Following the emergence of data-leak sites (DLSs) for extortion group Morpheus earlier this year, Cyjax has discovered a DLS for a new extortion outfit going by the name GD LockerSec. Read on to find out what we know so far.
Key takeaways
- A Tor-hosted DLS emerged for GD LockerSec in January 2025.
- At the time of writing, the group has claimed attacks against four organisations which are basedin Hong Kong, Nigeria, Morocco, and the US.
- GD LockerSec has released download links for data allegedly stolen from two of these organisations.
- Posts on a prominent cybercriminal forum suggest that GD LockerSec may be claiming at least one leak that had already been conducted by a separate threat actor, though this is unclear.
- It can be inferred that it plans to leak data for the other two named victims in late January and early February 2025.
- Wording on GD LockerSec’s DLS implies that the group operates as a Ransomware-as a-Service operation, though no evidence has materialised to confirm this.
Context
Extortion groups commonly use DLSs to further extort victims, typically proceeding in multiple stages. The first threat is that the victim’s name and news of a successful attack against it will be published on the extortion group’s website. Should this fail to motivate a victim to pay a ransom, the group’s next step is typically to provide proof of the successful theft of its data, such as screenshots of internal file trees, samples of employee or customer PII, or other sensitive documents. The group may add a countdown at this stage, noting that should the victim fail to pay by the conclusion, it will make available to DLS visitors all stolen data, either for free or at cost.
Locations
Data-leak site
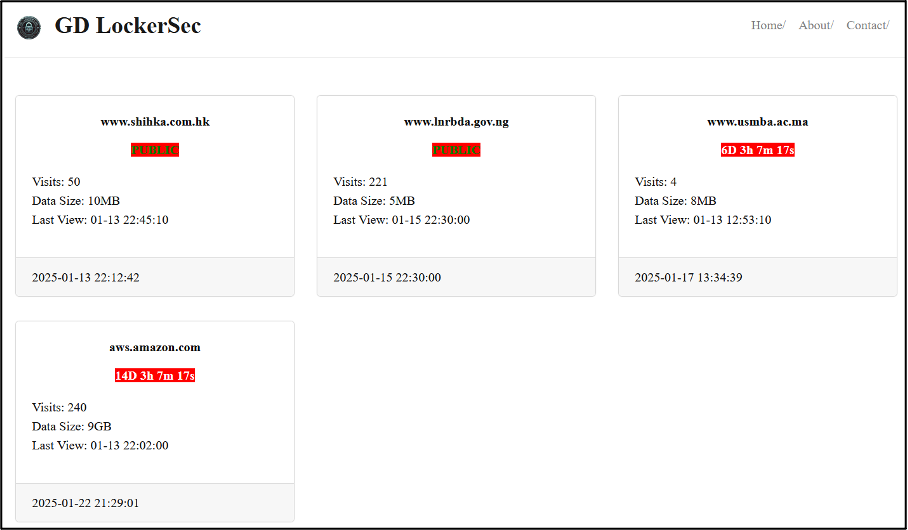
The Tor-hosted GD LockerSec DLS consists of three main pages. The first, which is the site’s landing page, hosts a list of organisations the group claims to have targeted. These provide the organisation’s name, the amount of data the group claims to have stolen from it, the number of views each victim post has received, and indicate whether the allegedly stolen information is publicly available for download from the site. Victim posts also feature a “last view” date, though this does not appear to have been updated. Underneath each of the four victim posts which exist at the time of writing, a date is listed. Though no further information surrounding this date is provided, it is likely that this relates to the date on which the group added each post to the site. Clicking on each victim post takes the visitor to a page from which they can download the allegedly stolen data.
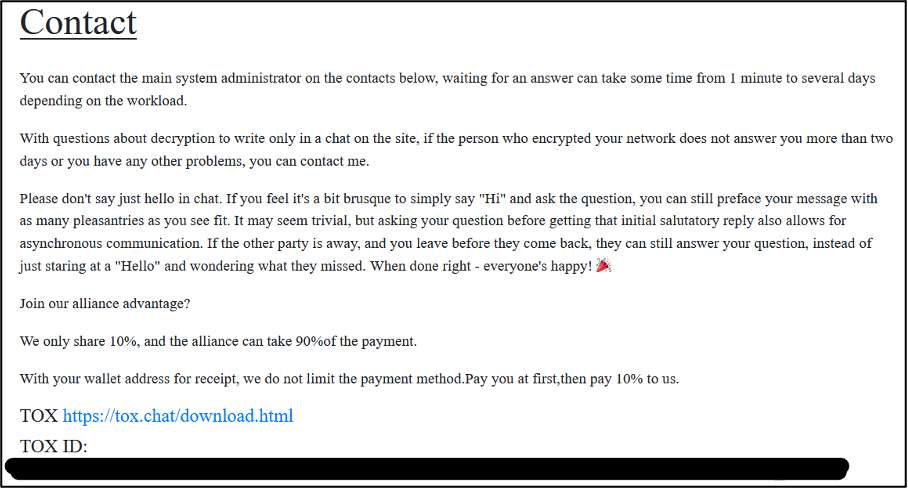
Other pages on site, namely ’About’, and ’Contact’, feature the group’s manifesto, rules, and affiliate program details. They also include the group’s contact details for the encrypted messaging platform Tox.
