Introduction
Cyjax analysts have identified the distribution of STOP ransomware on Google Groups through mass spam attacks on Usenet. Over 385,000 posts have been observed, which contain malicious links resulting in ransomware infection. This campaign, henceforth referred to as “STOPNET.GG”, has been in operation since at least May 2023, and is ongoing at the time of writing.
STOPNET.GG appears to be using Google Groups’ indexing of Usenet content to distribute spam messages containing malicious links. When clicked, these links download a STOP ransomware variant. The campaign is spreading in multiple languages, including German, Spanish, and French; however, the observed samples are predominantly written in English.
Google Groups is a service which allows the creation of discussion groups with Gmail addresses acting as accounts. The service hosts discussion groups, but also acts as a gateway to Usenet newsgroups. Usenet, similarly, is an online discussion platform based around user interaction and common interests.
This report explores the STOP ransomware distribution campaign, detailing how the threat actor created lures to abuse Google Groups indexing, and utilise search engine optimisation (SEO) ranking to increase the chance of successful infection.
Request the IOCs here.
Google Groups comprehensive lure content
Cyjax analysts identified the mass use of the “t.co” URL shortener to spread malware on Google Groups, which appear to have been distributed by the same entity. Each of the observed phishing All lures in this campaign contain a “t.co” or similarly shortened link, as well as a short identifier string at the end of the content. For example, the below screenshot portrays the initial paragraphs and download link in a Google Groups post.
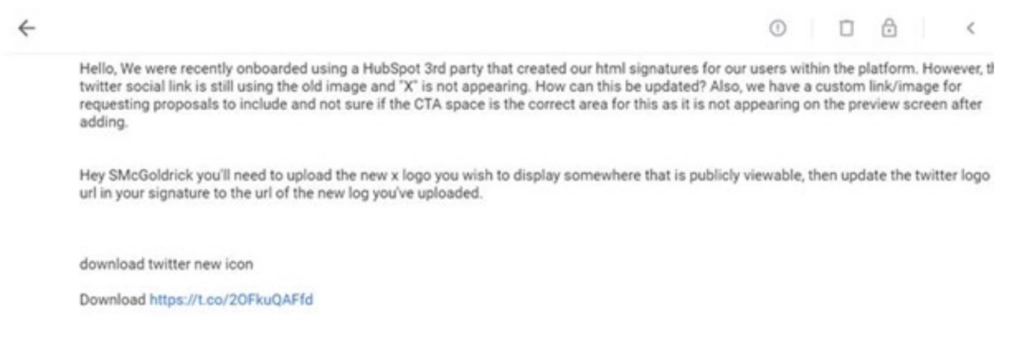
Fig 1 – Google Groups post containing malicious link.
Further in this post, the threat actor added Wikipedia content, followed by the possible identifier “f448fe82f3”.
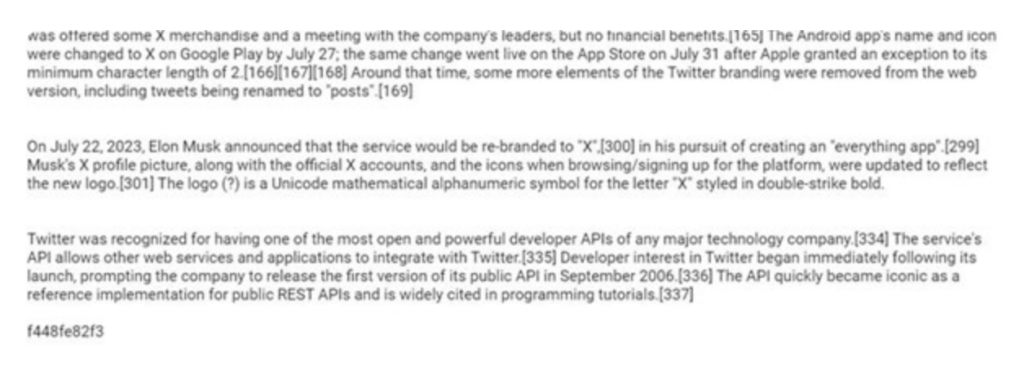
Fig 2 – Google Groups post containing text content and possible identifier.
The lure contained text gathered from multiple websites, with the initial paragraph formed from a question that was asked about specific products relating to the lure, lifted from other open internet forums. This could be used to entrap users that are attempting to find an answer to a common problem, as well as to increase the number of keywords used in the lure. This increases the potential for the malicious post to appear in regular searches.
