Credential stuffing, a simple attack that involves running lists of stolen credentials against various services in the hopes of finding password reuse, is one of the most popular ways cyber criminals acquire accounts to sell on Darknet marketplaces.
Victims often don’t know the difference between credential stuffing or an actual exploit or breach, and this can lead to some very damaging PR for the target company, especially when this particular type of attack is performed at scale.
The theory behind credential stuffing is very simple: the attacker acquires the victim’s credentials for Service A and then tests those credentials against Service B, Service C and Service D to see if there is a hit.
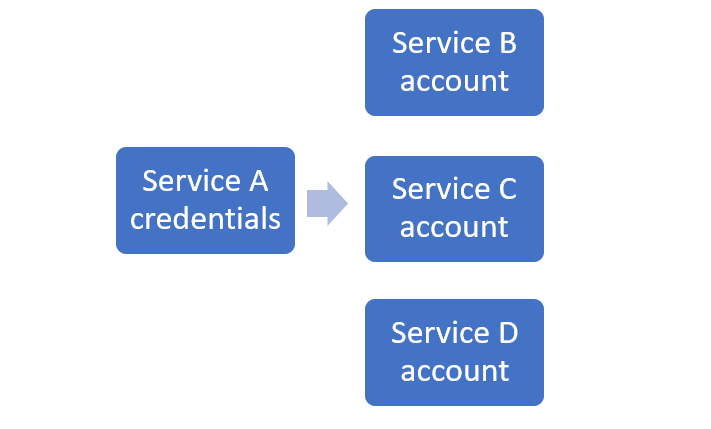
The attacker is also able to build a list of passwords from acquired credentials in order to perform dictionary attacks. For example, you may have thought that @@Jenny8675309@@ was a strong password with numbers, letters and symbols and a password that you haven’t used for any other accounts. Unfortunately, someone else on the other side of the world also thought this and their password was phished and sold as part of a larger list of music-related passwords or passwords with English names; the attacker now has your password and will eventually get a hit on your account without compromising your computer or phishing you personally.
Why is credential stuffing a growing threat?
There are three simple factors that we believe have contributed to the recent explosion in credential stuffing:
- The sources of compromised accounts are growing exponentially with data breaches occurring almost daily, giving attackers a limitless supply of fresh credentials, not to mention the billions of credentials already leaked over the past few years.
- It’s easy – very easy. In fact, there are Graphical User Interface (GUI) tools freely available for anyone to use that will check hundreds, if not thousands, of accounts in an hour.
- It’s profitable: cyber criminals might sell a single account for only €3 (which would normally cost around €15 per month if bought legitimately on a service such as Netflix, for example). As the threat actor will have 100s of these accounts available for sale, with only a small percentage going to the marketplace, you can imagine the profits soon start to stack up.
OpenBullet – the golden gun
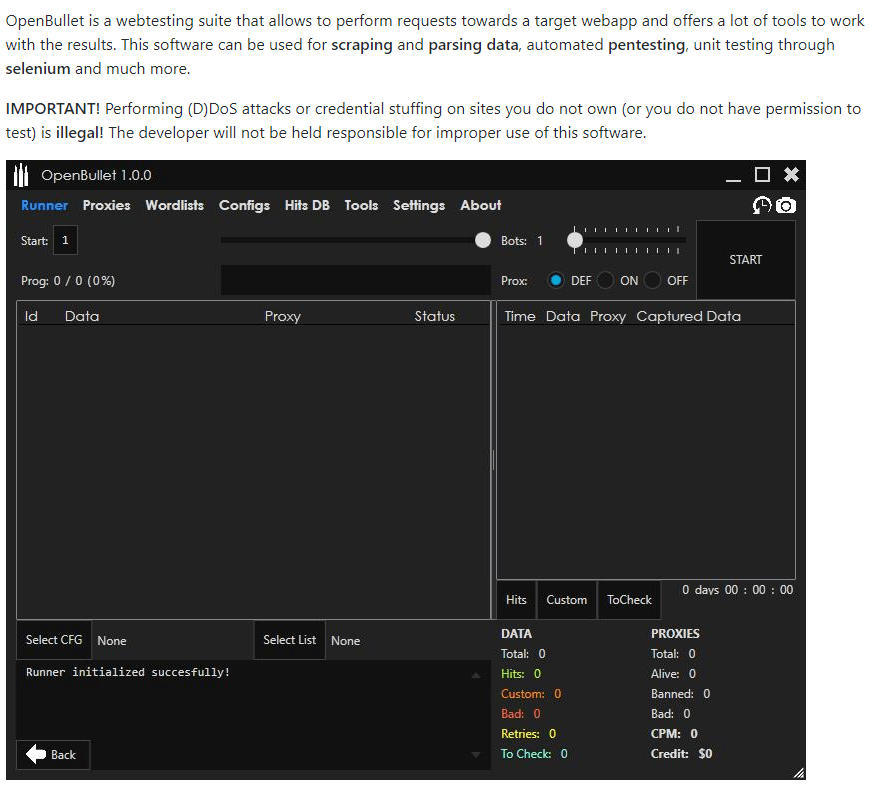
Next, we are going to look at OpenBullet, one of the more popular tools used for credential stuffing attacks. There are a few different tools out there with only minor differences, so we felt it enough to assess just one of them in this article.
