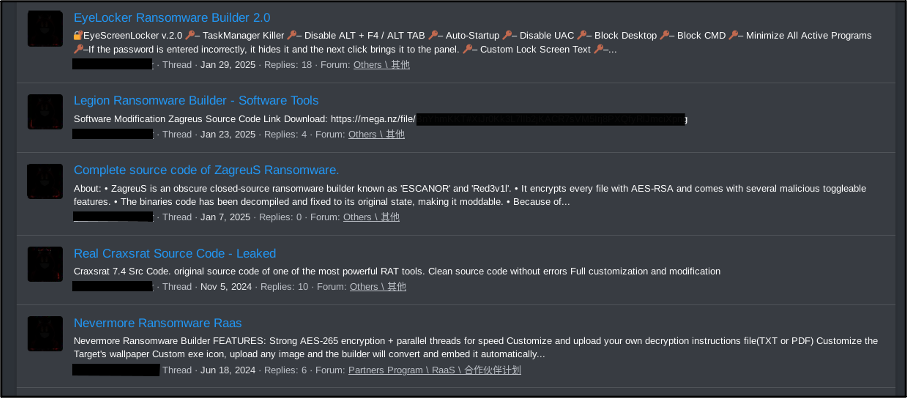
Figure 1 –List of free malware and ransomware builders on a cybercriminal forum.
As a result, an inexperienced threat actor can download a ransomware builder for free and experiment to develop their attack capabilities. Additionally, an attacker can study source code to gain technical knowledge regarding ransomware development. Making small modifications and using unseen versions of older malware strains can aid in evading detection and increase the chance of a successful attack.
Well-known examples of cracked or leaked ransomware builders have spread widely across cybercriminal forums. These have been known to be used in professional ransomware operations. For example, the Bl00Dy ransomware group first began operating in May 2022 and used a Telegram channel to advertise its leaked data. Despite this, the ransomware operator did not appear to have developed its own tools. Instead, it used open-source and leaked builders from other operators, including LockBit, Babuk and Conti. From September 2022, the group used the LockBit ransomware builder in its attacks, which was leaked in late 2022.
Similarly, the DragonForce ransomware binary was also revealed to have been likely generated using the LockBit Black builder. The DragonForce RaaS operation was responsible for extortion attacks against the UK retail sector in early- to mid-2025, with an affiliate assessed to be ScatteredSpider having breached Marks & Spencer, Co-op, and Harrods.
Using code from multiple operations could benefit threat groups. Switching between code from different strains of ransomware can aid in detection evasion, whilst also allowing the group to vary the features used in attacks.
Case Study: The RedLotus ransomware development
As previously mentioned, ransomware operations traditionally consisted of small, highly capable teams responsible for all stages of the attack chain. This included gaining access, escalating privileges, deploying malware, encrypting files, exfiltrating data, and negotiating a ransom. Additionally, this would also often include the development of tools and malware used in the attack. With the advent of cybercriminal forums, these responsibilities have been separated to allow threat actors with specific expertise to contribute towards attacks without requiring the knowledge of the entire chain. For example, IABs can sell access to organisations for ransomware operations, removing the need for the brokers to conduct extortion attacks. This also removes the need for ransomware threat actors to conduct reconnaissance and gain initial access. Moreover, ransomware developers can sell source code to other threat actors to avoid conducting attacks themselves. Cyjax identified a specific example of in early 2025 across multiple cybercriminal forums.
A cybercriminal forum user Cyjax tracks as ‘RedLotus’ has been observed developing a ransomware operation from at least early April to June 2025. RedLotus appears to have technical skills in malware development, having claimed to self-develop a ransomware binary. RedLotus has stated that their aim is create an entire ransomware operation, including a data-leak site (DLS) and admin panel. The user’s final goal is to purportedly sell the entire operation to a threat actor which will conduct the extortion attacks.