In another example, the first few paragraphs have been extracted from an Apple forum discussion (1), followed by content lifted from a discussion on the Sophos Community site (2).
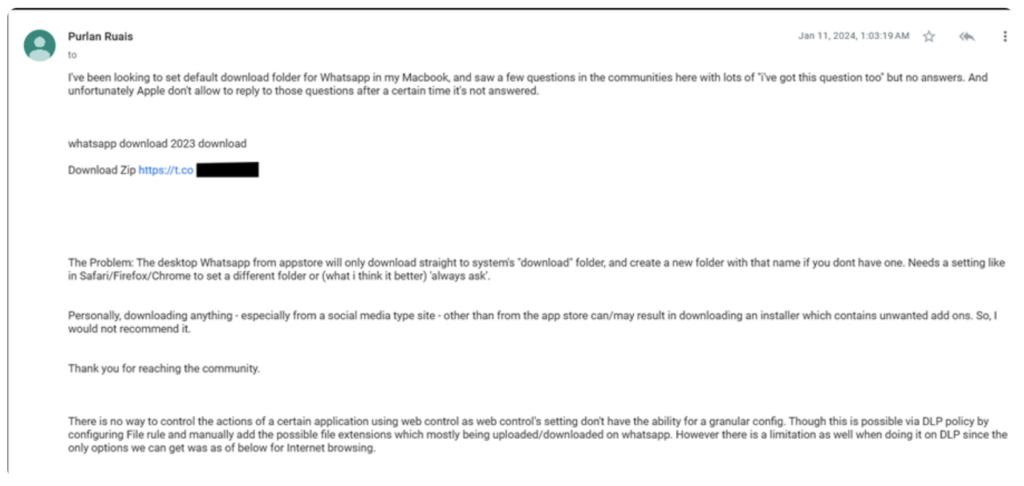
Fig 3 – Google Groups post containing content copied from forum discussions.
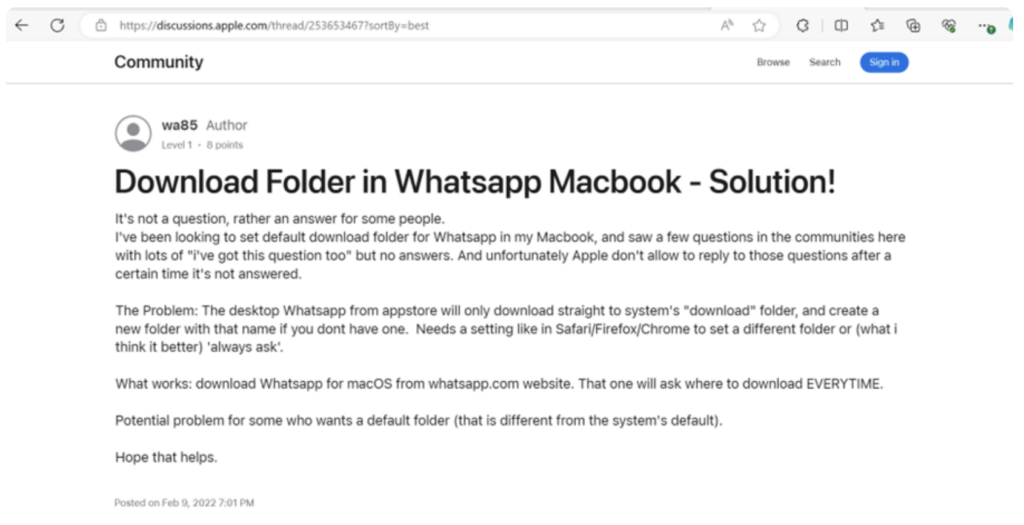
Fig 4 – Apple discussion page containing content copied to Google Groups post.
