Introduction
In 2022 and 2023, there has been a significant increase in threat actors uniting under singular causes. This focuses their attacks and increases their efficiency. Long-standing multi-group attack campaigns are constantly occurring in the hacktivist environment, and state-sponsored or country-affiliated threat groups act on behalf of and in support of their respective governments. There are established common goals and targets that naturally lead to cooperation. Factors such as these result in the creation of officially affiliated collectives and coalitions, when previously disparate groups came together under a common goal. Recent events such as the Russia-Ukraine war, as well as ongoing annual hacktivist campaigns and other geopolitical developments like the Israel-Palestine conflict are contributing factors to the increased joint threat activity Cyjax analysts have observed in the past two years.
This report aims to highlight the threat actor unification Cyjax has seen, the resulting increased capabilities this has given the collectives, and the impact this has had on the threat landscape. The report will also explore the factors contributing to threat actor cooperation and interactions on Telegram, the platform on which most threat actors are typically active, coordinate attacks from, and post successful reports for their subscribers.
Threat groups often consist of several actors and can be state-sponsored or act according to their own goals. Examples featured in the report include @AnonymousSudan and Lazarus. While @AnonymousSudan is allegedly Sudanese and acts with pro-Russian interests, they are not state-sponsored; however, @Lazarus is a state-sponsored threat group operating in the interests of the North Korean regime. The term “collective” has been used in this report to describe official collaboration between threat groups with the establishment of a common term or designated name, such as @TheFiveFamilies.
Geopolitical developments
Russia-Ukraine War
As part of the ongoing Russian-Ukraine war, cyberattacks have come to the forefront of non-physical combat, causing disruptions not only to the warring countries, but also to those supporting them. Notorious threat actors @Killnet and @AnonymousSudan have been heavily involved in cyberattacks against Ukraine and organisations in supporting countries.
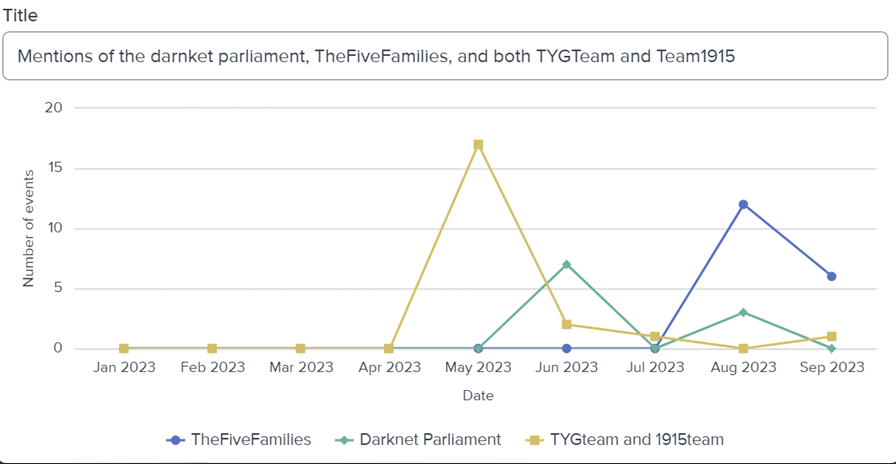
In June 2023, @AnonymousSudan and @Killnet claimed to have held a “darknet parliament” meeting to agree on common targets. They then began to target European bank transfer systems, and other known threat groups reposted and showed support for them on Telegram. @Killnet is a well-known group thought to have close relations with the Russian government. @AnonymousSudan has previously exhibited affiliation to @Killnet, and often conducts attack campaigns with pro-Russian sentiment. While the existence of the “darknet parliament” is disputed and @Killnet has claimed that the name was created as a joke, the joint action between the threat actors and continued cooperation suggests that the collective does exist, regardless of its identifier name.
Like the alleged “darknet parliament”, several pro-Russia hacktivist groups announced in early September 2023 that they had formed a new alliance under the name @Solntsepyok (Солцепек). The groups include @Beregini, @RaHDit, @Killnet, @Zarya, @JokerDNR, @Wagner, @XakNet Team, @NoName057, @BlackWolfs, @BEARITARMY, @Voskhod, @PeoplesCyberArmy, @PatriotBlackMatrix, @DEADFOUD, @Xecatsha, @BEARSPAW, @ZulikGroup, and @AnonymousRussia.