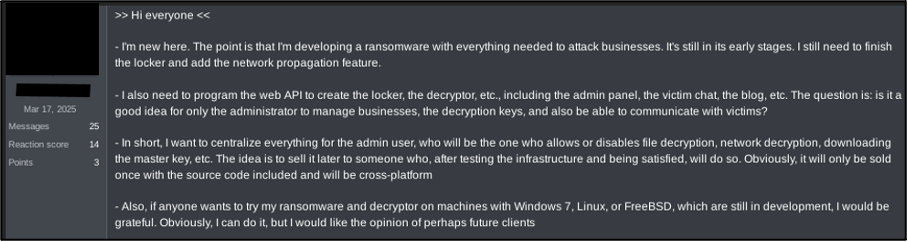
Figure 2 –Initial post in RedLotus’ ransomware development thread.
RedLotus has similarly commissioned other areas of the operation to a variety of forum users. One forum user was commissioned to develop an admin panel but created an arbitration post against the ransomware developer. This user provided screenshots of a Telegram conversation between the two and claimed that they had been scammed. From the screenshots available, it appears that the admin panel was aimed to be used for command and control (C2) communication.
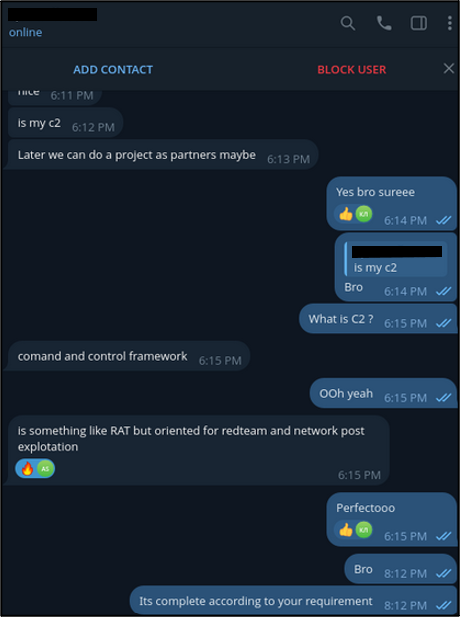
Figure 3 –Screenshot of Telegram conversation between a forum user and RedLotus.
Similarly, RedLotus has rented a bulletproof virtual private server (VPS) to likely facilitate C2 communication. This portrays that although the user has stated they are developing the entire ransomware operation, RedLotus is also relying on the skills of other threat actors and services to create it fully.
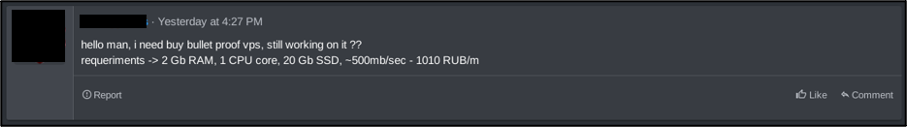
Figure 4 – Forum post by RedLotus requesting bulletproof VPS.
Not only does this phenomenon portray the dissemination of information across cybercriminal forums, but it also indicates the level of involvement some individuals can have to form a threat. It also demonstrates how specialisations are apparent on these forums. In early June 2025, RedLotus posted a request for an artist on the forum to create a logo. This is entirely legal activity which is being requested on a cybercriminal area. A non-criminal may be able to gain funds on forums without committing crimes or directly contributing to malicious activity. However, there may be an expectation of due diligence. Specifically, if the artist visit’s the user’s profile, then they will see that RedLotus is developing a ransomware operation. As such, the logo may be used for branding in the ransomware operation.
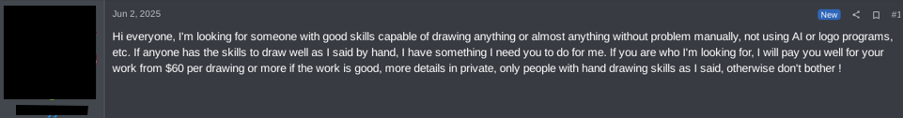
Figure 5 – RedLotus’ request for an artist on a cybercriminal forum.
Ransomware-as-a-Service (RaaS)
As opposed to the closed ransomware group model which previously dominated the scene, many ransomware developers have turned to the RaaS model. Within this model, ransomware developers lease it to affiliates who conduct the attacks and in return provide a share of the ransom.
