Introduction
Initial access brokers (IABs) form a key part of the cybercriminal ecosystem. They facilitate access for ransomware groups, data leakers, and advanced persistent threat groups (APTs) into corporate networks. They are highly specialised, professional, and operate in an established, lucrative market which is often characterised by rigid rules and conventions. Every ransomware incident or data breach begins with initial access, following the reconnaissance phase of an attack. For a fee, IABs can facilitate entry into an organisation’s network. This blog provides an overview of the landscape, identifying the key behaviours and operations of IABs.
What is an initial access broker?
Put simply, an IAB is a trader of entry points to corporate networks. IABs buy and sell remote access to the systems and infrastructure which organisations use to conduct business. For a threat actor to conduct malicious activity, it must first gain access to a network or system. An attacker can spend time and resources attempting to gain access to networks or could alternatively purchase it from an IAB. This is because IABs are specialists at getting into these networks and passing on such access to other cybercriminals.
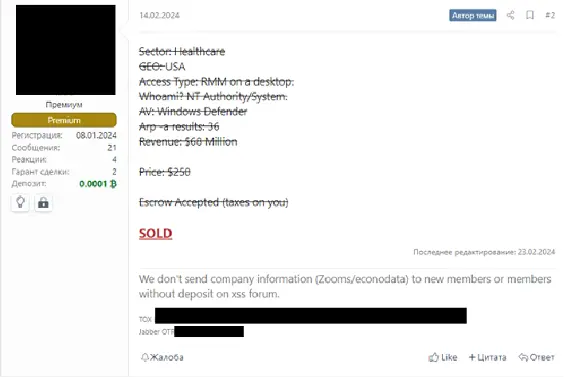
Figure 1. An initial access broker claims the sale of initial access to an unnamed US-based healthcare company
How do they achieve access?
Initial access brokers gain access to networks in a variety of ways, including the following:
- Purchase of compromised credentials: IABs may purchase or acquire compromised credentials from data leaks posted on cybercriminal forums. Additionally, credentials harvested from stealer malware can also be used in IAB operations.
- Weak exposed infrastructure: The internet may be scanned by IABs for exposed, public-facing services which are protected by default or basic passwords. These services can sometimes lack password protection, giving IABs easy access into networks.
- Exploitation of vulnerabilities: IABs can exploit flaws in unpatched and exposed hosts or services. This is commonly achieved through the use of Proof-of-Concepts (POCs) or via zero-days.
- Phishing and remote access malware: Phishing campaigns or drive-by downloads can be used to deploy malware, which provides continuous access to target networks. IABs can then sell this continuous access to other threat actors.
Alternatively, some IABs specialise in privilege escalation. Here, access with low privileges is purchased from another IAB. The access is then exploited to increase privilege levels and can be sold on for a higher price. This is due to the increased value of a more privileged access.
However, access is gained, the goal of an IAB is to directly monetise it without conducting additional attacks. Compared with extortion and ransomware groups, IABs do not hold victims to ransom or steal and sell data. Instead, an IAB is focused on facilitating access for other threat actors.
Where do initial access brokers operate?
Initial access can be sold in a various ways and much like legitimate products, can be offered either directly to consumers or through a marketplace. Some threat actors have members or known affiliates who gain initial access for a fee. These are often trusted individuals, with many deals occurring via direct message and in closed groups.
Others may pivot to the open market, with IAB listings found in the Access and Auctions sections of many Tor-hosted cybercriminal forums. Some forums have been operating successfully for decades, with the two most prominent being Russian-language forums Exploit and XSS. These forums are characterised by longevity, strict rules, and competent administration and moderation teams. Exploit and XSS have been running since 2005 and 2013, respectively. English-language counterparts do exist, though the scene is less stable as law enforcement takedowns and jailed forum administrators are a comparatively frequent occurrence. In 2024, the IAB market has amalgamated around a handful of mostly Russian-language forums. Several of these are closed access, meaning visitors must pay or otherwise prove their competency to register. Threat actors are also known to sell initial access on instant messaging service Telegram through prominent group chats; however, this is less common.
