Introduction
From late 2023 and into 2024, the ransomware ecosystem has become more diverse than ever, with an ever-expanding cast of extortion groups. Established players continue to compromise large companies globally, while smaller, newer groups are breaking into the scene with increasing frequency. From January to mid-May 2024 alone, 22 new ransomware groups emerged. In comparison, only 22 groups emerged during the entire two-and-a-half-year period between January 2018 and August 2020.
This blog will explore the growth in the ransomware market and possible causes, as well as the effect of various related phenomena on ransomware groups and their victimology.
Key takeaways
- There are more ransomware groups than ever, with approximately 5.5 new groups emerging per month so far in 2024.
- Possible explanations for this sudden boom include the natural evolution and maturity of the ransomware market, the widespread availability of ransomware binaries and Ransomware-as-a-Service programs on cybercrime forums, changes to ransomware groups themselves, law enforcement activity, and geopolitical developments.
- The boom continues as ransomware is not a saturated market. There are far more potential victims than there are current ones. With the creation of more companies, the ransomware victim pool constantly increases.
- There is an inverse correlation between the relative diversification of ransomware groups and unification of hacktivist groups. Financially motivated ransomware groups tend to splinter, while politically motivated hacktivists are increasingly collaborating in larger collectives.
Statistics
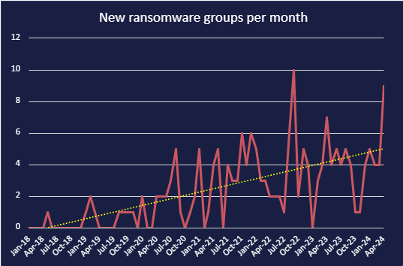
Group creation is at a yearly all time high
In May 2024, there are more ransomware groups than ever before. Approximately 5.5 new groups have emerged per month so far this year, tracked by the discovery of public-facing data-leak sites (DLSs). April alone saw at least eight new or rebranded groups, with notable inclusions being Eraleig (APT73) and Hellogookie, which itself is a rebrand of the HelloKitty ransomware originally formed in late 2020. Eraleig, which also refers to itself as APT73, is a new group created by an alleged former Lockbit affiliate, before law enforcement conducted “Operation Cronos” to disrupt the group in late February 2024.
Graph showing ransomware group emergence from January 2018 to April 2024.
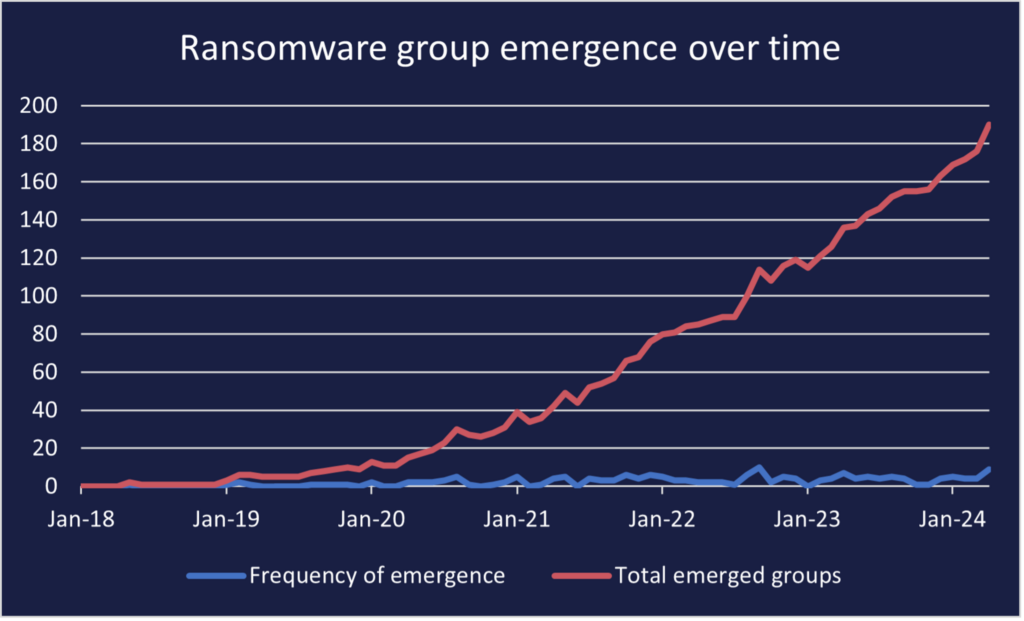
Since January 2018, the rate at which ransomware groups have emerged has drastically increased, in an almost exponential manner. The total number of publicly identified groups with trackable DLSs have reached nearly 200, as seen in the graph below. There are likely many more groups that do not maintain public facing infrastructure. Though older groups may split or disband, and as such not all ~200 groups remain active, Cyjax has identified that over 60 of the groups with DLSs have conducted attacks so far this year. Some groups have stood the test of time, such as RagnarLocker, which has been active since 2019.