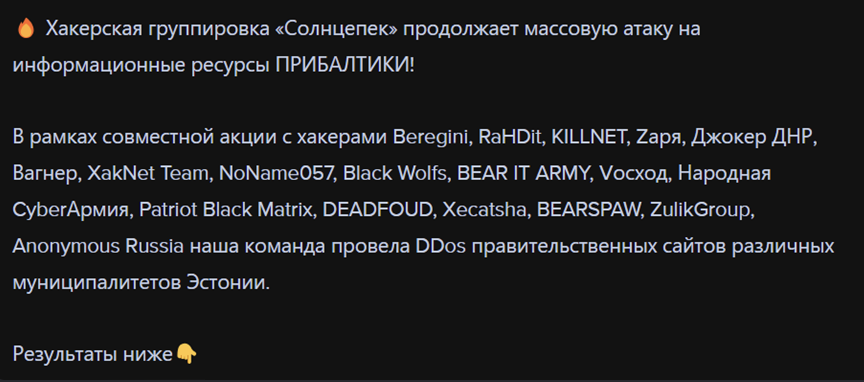
These collectives – the “darknet parliament” – and the pro-Russia hacktivist alliance both appear to have been formed since the start of the Russia-Ukraine war. Large-scale geopolitical developments such as the ongoing conflict often lead to changes in the threat landscape, with a significant increase in cyberattacks from both sides. This is likely to have been the main contributing factor for the creation of the unified threat groups.
@Killnet, for example, has a longstanding history of subgroups – threat actors that have previously been identified as standalone, but have become very closely affiliated with the group. @AnonymousSudan was briefly confirmed as a @Killnet subgroup; however, it later became a standalone group, working alongside several threat actors with no official unification until the “darknet parliament” was first mentioned. Other named subgroups or affiliated members include @XakNet, @Beregini, @CyberArmy, @AnonymousRussia, @RaHDit, @DPRJoker, @NoName057, and @Zsecnet. This collective includes threat actors that operate in isolation regardless of their many overlaps. Whilst Solntsepyok may conduct attacks to forward the collective’s goals, the threat actors still act independently.
In a less official capacity, analysts have observed pro-Russian threat groups reposting successful attack announcements by other groups, propagating the news to other threat actors as well as the public. While this does not portray clear threat actor unification, it highlights interactions between the groups to further the overall development of their campaigns and common goals, as they continue to operate outside of the wider collective.
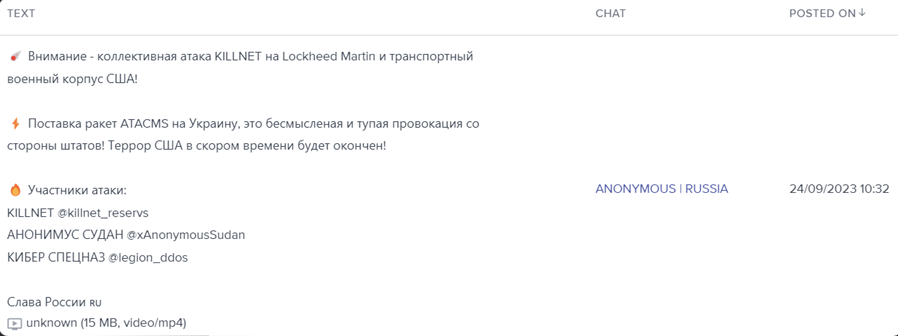
The Russia-Ukraine conflict appears to have altered the distinction between state-sponsored and standalone groups. While originally, state-sponsored threat groups were either formed or funded by the government, the war has seen the creation of groups consisting of volunteers, facilitated but ultimately not employed by the state. Retaliating to the constant stream of attacks from Russia and pro-Russian threat groups, and at the at the request of the Ukrainian government, hacktivists formed a large volunteer-led organisation named @ITArmyOfUkraine in February 2022. The group conducts cyberespionage against the Russian military, as well as defence operations to protect critical infrastructure. It consists of individuals with cybersecurity experience, volunteering to aid Ukraine and oppose Russia during the war, with 162,000 subscribers on their Telegram channel as of early October 2023.