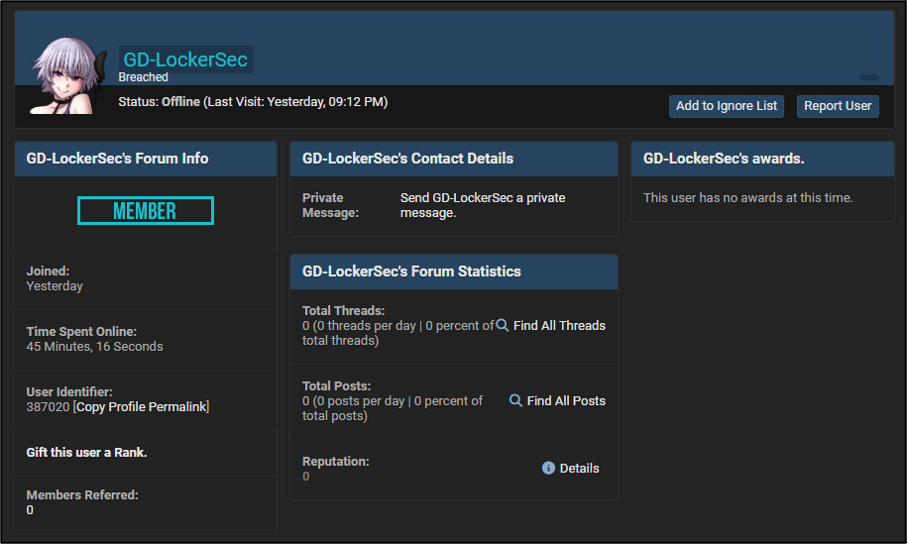
Possible BreachForums account
On 23 January 2025, an account with the username ’GD-LockerSec’ was created on the prominent English-language cybercriminal forum BreachForums. At the time of writing, this account has not made any contributions to the forum. Additionally,Cyjax cannot verify whether it is operated by the same entity that operates the GD LockerSec DLS.
Victimology
As of 24 January 2025, GD LockerSec has claimed attacks against four victims. Each of these victims are based in different geographies:
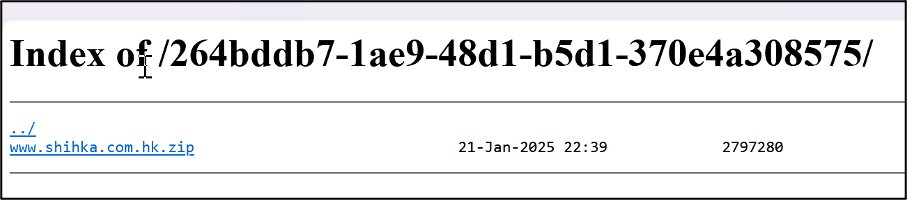
- Hong Kong-based packaging products manufacturer Shih Ka Plastic Boxes (www.shihka.com.hk), which was named on 13 January 2025. From this listing, 10MB of data allegedly stolen from the organisation is available for visitors of the site to download.
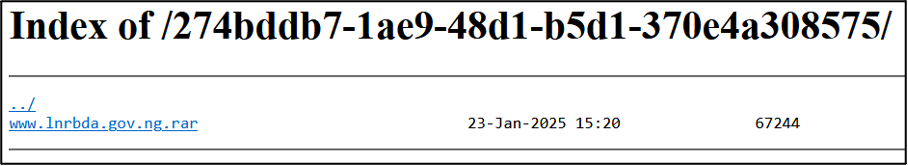
- Nigeria-based River Basin Development Authority (www.lnrbda.gov.ng) (LNRBDA), which was named on 15 January 2025. From this listing, 5MB of data allegedly stolen from the organisation is available for visitors of the site to download.