More groups does not always mean more attacks
It is important to note that the creation of new ransomware groups is not directly related to the number of ransomware attacks, with there being a 22% drop in ransomware attacks in Q1 2024 compared to Q4 2023. However, a more diverse set of attackers means that organisations must be aware of a more disparate set of TTPs that they must defend against. It is also likely that over the medium term (3-12 months), there will be an increase in the number of attacks as newer groups develop and mature.
September 2022 and April 2022 Spikes
While the rate of emerging ransomware groups has shown a general upward trend since January 2018, growth has not been totally linear. There was an anomalous emergence of 10 new groups in September 2022, a rate of emergence similar to the spike in April 2024; however, there are several likely causes for this.
Former prominent player Conti ransomware disbanded in late May 2022 following internal leaks, and officially shut down operations in early June. With the main team fluctuating between 62 and 100 members, it is almost certain that many of these individual threat actors moved to other ransomware operations or similar threat activity. For example, Cobalt Strike infrastructure associated with Conti was observed in various other ransomware operations. Conti’s disbanding was followed by a significant decrease in the number of emerging ransomware groups for several months. This then spiked again for the anomalous peak seen in the graph. The delay between the closing of one larger group and the emergence of newer, smaller groups could be explained by reticence and nervousness on behalf of the threat actors around law enforcement activity. It could also be explained by the time needed to build up and acquire new resources and infrastructure necessary to conduct offensive operations.
Our report on the disbanding on Conti and analysis of the internal leaks can be found here.
Another contributing factor is likely the leak of the LockBit Black ransomware builder in September 2022. This leak allowed threat actors to generate customised ransomware binaries for their own operations. There have been at least seven named ransomware groups known to have used the leaked builder in their attacks – Darkrace, DragonForce, Bl00dy, BlackDogs 2023, NATIONAL HAZARD AGENCY, GetLucky, and Buhti. However, there are highly likely many more threat actors using the builder.
There was another significant decrease around December 2023 and another smaller one occurring between February and March, followed by the significant spike in April 2024. These may be explained by the high profile ALPHV ransomware exiting the market in December 2023, and the ecosystem’s most prolific group LockBit being partially disrupted by law enforcement in February 2024.
Graph showing ransomware group emergence from January 2018 to April 2024.
What has likely caused the general increase in new group emergence?
Natural market evolution
Like any industry sector, the ransomware market has naturally increased in maturity over time, with older ransomware groups developing new tactics, techniques, and procedures (TTPs) and refining their malware and infrastructure, alongside newer groups learning the ropes.
Researchers have noted that ransomware groups are moving to target small to medium-sized businesses (SMBs) rather than large companies, typically those with lower revenues. Since Q1 2023, the average revenue of ransomware victims fell from around $1 billion, to $450 million in Q1 2024. A possible explanation for this phenomenon affecting the ransomware ecosystem is that new ransomware groups tend to have comparatively underdeveloped TTPs and less proficient technical capabilities. As such, they may target smaller businesses that likewise tend to have weaker security postures when compared to larger, better resourced organisations. While the overall SMB targeting is a new progression in the ecosystem, prominent group LockBit has long been known to target SMBs, eschewing the traditional “big game hunting” practiced by other outfits. LockBit affiliates moving to new groups following the law enforcement operation, due to decreased trust or natural splintering, may adopt this victimology in their new teams.