The below screenshot portrays the affiliate programme offered by ransomware group Medusa. As of early June 2025, Medusa has listed over 400 victims on its DLS and offers a comprehensive affiliate service. The advert states that affiliates gain access to professional teams for support, negotiation, and discussion, as well as the ransomware builder which can target Windows, Linux, and ESXi devices. There are benefits for affiliates which reach a certain payment amount. Specifically, affiliates are paid a higher percentage of the ransom if a larger revenue organisation is attacked.
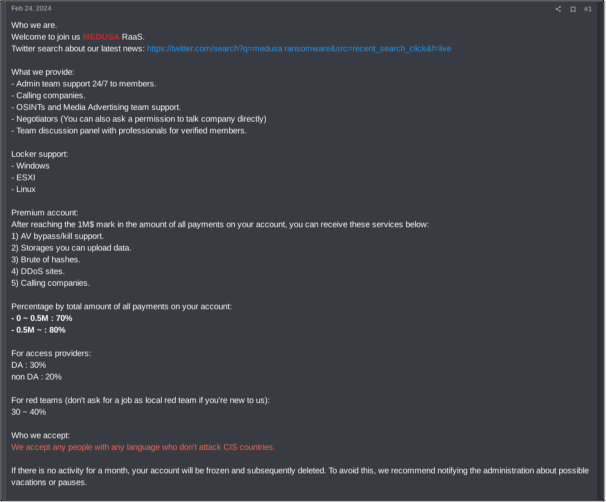
Figure 6 –Medusa’s RaaS affiliate advertisement post.
Affiliates can use access to a sophisticated builder and gain experience in attacks using ransomware. Subsequently, affiliates can acquire funds upon successfully ransoming a target. Developing their programming skills or reputation within the cybercriminal ecosystem may lead to affiliates developing their own brand. Conversely, the existence of easily obtainable binaries potentially compels existing affiliates to splinter from their current groups and provides newer threat actors entry into the ransomware ecosystem.
As explored in Cyjax’ blog “Here, There, Ransomware: The Surge of New Ransomware Groups”, ransomware is a business. Employees can find work elsewhere if a company breaks down, goes bankrupt, or no longer offers competitive terms. Alternatively, once they have enough experience, employees may choose to create their own brand and company. When a group does break down or disband, its affiliates often choose to set up their own RaaS group if they have sufficient technical ability and experience. It is here where se groups will nurture the next generation of affiliates. This creates a cycle where more groups are created as threat actors become familiar with how to conduct ransomware operations. These then result in more groups and the cycle continues.
Conclusion
The cybercriminal landscape currently allows individuals with little expertise to use forums to download free leaked ransomware builders, gain experience, and begin conducting attacks. Here, IABs may be used to purchase accesses staged for malware deployment.
An activity pipeline may be established with the following process. While this is not a defined progression method within the threat landscape, it provides a structured and feasible method cybercriminals may use in developing their activities.
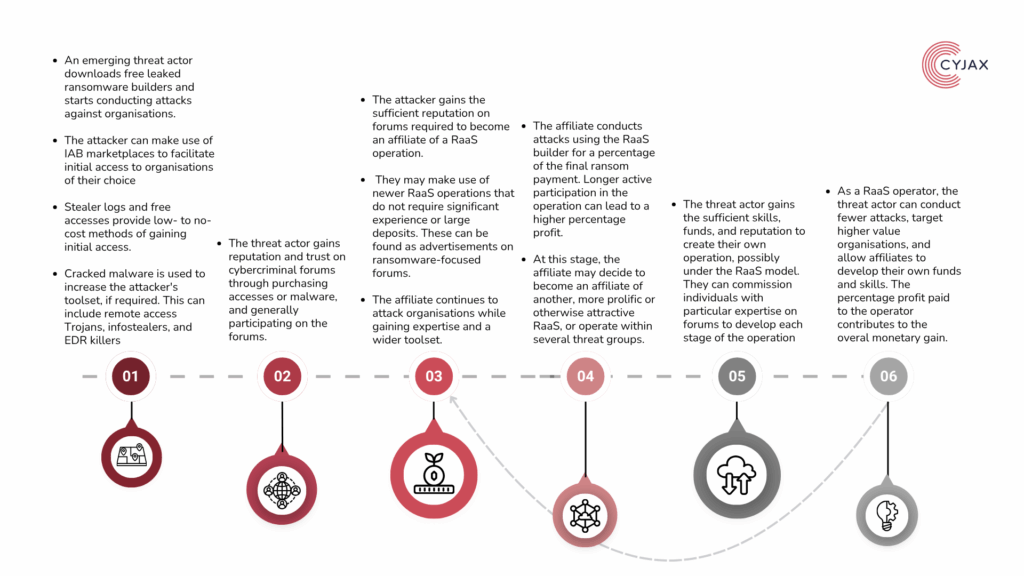
Figure 7 –Possible ransomware threat actor progression timeline.
