
CYJAX Integrations
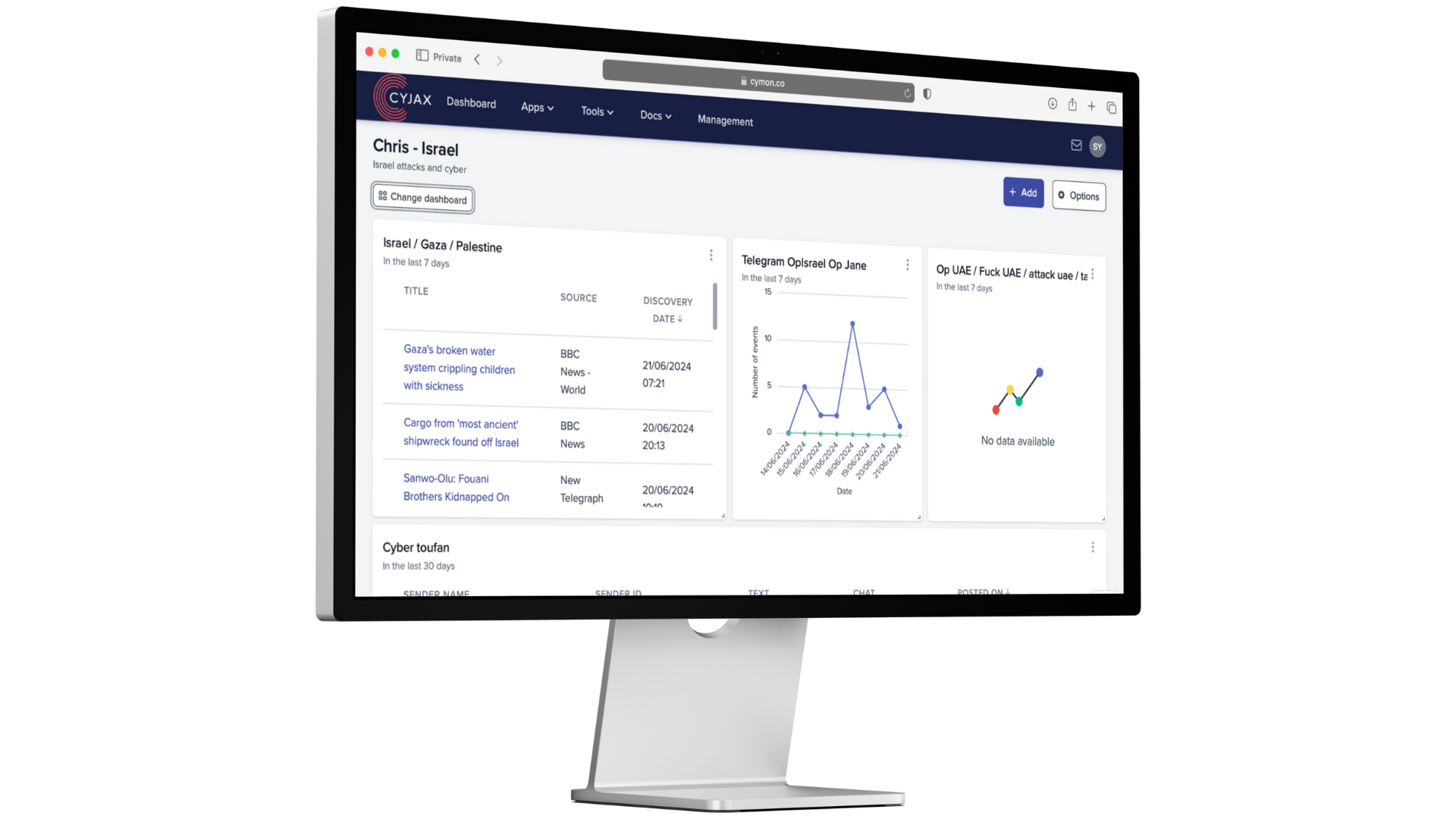
Security Workflow Automation
In the event of a security incident, effective communication and collaboration are critical. Workflow automation enables seamless incident escalation and collaboration among different teams, such as IT, security operations and management. Automated workflows can notify the relevant personnel, escalate incidents based on severity, and facilitate real-time collaboration to swiftly contain and mitigate potential threats.