In an interesting parallel to Russia’s use of boots-on-the-ground PMCs (Private Military Companies) such as Wagner, @Killnet attempted to rebrand itself as a cyber-based PMC, or a “private military hacker company” in early 2023. The group’s members stated that their “altruism” had ended and that they would offer their services to private and state sponsors, potentially altering their future options for unification.
Israel-Palestine conflict
On 7 October 2023, Palestinian militant force Hamas led a large-scale invasion against the Gaza Strip, effectively resulting in a declaration of war from Israel, counter-offensive measures, and the resumption of military conflict. As a result, both independent hacktivists and country-affiliated threat groups have initiated cyberattacks against both sides.
At a baseline level from 9 October, researchers identified a total of 39 threat groups involved in cyberattacks against either Palestine or Israel. This has risen to a total of 100 confirmed active groups at the time of writing – 77 pro-Palestine, 20 pro-Israel, and three neutral. Well-known threat actors such as @Killnet, @AnonymousSudan, @TeamInsanePK, and more have participated in cyberattacks against each side. It can be said that these groups are working towards common causes: either to cause a disadvantage for one side of the conflict, or to aim for peace. Regardless of the ideals and goals of these threat groups, they are unified in their attacks against government, military, financial, energy, media, and telecoms entities on both sides of the conflict.
Interestingly, the Israel-Palestine conflict has brought about an isolated incident in which threat actors have spoken against the actions of other groups. @CyberArmyofRussia has condemned @Killnet’s participation in the conflict, stating that they are against the group’s actions, and have urged other people to stop financially supporting them and unsubscribe under the hashtag #STOPKillnet. This may indicate that the same factors contributing to threat actor unification can also result in disagreements and disputes between them. This point can be examined further in the dissolution of ransomware group @Conti. The pro-Russian group detailed their allegiance to Russia at the start of the Russia-Ukraine war. Many of its members were unhappy with this announcement, effectively resulting in them being targeted by threat actors supporting Ukraine, and an insider releasing full leaks of internal communications. The group finally officially disbanded on 6 May 2022.
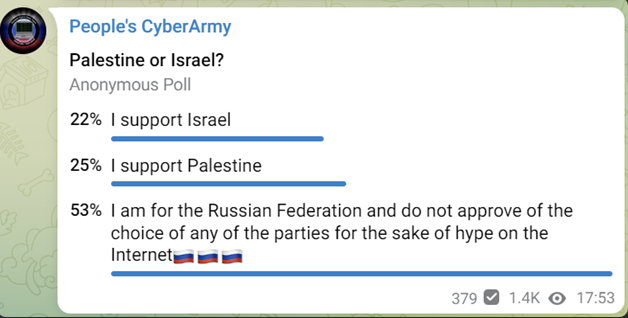
Perhaps to prevent a similar dissolution of the threat group, the @CyberArmyofRussia, also referred to as People’s CyberArmy, used their Telegram channel to conduct a poll to ask both members and subscribers within the channel whether they support Palestine or Israel, or whether they are neutral. While this may have been used a precursor to the group publicly condemning @Killnet’s participation in cyberattacks against the countries, it could also have been a method with which to gauge their members’ and subscribers’ sentiments towards the conflict to prevent internal disagreements with future attacks. The group has since remained neutral and has not conducted attacks against either side.
As the Israel–Palestine conflict and Russia-Ukraine war progress, it is highly likely that more threat actors will continue conducting cyberattacks against valuable targets, increasing the cooperation and collaboration between groups and collectives.
Hacktivist groups and campaigns
@TheFiveFamilies is another example of a recently formed threat group. This is a coalition consisting of @SiegedSec, @GhostSec, @Stormous, @Blackforums, and @ThreatSec. It was formed in August 2023 with the alleged aim of unifying hacktivist threat groups and forming an effective controlled sphere for their causes.