Greater availability of ransomware-as-a-service and ransomware strains
Ransomware builders, binaries, and offers for ransomware-as-a-service (RaaS) programs, whereby operators lease their malware to affiliates, who attack organisations and in return provide a percentage of the ransom profits to the operators, have become increasingly available. This allows more novice threat actors with fewer technical capabilities to conduct attacks without needing to develop their own ransomware, lowering the barrier for entry into the threat ecosystem.
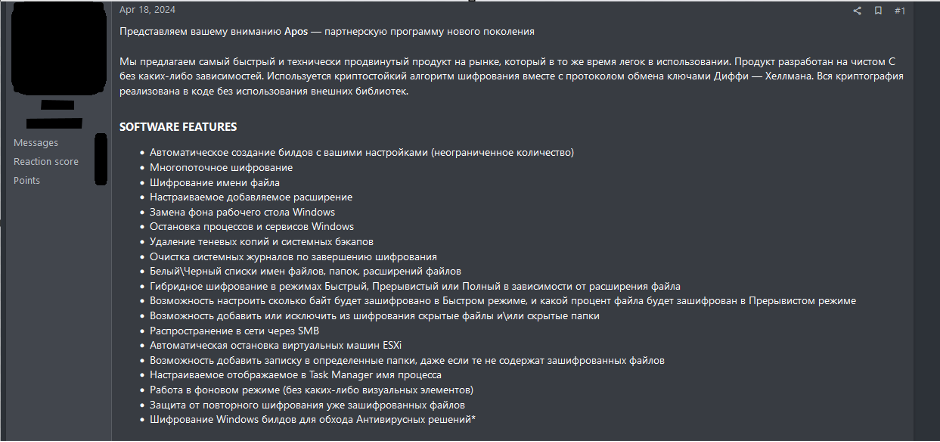
Below is a screenshot of a RaaS advertisement on RAMP regarding Apos, a ransomware group that emerged in April 2024. Translated from Russian, the advertisement reads –
Introducing Apos – a new generation affiliate program
We offer the fastest and most technically advanced product on the market, which is at the same time easy to use. The product is developed in pure C without any dependencies. A strong encryption algorithm is used along with the Diffie-Hellman key exchange protocol. All cryptography implemented in code without using external libraries.
SOFTWARE FEATURES
- Automatic creation of builds with your settings (unlimited number)
- Multi-threaded encryption
- File name encryption
- Customizable add-on extension
- Windows desktop background replacement
- Stopping Windows processes and services
- Removing shadow copies and system backups
- Clearing system logs after encryption is complete
- White\Black lists of file names, folders, file extensions
- Hybrid encryption in Fast, Intermittent or Full modes depending on file extension
- Ability to configure how many bytes will be encrypted in Fast mode, and what percentage of the file will be encrypted in Intermittent mode
- Ability to add or exclude hidden files and\or hidden folders from encryption
- Network distribution via SMB
- Automatic shutdown of ESXi virtual machines
- Ability to add a note to specific folders, even if they do not contain encrypted files
- Customizable process name displayed in Task Manager
- Work in the background (without any visual elements)
- Protection against re-encryption of already encrypted files
- Encryption of Windows builds to bypass Antivirus solutions
Apos advertisement on RAMP
In addition to RaaS programs and ransomware builder leaks, advertisements for inexpensive ransomware binaries as a one-off purchase, or even for free, have been seen on cybercriminal forums. These crudely built strains allow threat actors to conduct their own attacks without needing to pay a percentage of the profits to a RaaS operator, many of whom require large amount of capital up front to join their affiliate program. The existence of these easily obtainable binaries potentially compels existing affiliates to splinter from their current groups and provides newer threat actors with less financial means entry into the ransomware ecosystem.
Below is an example of a ransomware toolkit being disseminated on a cybercrime forum for free, further indicating the prevalence of simple initial introductions to the ransomware ecosystem, allowing new threat actors to completely bypass the ransomware creation stage and immediately conduct attacks.