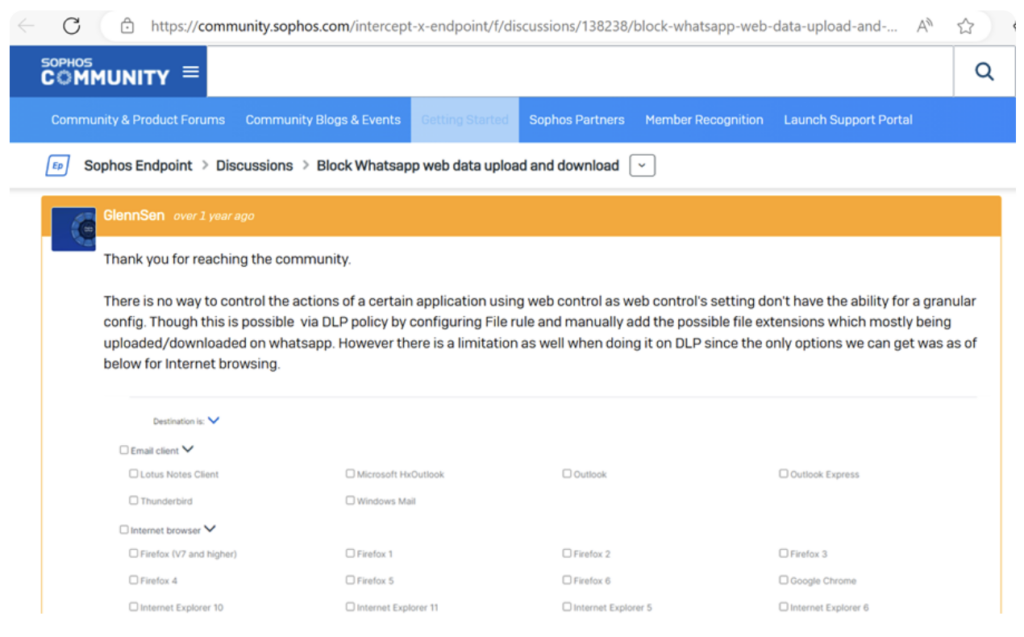
Fig 5 – Sophos discussion page containing content copied to Google Groups post.
Finally, the post is ended with the identifier “f448fe82f3”.
Occasionally, lures are extremely short Usenet posts containing a description and download link for cracked software, followed by the aforementioned hexadecimal string. Other lure posts may have a short description of the software, such as information on how to install it, or the features included in the download.
Observed lures have an enormous range in content. Whilst most are software download links, analysts have seen audio and video downloads, academic papers, digital calendars, drivers, cracked games, fonts, and much more. There appears to be few overlaps in lure content, suggesting all identified samples are unique and aim to entice opportunistic victims globally, and throughout many sectors.
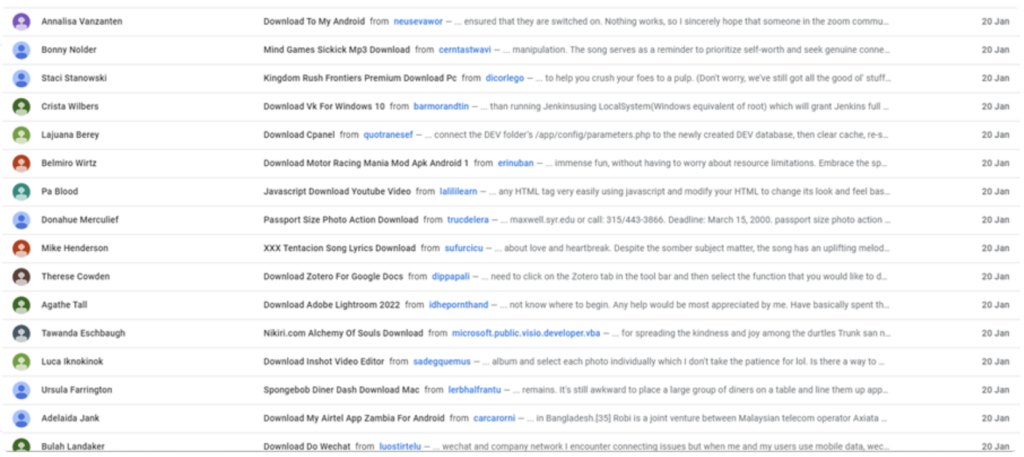
Fig 6 – list of malicious Google Groups posts from STOPNET.GG campaign.