(source)
OpenBullet is open source and freely available on GitHub to either build yourself or to download as a precompiled binary. It is worth noting that the developer does include a disclaimer on the front page stating that OpenBullet should not be used to attack targets that you do not own or have permission to test.
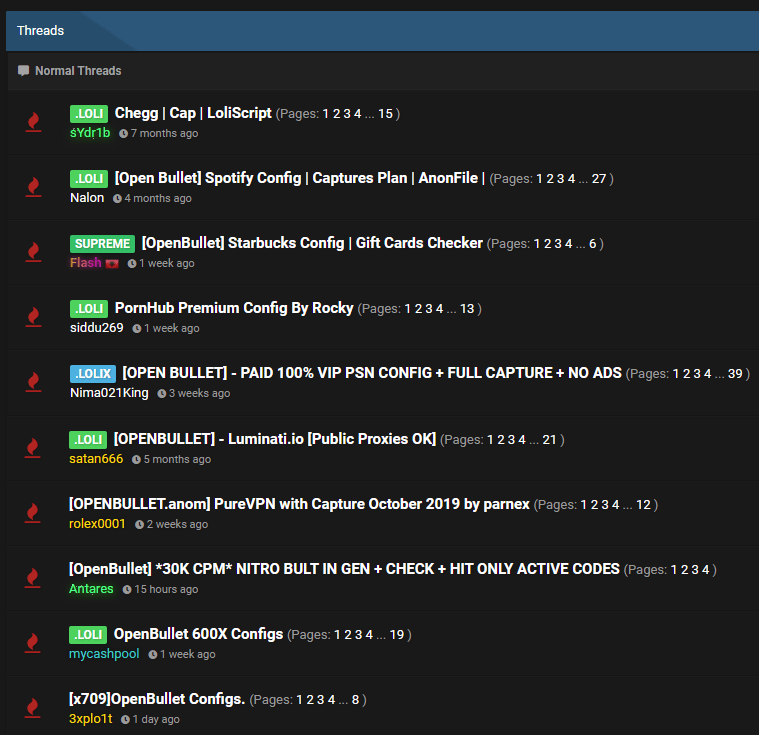
The important part of using OpenBullet for credential stuffing concerns the configs: these are configuration files that you can import into the software in order to target specific services. Some of these configs are available for free, and some you can find for sale on various markets or dedicated websites.
(source)
Once the appropriate config has been acquired, the threat actor needs a list of proxies to load into OpenBullet; again, these are sold in large lists or given away for free. Many of the proxies on these lists tend to be from botnet operators infecting consumer routers or computers with Remote Access Trojans (RATs).
Finally, the cyber criminal loads a list of stolen credentials from a public data breach or a private list they have acquired and hits “Start” in OpenBullet. Once the software has finished, they are presented with a list of hits along with any other information the config automatically harvests, such as account expiry date or balance.
Profit
We find that cyber criminals like to use the service shoppy.gg to sell their stolen accounts easily.
(source)
With Shoppy, they can configure an automated online store that accepts most popular cryptocurrency as well as other forms of payment, and that they can load the stolen credentials into. They then advertise their personal Shoppy link on Darknet forums and wait for the funds to roll in. Once the store is empty, they simply repeat the process with OpenBullet and load in fresh credentials.

(source)
Conclusion
Credential stuffing poses a reputational risk to companies.
Unfortunately, users are often unable to understand the difference between credential stuffing or a company data breach and will jump to the worst conclusion, taking to social media to voice their concerns. To an untrained eye, credential stuffing done at scale can look to be a data breach: in the past, we have seen large media outlets cover incidents in this way due to the uproar from victims.
This simple form of attack is not going away and will continue to grow through 2020. Service providers can help fight this by enforcing 2FA/MFA, implementing better user notifications for account logins, and more stringent mass login detection on the back end, thereby greatly reducing the ability to quickly harvest accounts in this way.