The collective consists of the leaders of the five threat groups and has been created under the premise “to establish better unity and connections” for threat actors, as well as to expand their hacktivist operations. As a result of this coalition, the #OpCuba campaign was revived, with hacktivists initiating attacks against Cuba, specifically targeting government corruption in response to law enforcement repression of protesters. This may lead to additional groups joining the collective. Additionally, @GhostSec was seen collaborating with the @Stormous ransomware group, highlighting that threat actor cooperation encompasses groups with disparate tactics, techniques, and procedures.
On a larger scale, hacktivist campaigns such as #OpIran, #OpIsrael, etc. often comprise a set of groups consistently targeting a government and country, with noticeable interaction between the threat actors, regardless of each constituent group’s personal aim. This again demonstrates that while hacktivist groups may have different objectives and ideologies, they may form larger collectives around a common goal. A common occurrence seen in threat actor Telegram channels is the reposting of successful attacks from different threat groups. This is most often observed in the same campaign – such as in the ongoing #OpIndia, with hacktivists reposting announcements from affiliated threat actors, whilst also mentioning other known participants. @TeamHerox is a hacktivist group with no country affiliation acting against government corruption; it carries out attacks in campaigns such as #OpIndia. As seen in a captured message section below, many hacktivists are working together to target India during the campaign.
OpIndia.
As previously reported in the Cyjax blog “Threat actors targeting Israel and India”, the hacktivist groups @Team1915 and @TYGTeam are known to be closely affiliated. They often join others in large-scale campaigns such as #OpIran and #OpIsrael to conduct attacks including distributed denial of service (DDoS), defacement, and data leaks. Their close affiliation is further highlighted by similar activity on their respective Telegram channels: both posted references to the aforementioned blog within nine minutes of each other.
These groups are known to cooperate, share news of each other’s successful attacks, and act towards the same goals, but they have not publicly announced any official affiliation. This could indicate private unification, and suggests that regardless of official ties, there is private communication between the groups.
State-sponsored groups
Countries employ state-sponsored groups to perform attacks for several reasons. They may target financial organisations to raise money for the government, other threat groups, or the agency employing them. Other groups may attack political adversaries for cyberespionage, data deletion, or service disruption. Targets can include critical infrastructure and the media, both for the propagation of misinformation, and to gain insider information.
Threat groups are often created with specific targeted verticals and TTPs respective to their goals. For example, North Korean APTs (Advanced Persistent Threat) @Lazarus, @Andariel, @BlueNoroff, and the @ElectronicWarfareJammingRegiment all have overlaps in infrastructure and are believed to operate as part of a hacking unit referred to as Bureau 121, and are thought to operate largely to fund North Korea’s nuclear and military ambitions. @Lazarus, in particular, appears to have three main objectives – data destruction, sensitive data exfiltration, and monetary theft. The group was responsible for several large cryptocurrency heists including against Ronin and the Horizon bridge, stealing hundreds of millions of dollars’ worth of cryptocurrency in each attack. Additionally, the group has previously targeted banks such as a heist against Bangladesh’s national bank. If the attack was successful, they would have stolen $1 billion; however, only five of the transactions were accepted.
@Lazarus is thought to have subgroups that allow it to operate more efficiently. For example, @BlueNoroff is believed to conduct attacks for monetary gain, in response to heightened global sanctions on North Korea. @BlueNoroff acts separately to @Lazarus and has distinct TTPs, aiming to steal funds through direct interaction with employees, conducting social engineering by masquerading as trusted partners after comprehensive reconnaissance. @Lazarus, however, has accrued funds through fake job advertisements from companies such as Lockheed Martin, deploying malware through malicious macros. Whilst these state-sponsored groups have defined TTPs, infrastructure, and goals, they have major overlap and often cooperate under the Bureau 121 umbrella.
An example of threat actor unification outside of Bureau 121 in North Korea is the joint campaign between @BlueNoroff, @Kimsuky and @Lazarus. @Kimsuky, a cyberespionage APT thought to be part of the North Korean General Reconnaissance Bureau, appears to operate separately from Bureau 121 whilst still acting on behalf of North Korea. The three groups were involved in joint targeting of the global maritime sector between December 2022 and January 2023, a previously unseen level of overlap in threat activity in North Korea.
