We recently analysed an interesting new dotNet banker from Brazil. The malware is not particularly sophisticated and only reveals itself under certain conditions. Further, it contains no obfuscation, making the analysis reasonably simple.
Delivery
The malware was being delivered via email, utilising a very simple exe loader contained inside a zip file. This requires the user to open the zip and run the loader; we did not observe any exploits in use. The final payload is added as a scheduled task and executed after the loader has run.
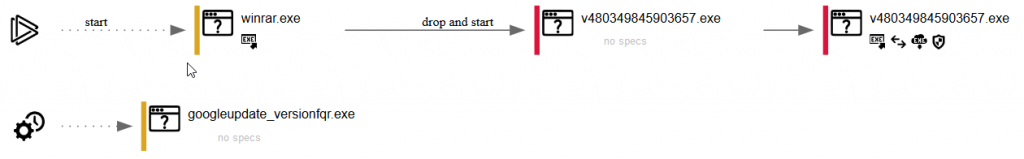
The Final Payload
After the final payload executes, the malware lies dormant and waits for certain conditions to be met. We immediately determined that the malware is written in dotNET and compiled for Microsoft Windows x86 systems.
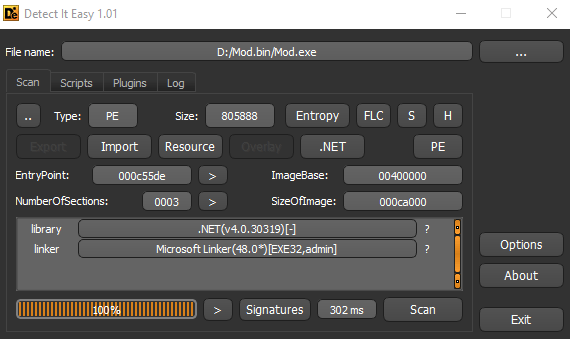
Interestingly, the executable is not packed in the usual way. As a result, we were able to use a dotNET decompiler to view the source code. Opening the executable using dotPeek presented us with a limited main routine that serves only to launch a second routine. Notably, it contained references to Costura and MOD3:
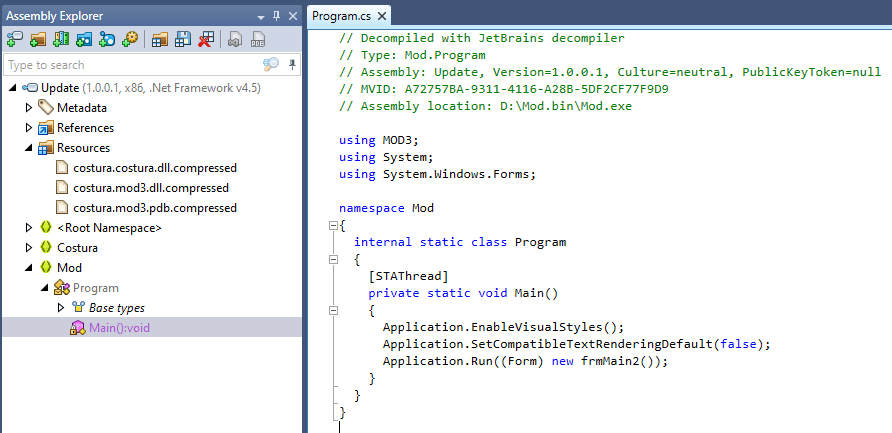
Costura is a plugin for Fody, which enables developers to embed dependencies (such as DLLs) as resources packed inside the final dotNET executable. These can then be extracted and decompressed using PowerShell.
Decompressing and decompiling mod3.dll presented us with additional code, including frmMain2, which is referenced before the mod3.dll is unpacked:
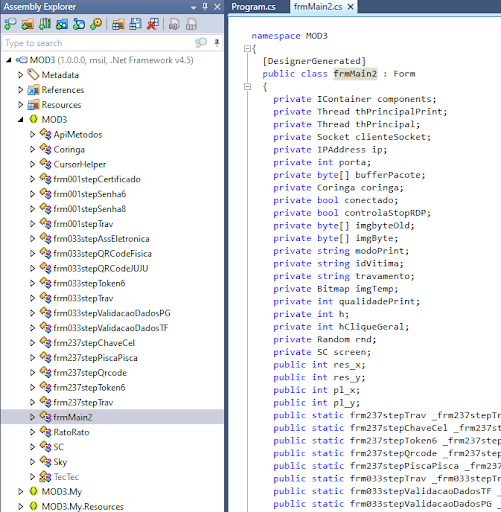
None of the code has been obfuscated, and this allows us to read it and gain an understanding of how the malware works.
