Honeywell creates and develops a wide range of products used across sectors, including manufacturing and industry. Researchers recently discovered three vulnerabilities affecting the Honeywell Experion Process Knowledge System (PKS), two of which were rated as critical. Experion PKS is a distributed control system (DCS) used for the automation of production lines and industrial processes. The critical vulnerabilities, designated CVE-2021-38395 and CVE-2021-38397, enable RCE or DoS, which may have a significant impact on day-to-day operations or lead to full system compromise.
The two vulnerabilities discussed in this blog stem from the lack of basic security processes such as sandboxing and sanitisation which allow an attacker to upload malicious files that are executed on the device instantly without any checks. One of the issues may also be leveraged to move laterally on the network, potentially allowing the attacker to install malware and become an undetected persistent threat on the network. There are a number of mitigations available, including security patches: these are not available, however, for all devices due to some being at end-of-life. For these, workarounds have been released.
Analysis
Honeywell Experion PKS is used to automate industrial processes: it can be used to aid manufacturing processes by increasing productivity. The PKS controller communicates with its configuration software, Experion PKS Configuration Studio Engineering Software, via TCP ports 55553 and 55555 which are used to configure the devices. One application within this suite is the Honeywell Experion Control Builder (contbldr.exe) which is used to program the logic of the controller. As this is native to every DCS/SCADA system, it is possible to change the programming of the device by performing a “download code procedure” which takes logic developed on the Control Builder suite and transfers compiled logic to the device and executes it.
This logic is compiled directly to the CPU’s machine code, which presents a security risk. To help mitigate this, a sandbox is typically used to prevent code from being executed on the native device. A sandbox is used in a very similar way to a virtual machine: running the code in a virtual environment that utilises the system’s hardware. However, anything run in a sandbox does not affect the host system, meaning that any malicious code can be terminated, leaving the host system unaffected. The PKS does not use a sandbox, memory protection or any other restrictions to ensure that malicious code is not executed on the native device. These security processes are crucial controls, especially when it comes to industrial control systems (ICS).
Researchers found that it is possible to mimic the download code procedure and use these requests to upload malicious arbitrary DLL/ELF files which the device then loads without performing any checks or sanitisation. This gives an attacker the ability to upload executables and run unauthorised code remotely and without authentication.
The ports 55553 and 55555 are not exposed to the internet therefore a previously established foothold in the network would be necessary. This can be achieved by phishing attacks on factory staff allowing for malware to be used to communicate with the device via the infected host. If exploited, these vulnerabilities may allow process values to be modified or the DCS to be used as a base from which to launch further attacks.
To fully understand these vulnerabilities, we need to look more deeply at how they work. A Control Component Library (CCL) is a library of control components that is loaded onto a controller to perform specific functions. These CCLs can be compared to an extension that is used to develop application-specific functionality with third party function blocks which are not supported by the standard libraries. The CCL format is a wrapper for DLL/ELF files. The executable is split up into byte blocks, the first four bytes being the CRC32 (cyclic redundancy check) of the executable. The next 128 bytes represent the name of the library, and the rest of the file is the actual wrapped DLL/ELF file.
These wrapped DLL/ELF files are libraries of code blocks that are used in the Control Builder software. When the CCL files are being parsed from the Control Builder to the PKS device there are no security validations such as signature checking or sanitization of the library names, therefore, it is possible for an attacker to perform a directory traversal attack to upload any DLL/ELF file they wish to arbitrary locations on the remote controller. In some cases, CCL files that are sent to the end devices get executed instantly without performing any security checks. The protocol used for parsing files from the Control Builder software to the device does not require any form of authentication. If in place, this would prevent unauthorised users from performing download actions. Therefore, an attacker may use the library to remotely execute code without authentication by downloading a malicious DLL/ELF file to the controller using the protocol and it will be instantly executed on the device.
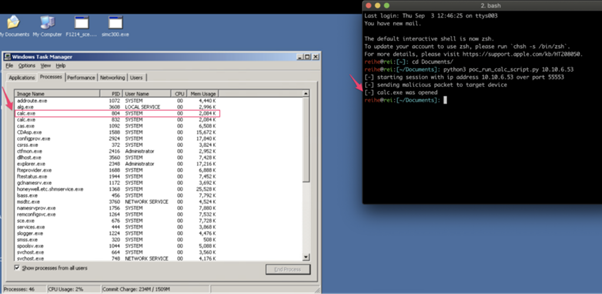
Team82 Proof of Concept showing how an attacker can achieve unauthorised RCE in Honeywell Experion Controller Simulator
Successful exploitation of these vulnerabilities may cause significant disruption to production lines or automated processes. The compromised device may also be leveraged to further exploit vulnerabilities in the native network, possibly allowing an attacker to move laterally to other hosts and perform reconnaissance or install malware, allowing the attacker to sit on a network, undetected for an unlimited time.
This issue, along with the many vulnerabilities to ICSs documented over the years, demonstrates the importance of focusing on the security of these devices. If overlooked – whether for fear of increased development time or a lack of understanding of the consequences of a successful cyberattack on a customer’s system – a brand’s reputation could be damaged and lead to a loss of customer trust. This is particularly the case in critical infrastructure processes, where any form of security risk and possible downtime is severe. As IoT devices become more prevalent in every sector, their security must not be overlooked.
Mitigations
Honeywell has said that the vulnerabilities affect its C200, C200E, C300 and ACE controllers. Patches have been released for C200E and C300. The C200 and ACE controllers, however, have reached end-of-life status, but mitigations are nonetheless available. More information about patches and mitigations can be found in the Honeywell support document. CISA has recommended users take defensive measures to minimise the risk of exploitation. Users should:
- Minimize network exposure for all control system devices and/or systems and ensure that they are not accessible from the Internet.
- Locate control system networks and remote devices behind firewalls and isolate them from the business network.
- When remote access is required, use secure methods, such as Virtual Private Networks (VPNs), recognizing VPNs may have vulnerabilities and should be updated to the most current version available. Also recognise VPN is only as secure as its connected devices.
These recommendations also include reminding organisations to perform proper impact analysis and risk assessment prior to deploying defensive measures.