Featured Integrations





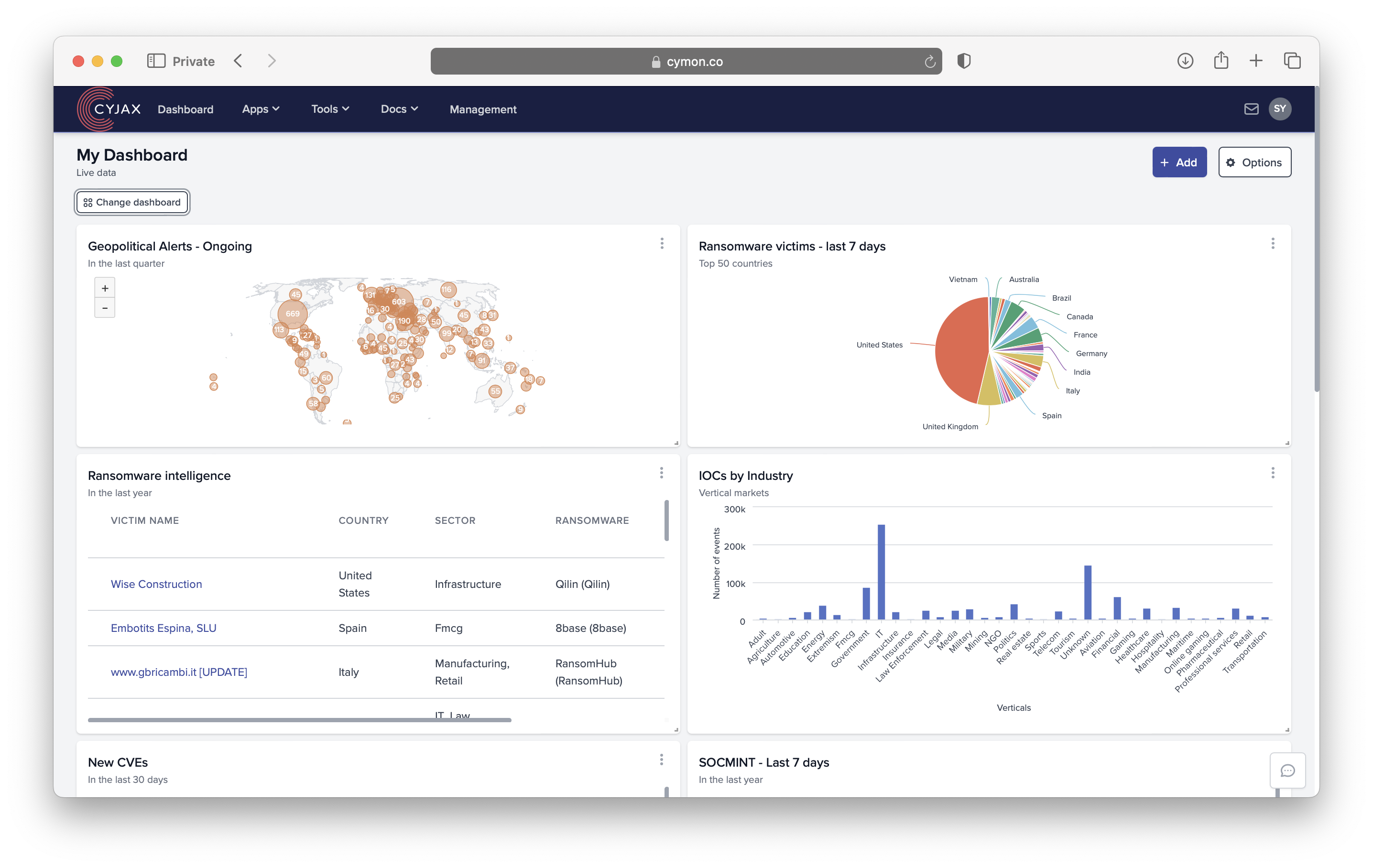
Mitigate Risks
In the face of increasingly sophisticated cyber threats, rapid detection and response are crucial. CYJAX workflow automation integrates our threat intelligence with your existing security automation platform and enables real-time monitoring of external cyber threats. Automated workflows can trigger immediate notifications, alerts and responses when suspicious activities are detected, allowing your security team to investigate and mitigate threats promptly.