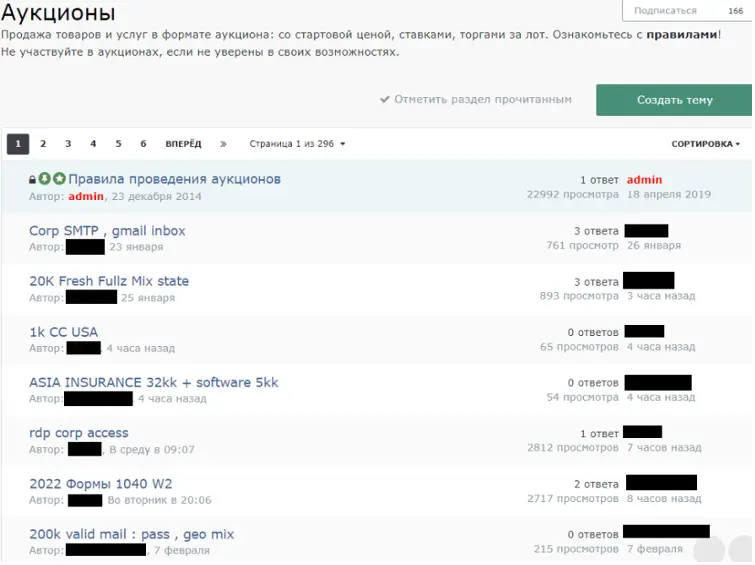
Figure 2. The landing page of the Auctions section of a Russian-language cybercriminal forum
How do they operate?
Initial access listings on cybercriminal forums follow some common conventions, ensuring sales are completed without issue.
Brokers are keen to prevent victims from discovering the compromise before access is sold. If an organisation is able to identify that it has been compromised, it may be able to remove the threat actor’s access before it can be sold.
One method to achieve this is to obscure the identity of the advertised organisation, often by refraining to name it. Instead, IABs provide a vague description which often only lists the victim’s geography, industry sector, revenue, and the type and privilege level of the access. Listings may also include the number of employees at the organisation. It may also present technical information such as the number of hosts, the anti-virus present on the network, or the type and amount of data available via the access. On many Russian forums, criminal slang and other writing conventions are used to further obfuscate this information from users who are uninformed.
Some IABs sell access individually whilst others are sold in bundles. In certain cases, trusted IABs may not advertise named accesses at all and rely on pinned posts to note that they sell initial access. In this instance, interested buyers must contact the IAB via private message to discover what the vendor has available.
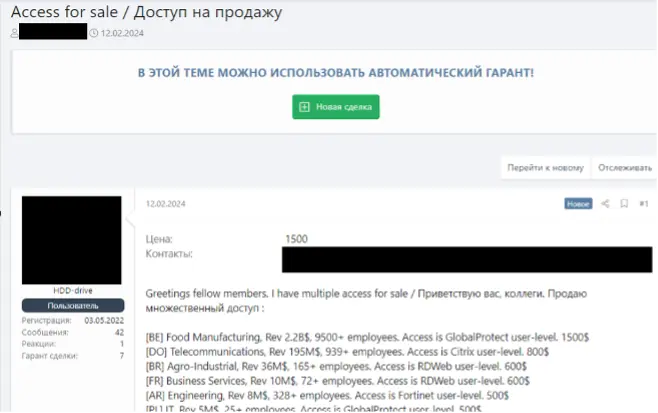
Figure 3. An initial access broker uses one post to advertise multiple initial access listings
Why do IABs use cybercriminal forums?
Like most cybercriminals, IABs face the common challenge of anonymising their identity whilst communicating with other threat actors and appealing to markets. Effective and successful Tor-hosted cybercriminal forums often solve these issues. The options for encrypted messaging and in-built systems such as escrow and “people’s courts” allow IABs to negotiate trade privately and anonymously. This also means that IABs can appeal to forum administrators should another threat actor carry out fraud attempts.
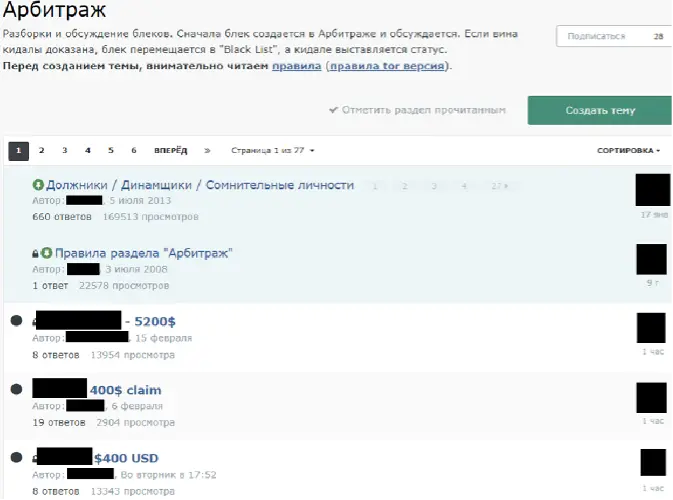
Figure 4. The Arbitration section on a cybercriminal forum sees users appealing to the forum administration section to settle their claims against other users
Most forums have a reputation system where points are awarded to legitimate traders upon the completion of successful sales. Many forums also feature a deposit system, where users can place large sums of cryptocurrency on a profile. This indicates a level of credibility and success to other forum members without IABs revealing their offline identity. However, these systems are not infallible and exit scamming remains an issue.