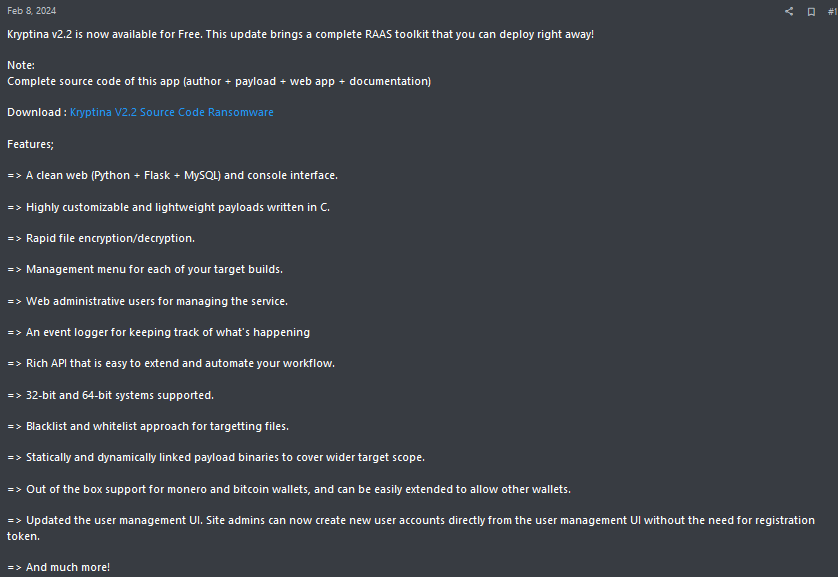
Kryptina RaaS toolkit promotion on cybercrime forum
The affiliate-to-operator development pathway
Ransomware is a business – employees can find work elsewhere if a company breaks down, goes bankrupt, or no longer offers competitive terms. Alternatively, employees, once they have enough experience, may choose to create their own brand and company. When a group does break down or disband, it affiliates, if they have sufficient technical ability and experience, often choose to set up their own RaaS group where they will in turn nurture the next generation of affiliates. This creates a cycle in which groups create more groups as more threat actors become familiar with how to conduct ransomware operations. These then result in more groups, and the cycle continues.
Law enforcement playing Wack-a-mole
Despite successful law enforcement activity, very few group members have been apprehended in recent years. Law enforcement operations also have potentially unintended effects on ransomware groups. While groups may be disrupted and taken offline in law enforcement operations, it is difficult to attribute committed crimes to specific individuals, then even more difficult to extradite and/or arrest these individuals, leading to rebranding or reemergence of threat groups. An example of this can be seen in the law enforcement operation “Operation Cronos,” in which Russia-based ransomware group LockBit was taken down by joint forces including the Federal Bureau of Investigation (FBI) and National Crime Agency (NCA). LockBit relaunched its operations shortly after and resumed publishing attack announcements, with a new encryptor “LockBit-NG-Dev” identified in several new attacks. Law enforcement subsequently released the alleged identity of LockbitSupp as Dmitry Khoroshev. Regardless, LockBit continues to release attack announcements at a high rate, and as mentioned previously, a former affiliate has created their own ransomware group, Eraleig. As long as operators and affiliates remain at large, there is little to stop them rebranding, moving to existing groups, or setting up one of their own. Even when law enforcement operations do result in apprehension, in parallel to the drug cartels operating in Central America, the industry is simply so lucrative that another threat actor will step in to fill the gap.
Ransomware groups causing changes
Group operators themselves can cause changes in the ransomware ecosystem. In the case of RaaS adoption, operators rely on affiliates to conduct attacks, while affiliates rely on the operators to facilitate negotiation and provide the ransomware binary; however, this symbiotic relationship comes with several hardships. Operators must maintain a good reputation and provide sufficient services to the affiliates, while the affiliates are required to conduct attacks and accept decisions made by the group, such as final ransom payouts. Often, disputes take place, relationships sour, and group members can turn on each other.