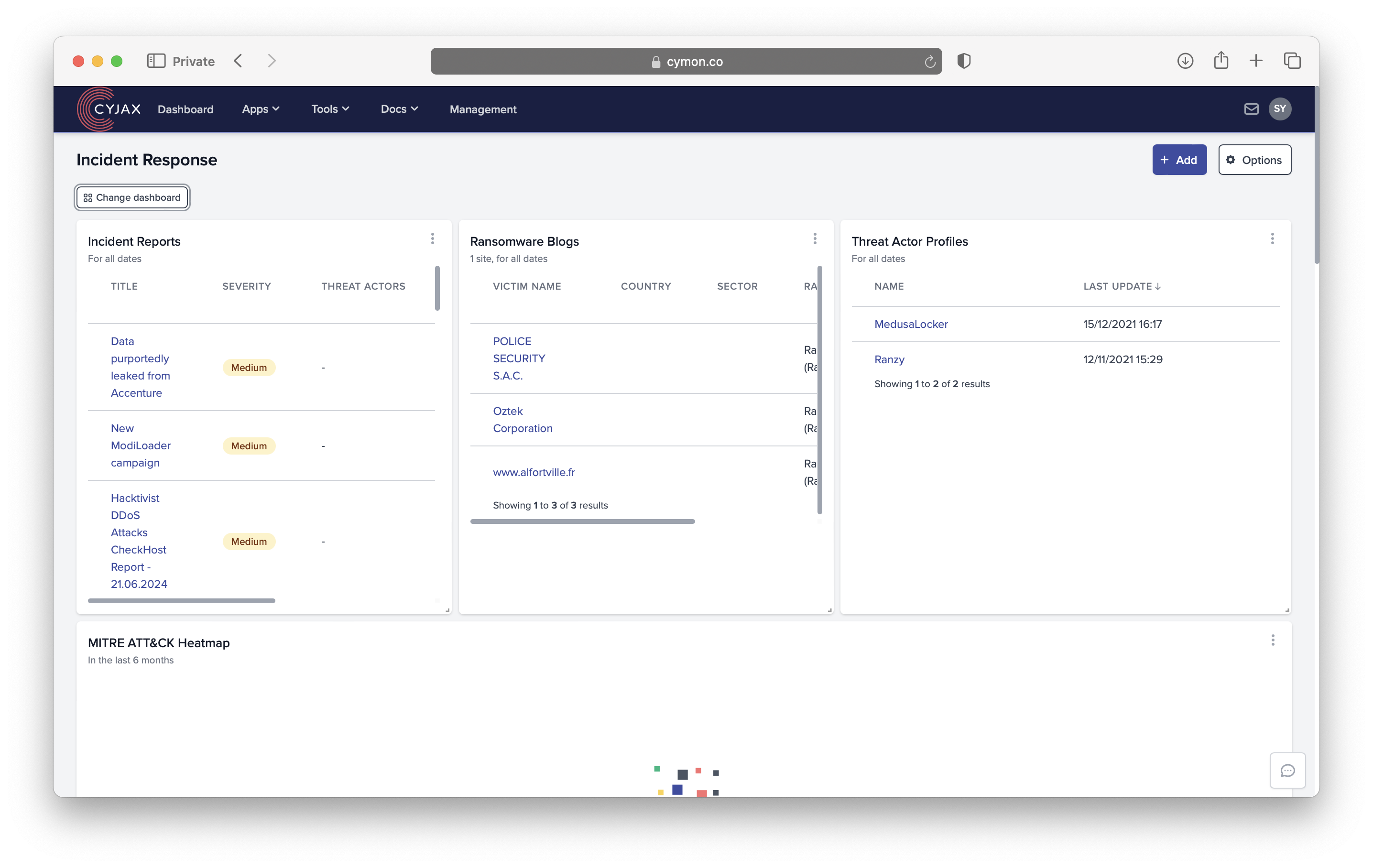
Cybersecurity and Intelligence Workflows
Cybersecurity and intelligence workflows often involve numerous manual processes and tasks that are prone to human error. With workflow automation, these processes can be streamlined, accelerating response times and ensuring accuracy. By automating routine tasks such as data breach monitoring, darkweb exposure and threat detection, your team can focus on higher-value activities, such as analysing threats and developing proactive security strategies.
Awards and Certifications




Protect your company’s most valuable asset with CYJAX
CYJAX integrates with market-leading solutions such as Palo Alto – Cortex XSOAR, IBM – Qradar, Splunk, ServiceNow, Vectra, Threat Quotient, TAXII2, MISP, and OpenCTI. Our platform also comes loaded with a Python SDK that enables bespoke solutions and support for OT infrastructure.
Receive our latest cyber intelligence insights delivered directly to your inbox
Simply complete the form to subscribe to our newsletter, ensuring you stay informed about the latest cyber intelligence insights and news.