However, this concept has been discussed on another cybercriminal forum. In late March 2025, a user initiated a thread debating the current state of hacking. Here, the user stated that the majority of new hacking groups are “a bunch of skids in costumes” or individuals with low technical capabilities masquerading as sophisticated threat actors. The initial post included the suggestion that many new threat groups use AI-generated code to produce ransomware builders for RaaS operations. This sentiment appears to be shared with other forum members, with one user replying that the state of hacking has become a “playground for script kiddies”. These individuals have been labelled as “inexperienced wannabes who slap together some half-baked code throw on a spooky mask and call themselves a “group.””.
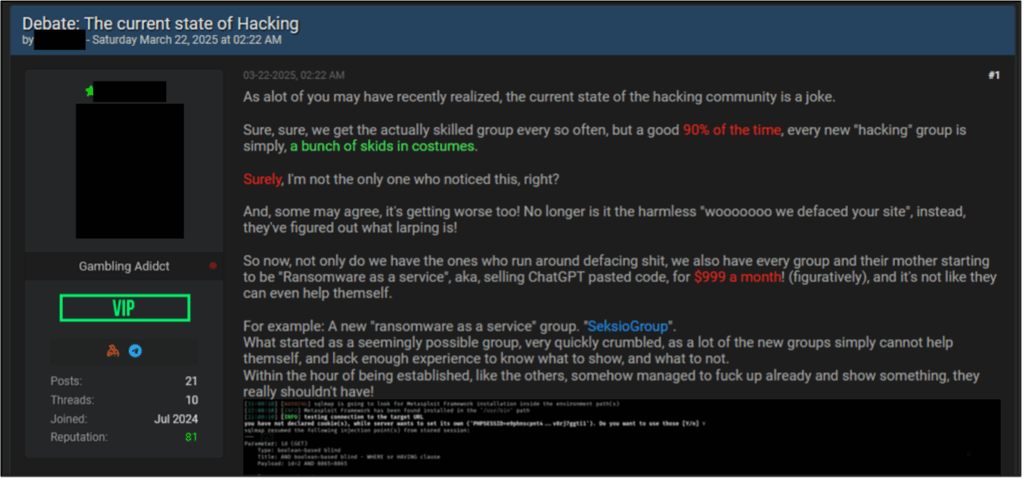
Figure 8 –Cybercriminal forum post regarding the state of hacking.
Whether this sentiment is true, notable threat groups identified in 2025 have listed prominent and impactful organisations on data-leak sites. This highlights that regardless of skill level and reputation, new groups can conduct attacks against organisations and monetise operations through ransom demands and extortion. In the short term, whilst the skill level required to conduct sophisticated attacks appears to be lowering, the number of observed successful attacks is not. This portrays that this changing landscape is benefitting emerging threat actors by providing the necessary platform to progress quickly and gain expertise. It also shows how threat actors can acquire the toolsets to instantly conduct attacks rather than relying on slower means of progression, such as learning malicious programming and developing capabilities.
It is vital to monitor changes within the global threat landscape. This includes monitoring the progression of threat actors and the lowering barrier of entry into cybercrime, which can aid in proactive threat mitigation by analysing commonly distributed malware. Additionally, monitoring threat actor discussion can aid in understanding their capabilities, motivation, and intent.
Receive our latest cyber intelligence insights delivered directly to your inbox
Simply complete the form to subscribe to our newsletter, ensuring you stay informed about the latest cyber intelligence insights and news.