ALPHV, also known as BlackCat, was a high-profile RaaS group which first emerged in late 2021. In December 2023, the FBI conducted an operation targeting ALPHV infrastructure, resulting in domain seizures. Despite law enforcement action, ALPHV remained active until March 2024, when it shut down its servers and conducted an exit scam, following an affiliate, allegedly responsible for an attack against United Health Group (UHG) and its Optum division, complaining to administrators of a Russian-language cybercriminal forum that ALPHV operators had denied them their share of the $22 million ransom payment from the attack. ALPHV operators subsequently stated that they were shutting down operations, falsely claiming that the operation had been compromised by the FBI. They later advertised the ALPHV ransomware source code for $5,000,000. In response to the exit scam, the affiliate allegedly responsible for the attack, as well as several others, formed the RansomHub ransomware group, which started leaking data purportedly gained from the original UHG attack.
Geopolitical influence
It is known that many ransomware groups are based in Russia, such as Revil, LockBit, Black Basta, the now-defunct Conti, DarkSide, and Avaddon. While the Russia-Ukraine war has significantly impacted cooperation between governments, and therefore law enforcement operations and extraditions, Russia particularly has shown scant interest in acting against ransomware groups, so long as they target the West. This is not necessarily a new development, with the anti-CIS targeting rules of almost all Russian-language cybercriminal forums reflecting the community’s recognition of the Kremlins’ willingness to turn a blind eye to cybercrime so long as it impacts the West. However, since Russia’s invasion of Ukraine, the already rare Russian-Western law enforcement cooperation has become non-existent.
Why the boom can continue
Lack of market saturation: the town is big enough for all of us
A noteworthy reason the growth of the ransomware market can continue is that it is not a saturated market – there are many more possible targets than current targets, with an estimated total of 334 million businesses in the world. Every time a new company is created, it becomes a potential target. This is increasingly important considering the recent shift to groups targeting SMBs, further increasing the pool of potential victims, and likelihood of attacks for lower revenue organisations. In this sense, ransomware groups do not compete against each other to attack a limited number of victims. Rather, if one groups attacks a particular business first, the other groups will simply turn to a similarly unprotected organisation.
Mandatory attack reporting
Another factor is the increase in mandatory attack reporting. Organisations in the US are required to disclose cyber incidents within 96 hours, with potential significant consequences from the Securities and Exchange Commission (SEC) if they do not comply. Non-compliance could lead to financial penalties, legal liabilities, reputational damage, and more. Companies may not want to publicly disclose ransomware attacks if they can pay the ransom and recover the stolen and encrypted data, and the requirement for SEC filings has provided additional extortion opportunities to threat actors.
For example, ALPHV allegedly listed a complaint with the SEC regarding one of its victims following a data breach. Threat actors may choose to urge victims to pay the ransom with the additional threat of filing complaints, increasing the potential of victims paying the ransom not only to recover data and prevent public data leaks, but also to prevent consequences from regulatory bodies.
ALPHV post allegedly reporting victim to SEC (Credit: Malware News)
Cybercrime forums
Ransomware operations often use initial access, malware, tooling, and hosting infrastructure commonly available for purchase on cybercriminal forums, as well as the networking and recruitment opportunities prevalent on these locations. These forums constantly grow and become more mature as new users join and existing ones gain experience. Services provided by threat actors on forums are diverse, allowing more opportunities for ransomware operators and affiliates to facilitate their operations. This is through initial access brokers to buy access to organisations, affiliate advertisements to advance ransomware groups, discussion topics to collaborate with other operators and expand capabilities, and more. Thus, the ransomware market becomes more specialised, as operators can allocate responsibilities of the operation to other members, allowing them to concentrate their efforts in specific areas and innovate.
Testing in developing countries
Ransomware groups are known to test their code on organisations in developing countries in Africa, Asia, and South America before moving on to larger organisations and countries. This allows them to develop their ransomware to a sufficient degree before targeting organisations that are potentially more lucrative but have stronger security postures based in Western geographies all the while standing a better chance at evading detection and increasing the capabilities of the group and its ransomware.
Ransomware groups such as Medusa conducted attacks in Senegal, Chile, Colombia, Brazil, Southeast Asia, South Africa, and Argentina, before moving on to target countries such as the US, UK, Canada, Italy, and France. Developing countries may, and often do, have lower security measures and insufficient protection against attacks, creating an ideal target for ransomware groups testing their capabilities. For example, the graph below portrays the number of secure Internet servers in Brazil and the United Kingdom per million inhabitants, showing the vast difference in both Internet prevalence and related security measures.