Certain Conditions
An analysis of the decompiled code indicated that this malware only targets a select number of banks. It does this by reading the system process list and checking the titles of process windows to identify files connected to popular Brazilian online banks. The malware also checks to ensure that the web browser is not currently on a Google search results page.
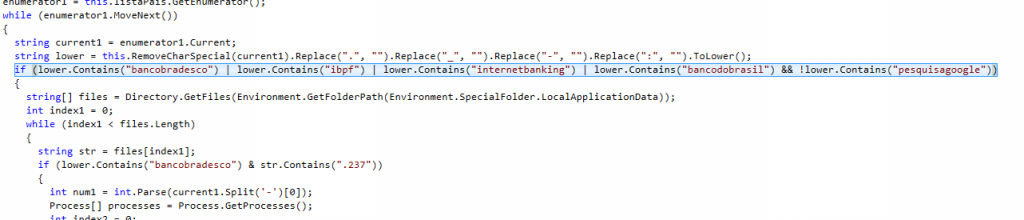
From the screenshot above we can see that the malware is targeting the following Brazilian banks:
Banco do Brasil
Sicredi (ibpf)
Banco Bradesco
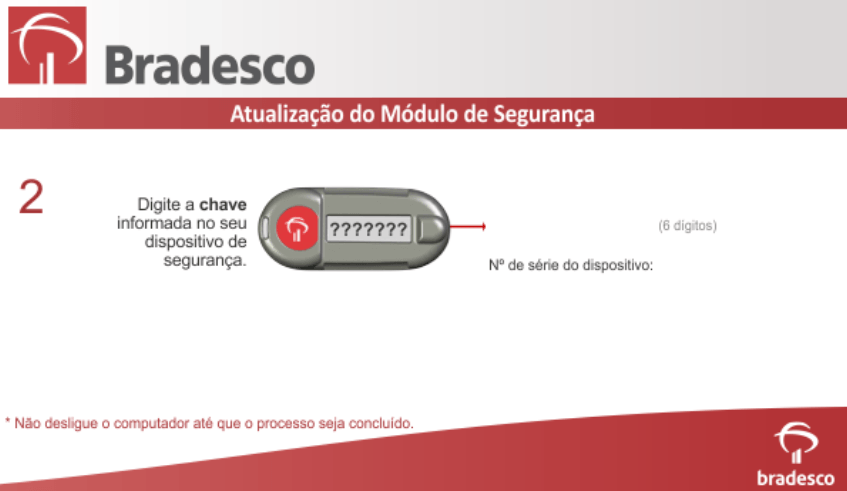
Once the conditions are met, the malware generates various message boxes and forms (examples below) intended to capture the victim’s credentials and forward them to the C&C server via a TCP socket.

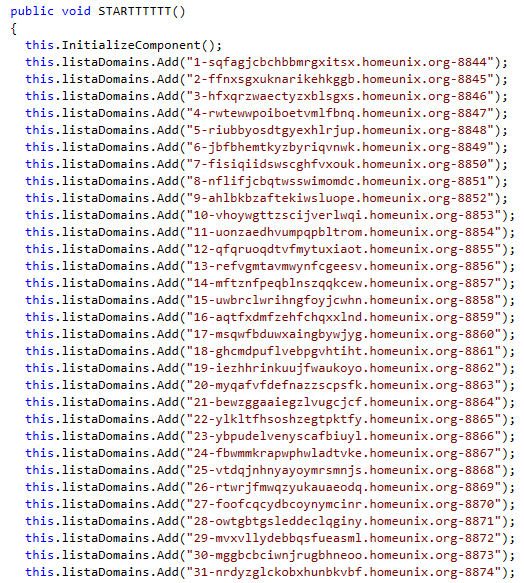
The malware includes the following list of C&C servers which were embedded in the code with no attempt at obfuscation:
Conclusion
Although this is a fairly unsophisticated piece of dotNET banking malware, it has the potential to be incredibly effective. The forms are well designed and the malware only triggers when certain online banking pages are opened in the browser. It persists with reboots via a scheduled task and can capture the bank’s own 2FA from the user. At the time of publishing, the detection rate is fairly low, with only 10 out of 70 engines currently detecting it as malicious.