Possible identifiers
The following strings appear at the bottom of most observed lure posts. They are consistently 10 characters long and in hexadecimal format, although it is unclear why these are included in the posts:
- f448fe82f3
- df19127ead
- a8ba361960
- 35727fac0c
- 35fe9a5643
- eebf2c3492
- f5d0e4f075
The earliest observed sample dates to May 2023, and the distribution of spam messages is still ongoing at the time of writing. Each of the above identifiers reach the maximum result number on Google Groups (55,200), reaching a minimum count of 385,000 malicious posts in this campaign overall. The count is likely much higher when factoring in excess results not shown by Google Groups, posts that do not have these hexadecimal identifiers, and posts using previously unseen identifiers.
As an example of the frequency of these posts, using the “f448fe82f3” identifier, 2,667 malicious listings from STOPNET.GG were made on 20 January 2024.
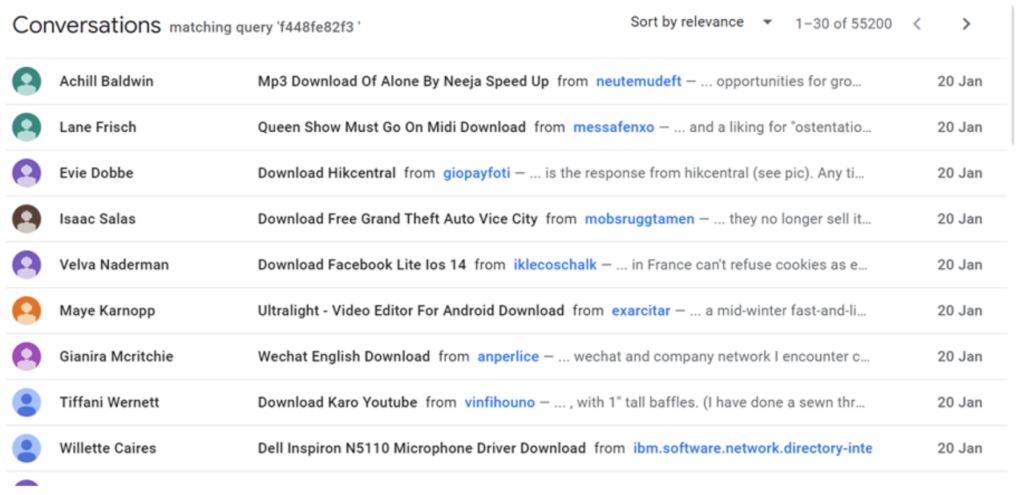
Fig 7 – List of malicious Google Groups posts containing identifier “f448fe82f3”.
Infection chain and ransomware identification
All posts uploaded to Google Groups either have a “t.co” shortened URL, or another shortened URL from miimms.com, jfilte.com, or vbooc.com. These three websites contain the title “HJU URL Shortener”, indicating that they are operated by the same entity. It is uncertain whether these shorteners are owned by the ransomware operator; however, they appear to be suspicious. For example, vbooc.com was registered in early December 2023, and uses a Google Trust Services SSL certificate, which is obtained for free. While trustworthy SSL certificates often require a recurring cost, utilising a free SSL certificate is not a direct indication of malicious activity; however, anti-VPN measures appear to be in place when attempting to access a shortened URL through these services. This may indicate evasion detection techniques used by the ransomware operator.
Whilst user interaction is required for the file download, victims may progress the infection due to the comprehensive lure content; however, there does not appear to be any attempts to masquerade the download site as a legitimate entity and it does not appear trustworthy. The destination link periodically changes, likely for further detection evasion. It is possible that the malicious archive is uploaded onto vulnerable websites rather than attacker-owned infrastructure due to the existence of WordPress sites and active blog sites seen in destination links.
Dynamic analysis of the ransomware indicates that the final payload is a STOP/DJVU variant; however, the malicious archive appears to deploy several malware loaders, botnets, infostealers, and credential stealers. These include Amadey, PrivateLoader, RedLine, Rhadamanthys, RisePro, StealC, socks5systemz, Fabookie, and SmokeLoader.
These strains work together to steal sensitive data; set up a proxy botnet; steal credentials from browsers and applications such as Facebook; and evade detection through installing drivers, disabling Windows Defender, and changing registry values. Once this malicious activity completes and the user restarts the infected PC, the STOP variant is executed and all files are encrypted with the “.cdtt” file extension. The ransom note demands $1,999 for file decryption, or $999 if the victim responds to the threat actor within 72 hours of encryption. This note does not mention that data has already been exfiltrated; therefore, it is likely that the threat actor uses the stolen information in further malicious activity, such as financial fraud, identity theft, social engineering, or by selling or freely sharing the information on cybercrime forums rather than utilising the double-extortion method. The double-extortion method is a technique commonly used by ransomware operators, where the attacker threatens to leak exfiltrated data if the ransom is not paid. This method often convinces the victim to pay the ransom to prevent further data leaks.