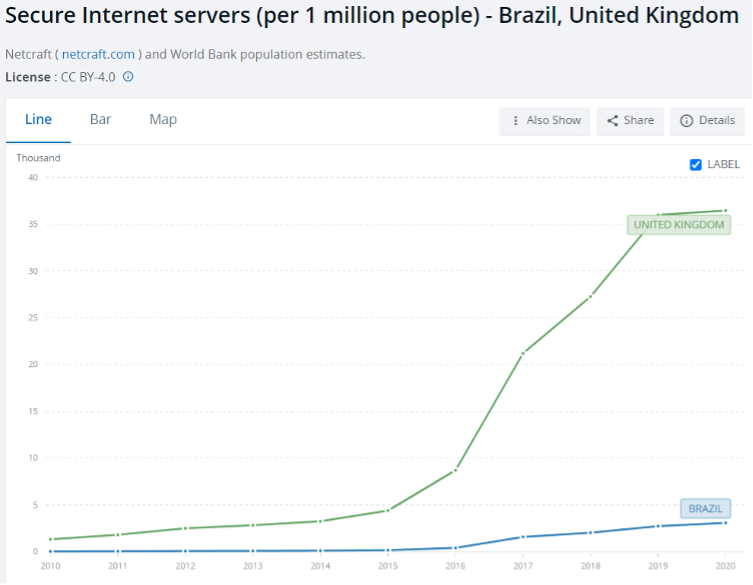
Graph showing number of secure Internet servers per million people in Brazil and the UK. (Credit: The World Bank)
Notably, a newly identified data-leak extortion site, Arcus Media, first posted on 08 May 2024 and has since posted data leaks for companies strictly in Brazil, Colombia, Argentina, Egypt, and the Philippines. The operating group itself works with an affiliate system, though there is no public evidence that it is encrypting files and directories. However, the targeting indicates that the threat actors are attacking companies in developing countries, suggesting a newly emerged group potentially testing its capabilities.
Comparison to hacktivism
A sizeable portion of this blog discusses ransomware groups splintering and affiliates leaving known groups to create their own operations. The inverse of this theme can be seen in hacktivism, where groups are increasingly forming larger collectives and uniting under singular causes. As there are no profits to be shared, collective members are not worried about having a smaller slice of the pie, and instead can focus on increasing their efficiency and strength of attacks. As ransomware actors are financially motivated, they are highly unlikely to collaborate and form multi-ransomware groups, even if this would result in a higher chance of success.
The main goal of ransomware is monetary gain. In the case of RaaS, affiliates likely aim to increase their profits, while removing the dependence on the RaaS operator, and are likely to splinter, even if this is less efficient than remaining in the affiliate role. As hacktivists are not financially motivated, efficiency is vital as it aids in achieving their goals, meaning they are less likely to splinter and decrease the efficiency and effectiveness of their attacks. Similar dynamics exist in both spheres of the threat landscape but are essentially reversed due to the primary goal of the threat actors.
On this note, our report on the factors contributing to threat actor unification can be found here.
Conclusion
With the observed developments in the rate of emergence of new ransomware groups, the prevalence of ransomware is not likely to change anytime soon. While factors affect the rate of progression in the ransomware ecosystem, whether slow or fast, it remains climbing.
Ransomware remains an extreme threat to organisational security. Defenders will need to be wary of more attackers using an increasing number of different TTPs. It is potentially easier to defend against fewer, larger, known entities with established TTPs, than many smaller ones using a range of techniques and with lower detection capabilities. Standard security policies and procedures may not be enough with the potential new and increased TTPs. Therefore, it is vital to consider pre-emptive mitigation and risk management to minimise potential damage in the increasingly likely case of ransomware targeting.
Cyjax closely tracks all existing and emerging groups to keep its customers aware of these developing threats.
Ready to strengthen your organisation’s defence against ransomware?
Request a demo today to see how Cyjax can help you stay ahead of the evolving threat landscape. Our comprehensive tracking and analysis will provide you with the insights and tools needed to pre-emptively mitigate risks and safeguard your operations.