- Morocco’s Sidi Mohamed Ben Abdellah University (www.usmba.ac.ma), which was named on 17 January 2025. From this listing, 8MB of data allegedly stolen from the organisation is available for visitors of the site to download. GD LockerSec has not released a download link for the 8MB of data it claims to have stolen from the organisation. However, visitors can load and display a CSV of the data that contains the following column headings: “n_lab, n_equipe, nom_equipe, axe_rech__equipe”.

- Amazon Web Services (aws.amazon.com) (AWS), which was named on 22 January 2025. GD LockerSec has not released a download link for the 9GB of data it claims to have stolen from the organisation. However, visitors can load and display a CSV of the data that contains the following column headings: “week, sales_method, customer_id, nb_sold, revenue, years_as_customer, nb_site_visits, state”.
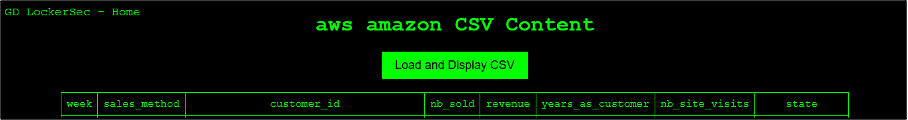
It is unclear whether the group is claiming an attack against Amazon Web Services directly, or against one or multiple companies that use the service. The Sidi Mohamed Ben Abdellah University and AWS victim posts features a timer which is due to expire on Thursday 30 January 2025 and Friday 7 February 2025, respectively. It is likely that this relates to the date upon which GD LockerSec intends to release a download link for the full or partial data it claims to have stolen from these organisations.
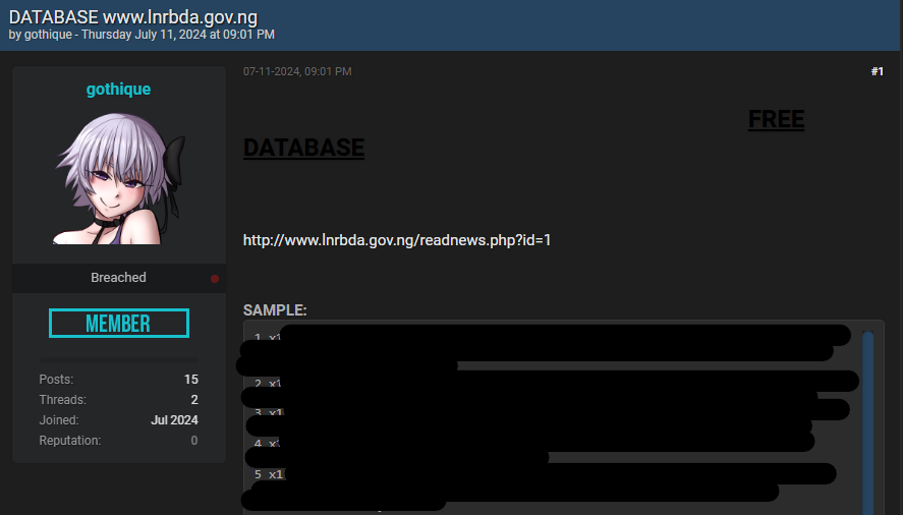
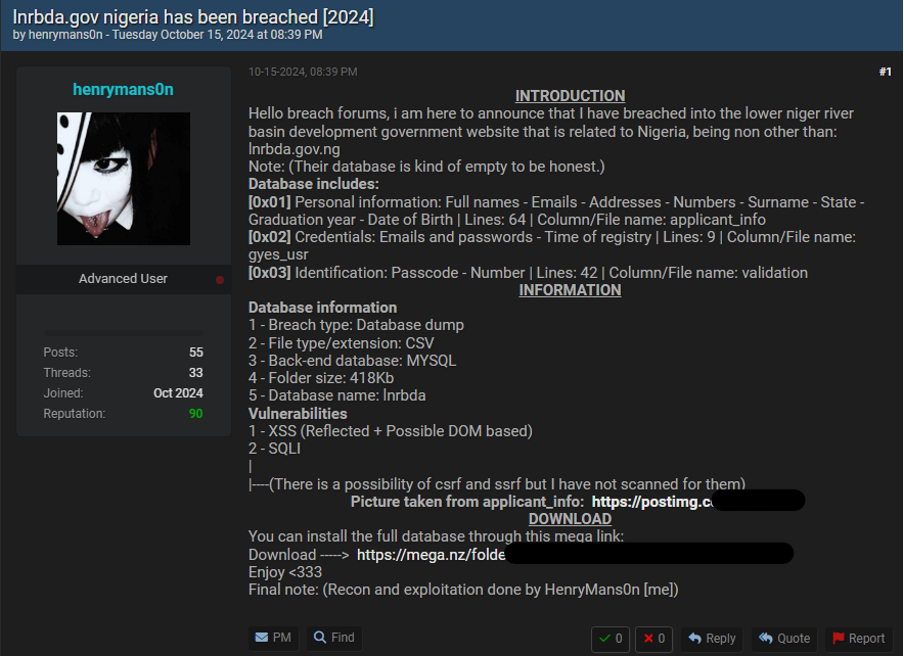
At the time of writing, none of the claimed victims have acknowledged the group’s claims nor announced that they have suffered any recent cyber incidents. However, data allegedly stolen from River Basin Development Authority was shared on BreachForums on two separate occasions in 2024. These posts were created by two different users, thoughis unclear whether these are separate leaks or one and the same. It is also unclear how or whether these are related to GD LockerSec’s claims, or whether the group used the already-leaked information during any attacks it carried out. It is realistically possible that GD LockerSec has obtained this data from BreachFroums and is attempting to pass the leak off as its own.