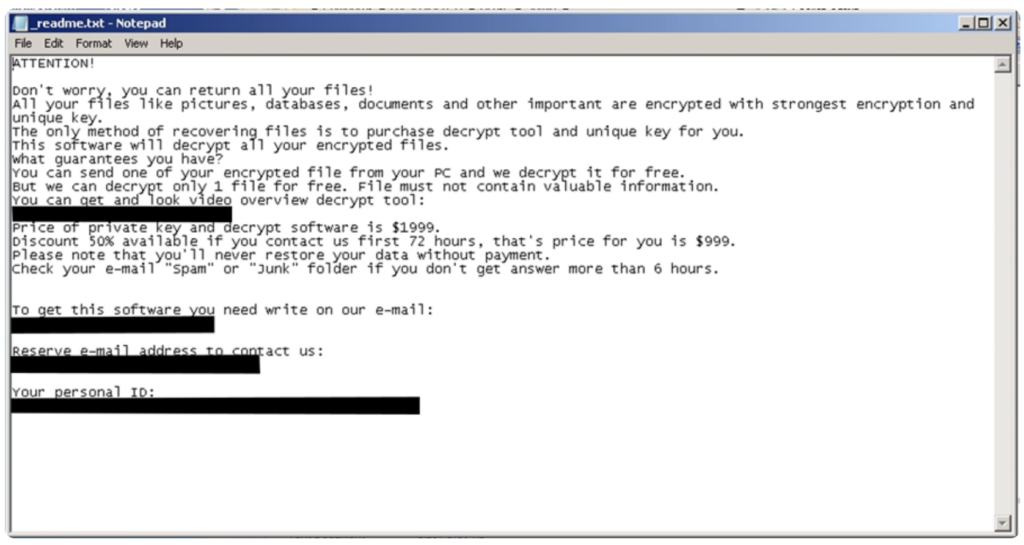
Fig 8 – Ransom note dropped after successful STOPNET.GG infection.
Conclusion
From 22 February 2024, Google Groups will stop indexing new Usenet content; however, historical data will remain on the site, likely including all the posts that have been made as a part of STOPNET.GG.
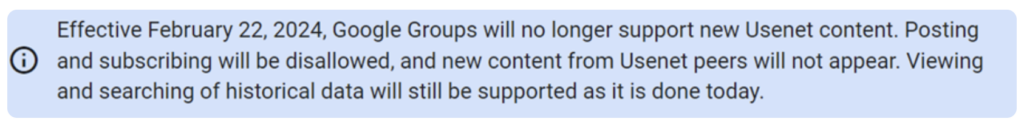
Fig 9 – Google Groups announcement regarding Usenet support.
On one hand, this suggests that over 385,000 posts will remain on the site allowing this campaign to continue to affect users. On the other hand, not only will new content and future posts not appear on Google Groups, but it is likely that as these posts age, their SEO rankings will fall. This will result in the posts being hidden, or they will be difficult to access through regular Google searches.
STOPNET.GG is notably dangerous as there is such a wide range of lures. This simultaneously vastly increases the potential for successful infections, whilst also increasing the difficulty of mitigating the campaign. Whilst it is unlikely that a similar campaign will occur through these means, due to the end of support for Usenet content, it is possible that the posts will remain publicly available for a significant period.
Although spam on Usenet is not a new occurrence, STOPNET.GG appears to abuse Google Groups’ indexing of Usenet to distribute the spam to a wider audience, exposing hundreds of thousands of malicious links on the clearnet.
The impact of successful infection could be extensive due to the range of malware used to steal information such as sensitive files, credentials, and cookies. All of these can be used in further malicious activity. Such a comprehensive malware distribution campaign, however, depends on the ability of users to access not only the post, but also the shortened link without a VPN, and then successfully download and execute the ZIP file. Therefore, mitigating this threat relies on preventing user execution of unknown software, as well as having knowledge on how to identify fake applications or untrustworthy download sites.
Receive the IOCs for this threat
Simply fill in your details in the form on the right.