IABs also use cybercriminal forums because it solves many marketing issues, with these sites presenting a ready-made target market. Forums attract a range of cybercriminals, including ransomware affiliates, identity fraudsters, carders, malware developers, money launders, and more. Many of these threat actors are interested in purchasing initial access to corporate networks for various reasons. Therefore, IABs do not need to create and maintain a platform to advertise access. Instead, an IAB can simply use one which already exists.
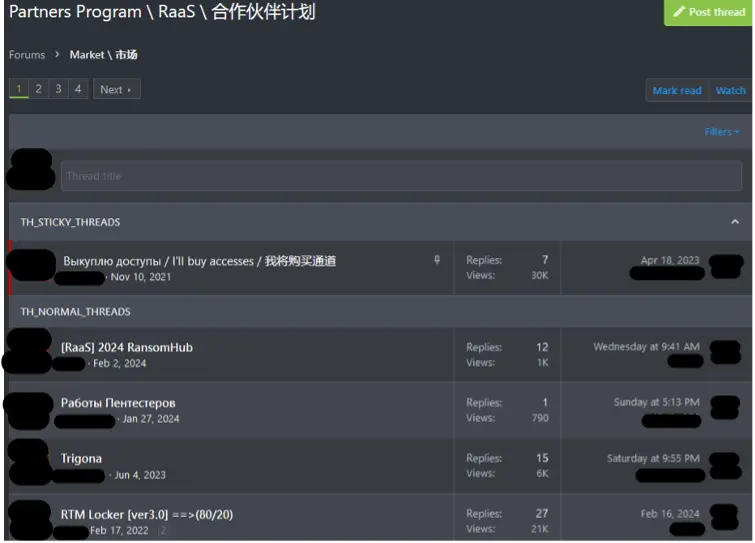
Figure 5. Ransomware operators advertising their ransomware-as-a-service (RaaS) partnership programs advertised on a cybercriminal forum
Why do initial access brokers exist?
If IABs can gain access to networks, it follows that technically competent ransomware operators and affiliates should be able to carry out the same activity. In many ransomware attacks or data breaches, initial access is gained through publicly exposed entry points. However, though many extortion and data-leak groups gain initial access themselves, IABs allow for specialisation.
IABs enable threat actors to focus on a relative area of expertise, including lateral movement, privilege escalation, encryption, and exfiltration. Cybercrime is a huge business, and like any business, it has specialists. A ransomware group may choose to focus on encrypting victim’s data rather than conducting reconnaissance and gaining access to networks. As such, the market allows IABs to become extremely effective at gaining access without having to consider the nuance of extorting a victim. Put simply, they can gain access, sell it on, and cash out.
Once a threat actor has gained initial access to a network, it is likely that it does not know which organisation has been breached. This is especially true if the compromised device is running on a VPN, cloud, virtual machine, or other proxy. In this case, an attacker must often explore the network by conducting discovery and examining files in an attempt to decipher the victim’s identity. In certain incidents, once an attacker discovers the nature and identity of a gained access, it may choose to discard it. An example of this is where a ransomware group compromises an organisation with a very small revenue, which means it is likely not worth extorting. Additionally, the breached organisation may be based in a country or sector which the attacker did not wish to target. These instances of discarded access present both a period of wasted time and potential monetary loss for an attacker. Instead, threat actors can use the services of an IAB to outsource victim identification through details including the target environment, country, sector, and revenue.
Similarly, whilst a ransomware group might not have the time and resources to search for exposed hosts or conduct phishing campaigns to gain initial access, an IAB may not have the capability to conduct an attack. Furthermore, it is likely that IABs believe they cannot be held accountable for attacks if they only sell gained accesses. The concern of being discovered installing a ransomware executable, stealing data, extorting organisations, and collecting and laundering a ransom demand is removed. However, selling access allows an IAB to target this specialised market and make a financial gain.
Conclusion
IABs remain a prevalent part of the wider cybercrime landscape, facilitating access to many organisations worldwide. Because of this, it is vital that organisations understand the threat posed by IABs and how the outsourcing of initial access aids threat actors in conducting attacks.
Cyjax leverages its linguistic capabilities and years of experience to track initial access listings across the most prominent and hidden cybercriminal forums. Click here to find out more about the threat landscape and how Cyjax can help your organisation.
Receive our latest cyber intelligence insights delivered directly to your inbox
Simply complete the form to subscribe to our newsletter, ensuring you stay informed about the latest cyber intelligence insights and news.