Manifesto and Motivation
The group’s About page provides insight into its alleged composition, targeting, and aims. It states that GD LockerSec members are from different countries and have only financial motivations. It stipulates that the group does not allow its members to conduct attacks against “non-profit hospitals” or “some [undisclosed] non-profit organisations”, members of the Commonwealth of Independent States (CIS), Cuba, North Korea, or China. The rules also expressly forbid attacks against organisations which have already paid GD LockerSec a ransom.
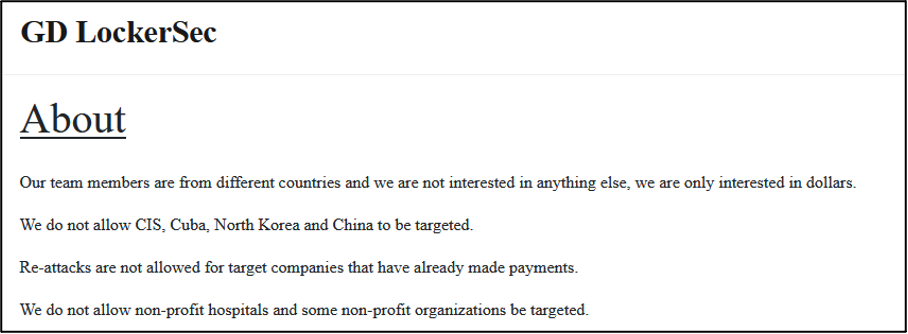
RaaS Operation
Though Cyjax has not identified samples of a GD LockerSec ransomware executable, the group’s DLS refers to a “decryptor”. This likely means a key for decrypting encrypted files and directories. GD LockerSec notes that should victims fail to receive a decryptor following a ransom payment, they can contact the group directly to receive one. This suggests that the group either conducts encryption-based attacks or is at least attempting to masquerade as using such tactics. It is as yet unclear which, if any, ransomware executable the group uses. Consequently, it is also unclearwhether this is proprietary or made using a ransomware builder belonging to an existing group.
On both the About and Contact pages of the GD LockerSec DLS, the group makes reference to an apparent Ransomware-as-a-Service scheme. Here,it promises that affiliates will receive 90% of ransoms paid by victims, with GD LockerSec keeping the remaining 10%. Such wording is typical of RaaS advertisements. However, further details of such a scheme are unavailable.
Threat Assessment
GD LockerSec has so far claimed attacks against four organisations and has shared download links for data allegedly stolen from two of them. However, one of these two organisations allegedly experienced at least one data leak in 2024. As such, it is unclear whether GD LockerSec is attempting to claim responsibility for these leaks, or whether they are unrelated. Cyjax has not identified any concrete information surrounding any tactics, techniques, or procedures (TTPs) the group may use, and subsequently cannot assess the extent to which GD LockerSec is technically capable.
To access our full intelligence repository containing detailed profiles like this one, covering extortion groups, advanced persistence threat groups (APTs), data brokers, hacktivists, initial access brokers, and more, click here to take a test drive of Cymon.
Receive our latest cyber intelligence insights delivered directly to your inbox
Simply complete the form to subscribe to our newsletter, ensuring you stay informed about the latest cyber intelligence insights and news.