A country’s specific cyber-related requirements, political situation, and geopolitical developments contribute to the need for state-sponsored threat groups. As a result, not only are these groups created, but they may be required to cooperate with others to achieve the government’s objectives. This may be to target specific sectors, as seen in the cooperation between @BlueNoroff, @Kimsuky, and @Lazarus. By working together as a collective, the state can create efficient and isolated groups with specific skills, resources, and TTPs. For example, a group can be established for intelligence collection, whilst another can rase monetary funds for the state or intelligence agency. It can also help to provide plausible deniability not only for the state, but also for other groups in the collective.
Researchers have observed, on a much smaller scale, collaboration between different state-backed groups. @Trickbot, a Russian-speaking cybercrime group with confirmed links to the FSB, released a project named “Anchor”, which allowed users to access APT-like functionality, loading known attack frameworks such as Metasploit and Cobalt Strike. A @Lazarus toolkit “PowerRatankba” was loaded using Anchor, highlighting a relationship between @Trickbot and @Lazarus, portraying collaboration between Russian cybercrime actors and a North Korean state-sponsored threat group.
Conclusion
Cyjax reporting has revealed a potential growth in threat actor unification since the start of the year, or an increase in public mentions of threat actor cooperation. This suggests that recent geopolitical and activism-related developments are contributing factors to the unification of standalone threat actors, collectives and state-sponsored APTs.
Geopolitical developments are a significant driving factor for threat actor unification. For instance, the ongoing Russia-Ukraine war has led to the unification of Russian and Ukrainian threat groups alike; however, these have become aligned due to their common causes, rather than directly due to the development. Russian threat groups have formed coalitions to target Ukraine, the EU, and the US in service disruption and data theft attacks, ultimately for Moscow to gain an advantage over opposing entities. Similarly, Ukraine-affiliated individuals and groups with threat actor capabilities are volunteering in the IT Army of Ukraine, creating a unified force to cause maximum disruption to Russian entities, as well as a robust cyber defence structure.
There seem to be pre-determined requirements to create the need for threat actor affiliation, with the largest one appearing to be a common cause. The “darknet parliament” was created to specify future targets by pro-Russian cybercrime groups; @ITArmyofUkraine was formed to combat cyber threats from Russia due to the ongoing conflict; hacktivist groups work to target specific entities in campaigns acting for singular causes that stem from environmental, governmental, or political factors; and state-sponsored groups are established to act in the specific interests of their respective governments, often as a reaction to geopolitical developments.
In a different approach, researchers noted a 450% increase in DDoS attacks from Q1 2021 to Q2 2022. This growth was due to the Russia-Ukraine war and associated cyberattacks, which may have been a major reason for the creation of collectives such as Solntsepyok. The geopolitical development had a consequential effect on the threat landscape and appeared to prompt threat actor unification. With such a significant increase in DDoS attacks, collectives have the capability to overcome DDoS prevention services and networking techniques to mitigate attacks, resulting in an increase in success. DDoS protection often relies on preventing requests from specific areas. With more resources from different regions allocated to specific targets, collectives can cause prolonged disruption and have a greater impact on their targets.
Through the establishment of collectives, threat actors can designate targets for larger-scale attacks, share TTPs, and greatly increase the precision of attacks, rather than individual groups attacking a widespread area. Whilst the establishment of collectives will not necessarily increase the threat of a specific attack type for individual entities, if groups with varied TTPs attack the same designated target, there may by an increase in successful campaigns as more attack vectors are used. By uniting under common causes, threat actors can also increase communicability, as when @TheFiveFamilies was formed. Sharing potential attack vectors, compromised infrastructure, new malware variants and cracked tools such as Cobalt Strike aids in evolving the whole collective to increase their capabilities.
As the threat landscape continues to change alongside global events affecting geopolitics, there will likely be a higher level of threat actor unification through larger collectives.
Receive our latest cyber intelligence insights delivered directly to your inbox
Simply complete the form to subscribe to our newsletter, ensuring you stay informed about the latest cyber intelligence insights and news.
